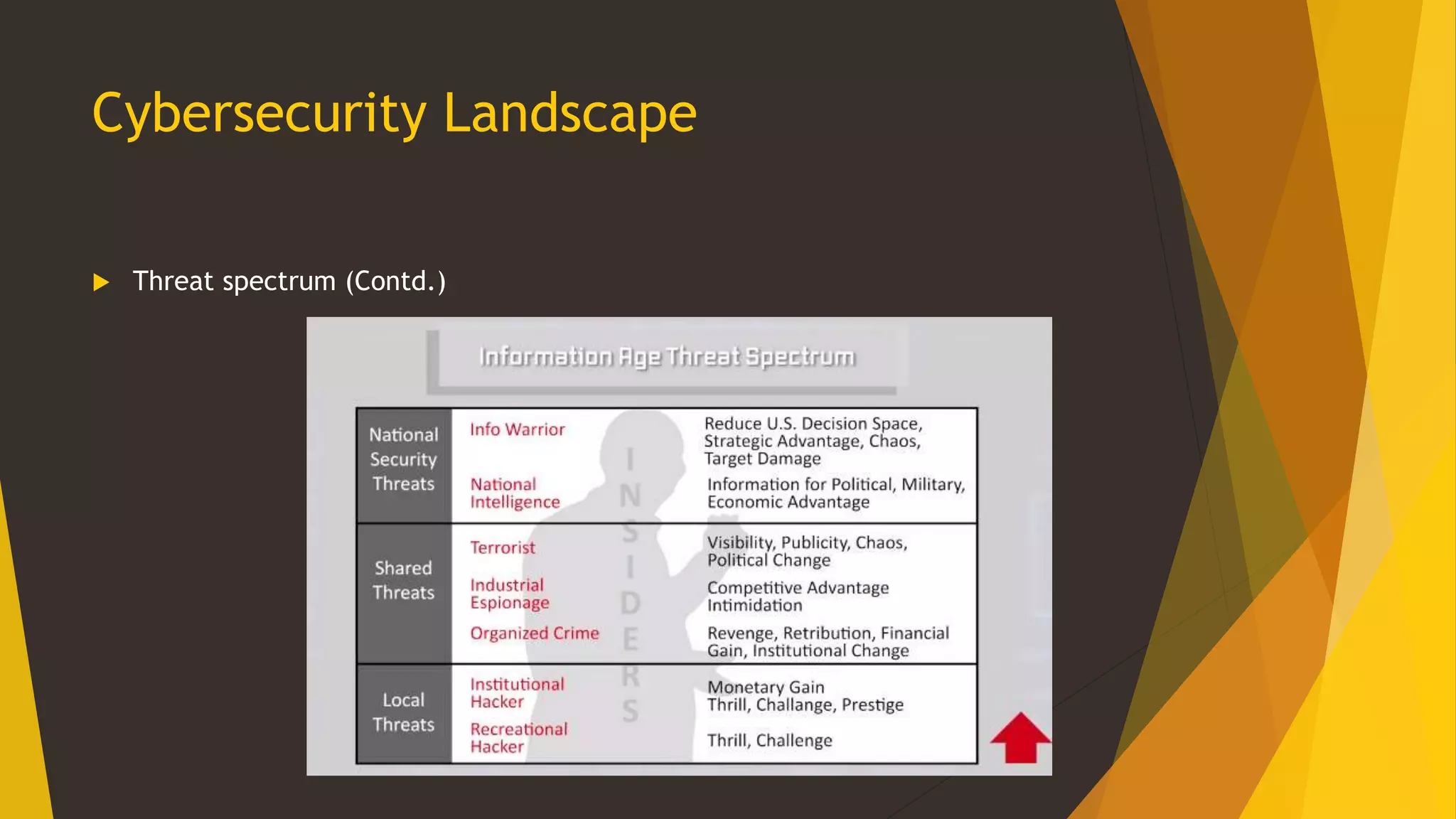
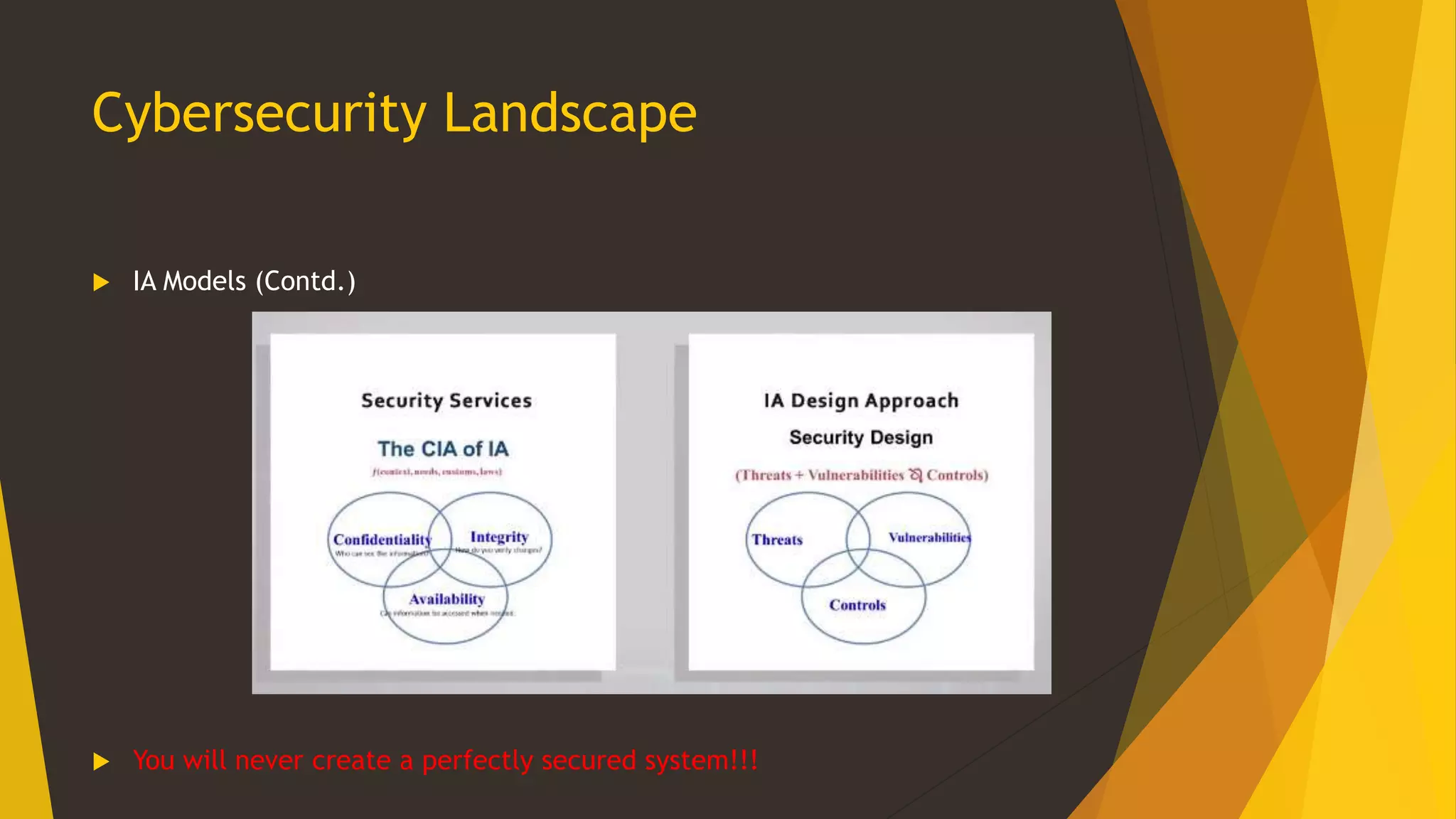
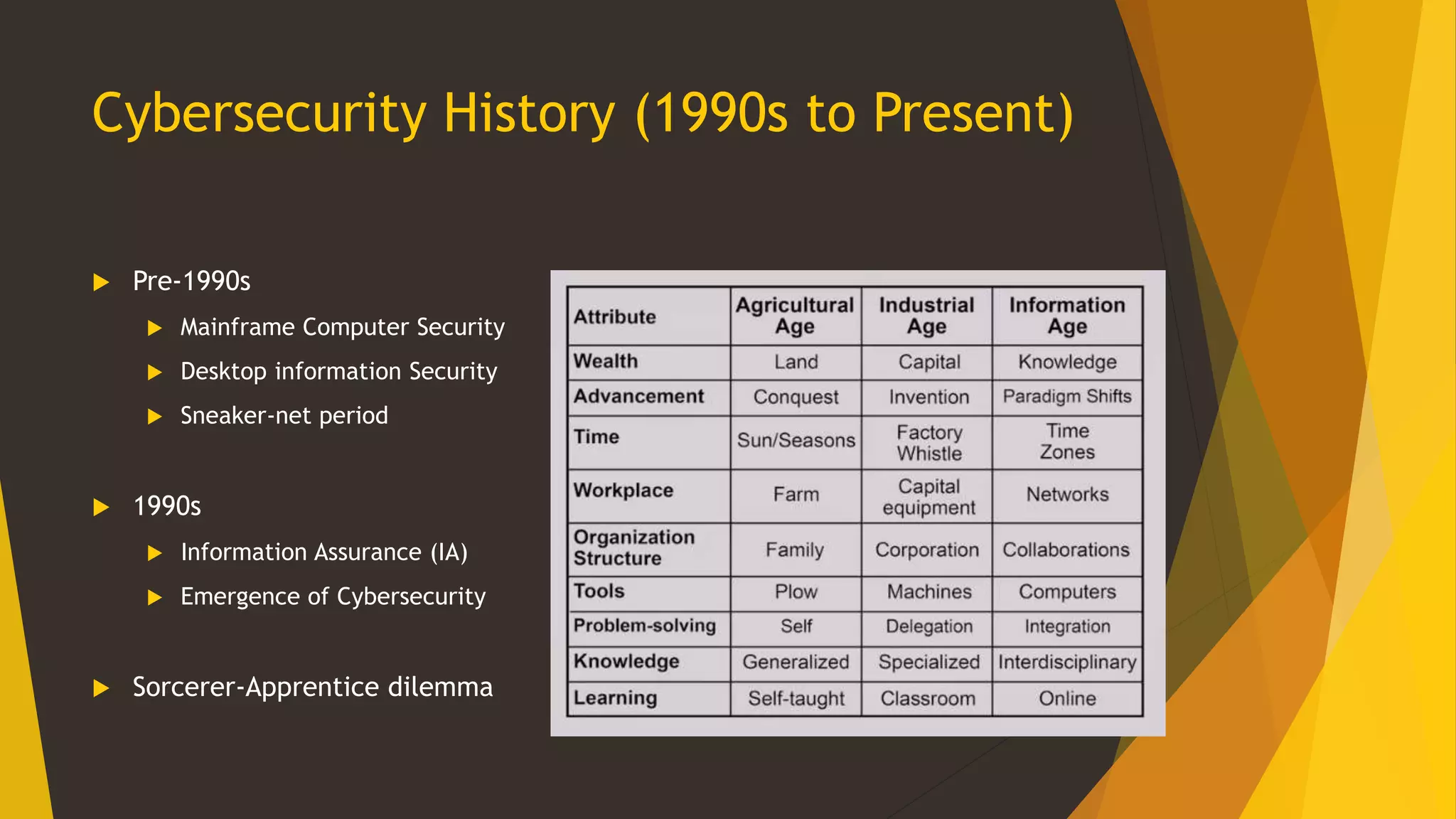
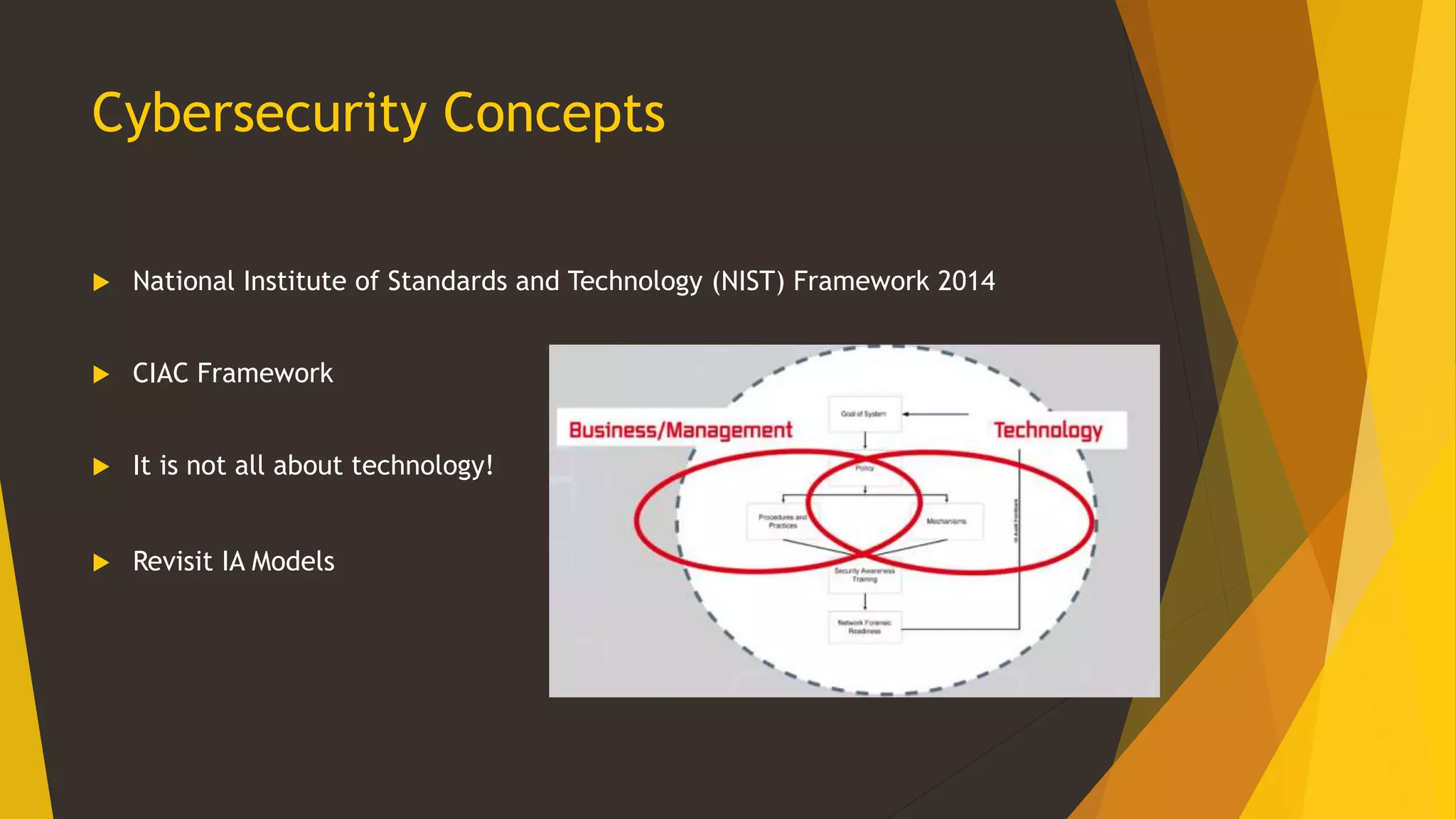
