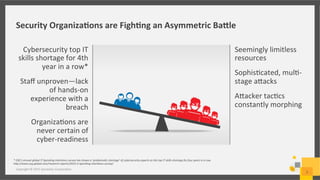
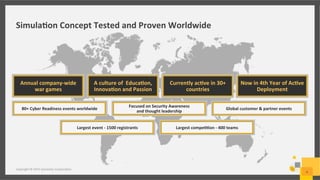
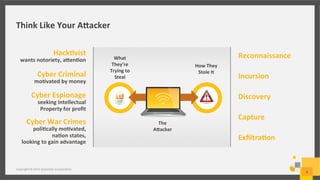
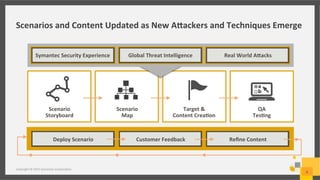
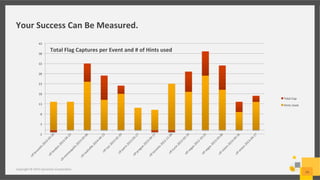
This document discusses a cyber security simulation tool developed by Symantec Corporation to help organizations strengthen their cyber readiness. The simulation provides a cloud-based, virtual training experience that simulates multi-staged attack scenarios. It allows users to assume the identity of attackers to learn their tactics. The simulation has been tested worldwide over 4 years with over 80 events. It assesses user skills and identifies gaps to guide development programs. The tool and its scenarios are continuously updated based on the latest global threat intelligence and real world attacks.