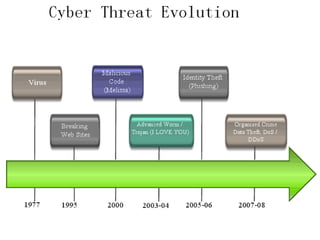
Cybercrime involves using computers or the internet to steal identities or import illegal programs. The first recorded cybercrime took place in 1820. There are different types of cybercrimes such as hacking, denial of service attacks, computer viruses, and software piracy. Cybercrimes also include using computers to attack other systems, commit real-world crimes, or steal proprietary information. Common cyber attacks include financial fraud, sabotage of networks, theft of data, and unauthorized access. Internet security aims to establish rules to protect against such attacks by using antivirus software, firewalls, and updating security settings regularly.