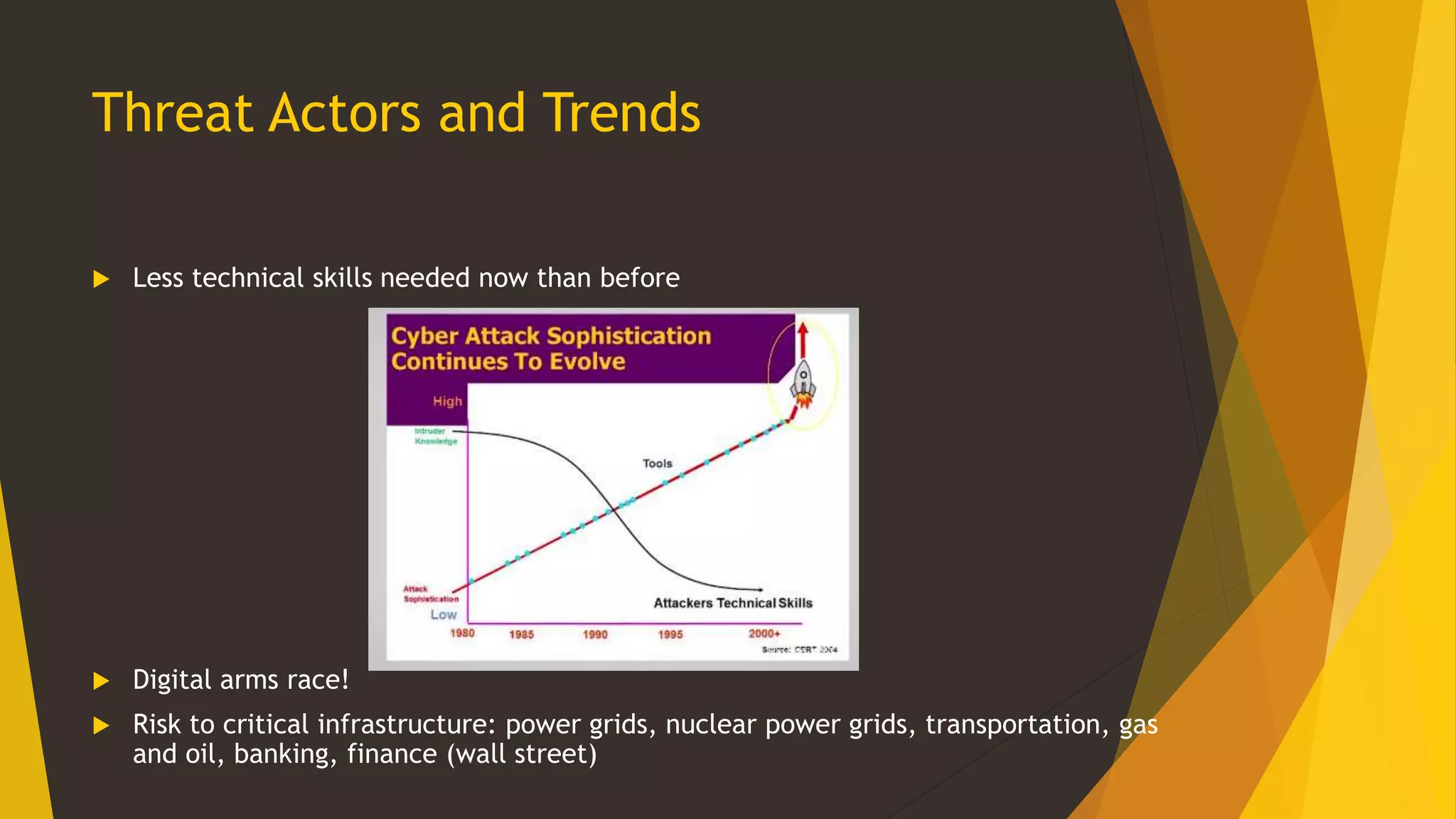
This document provides an overview of cybersecurity, including its history from the 1990s to present. It discusses cybersecurity landscapes, concepts, education, international and US perspectives, legal issues, and threat actors and trends. The key topics covered include the emergence of cybersecurity as a field, different frameworks for cybersecurity including those from NIST and CIAC, the importance of cybersecurity education and standardization, cyber attacks posing risks to critical infrastructure, and the challenges of applying law to this evolving domain across international boundaries.