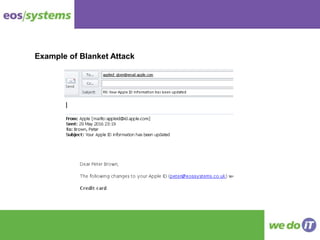
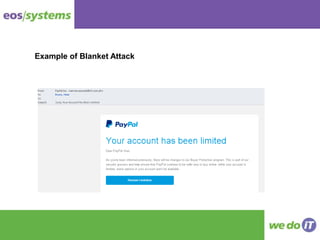
The document covers key aspects of cyber crime, including its definition, statistics, and the prevalence of ransomware. It outlines the methods of ransomware infection, removal challenges, and prevention strategies, emphasizing the importance of education and backups. Additionally, it discusses various types of hacking and phishing attacks, highlighting the need for user awareness to protect against cyber threats.