Embed presentation
Download to read offline







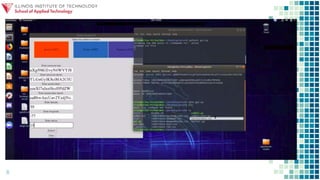
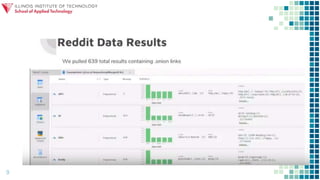
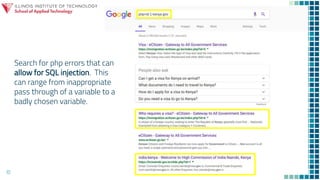
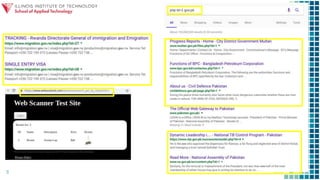



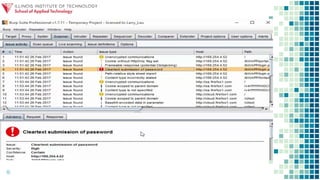
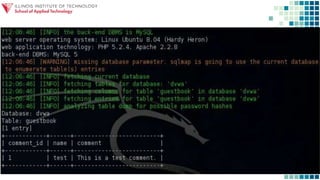






The document discusses gaining control of a situation through intelligence gathering and search techniques in order to find vulnerabilities that can be exploited to perform unparalleled events. It explores controlling the landscape through applying intelligence operations, information warfare, data science, and cybersecurity to search for and sample applications that allow one to exploit and destroy through techniques like searching for PHP errors that enable SQL injection. The session aims to explore this landscape and applications of control, search, exploit, and destroy.





















