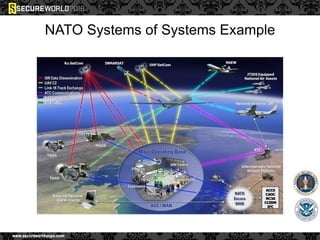
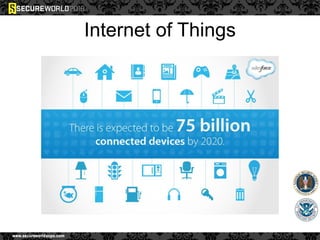
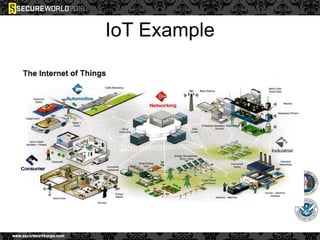
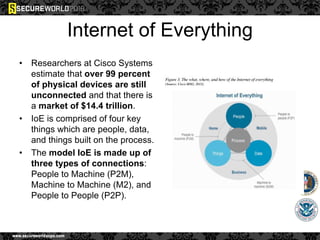
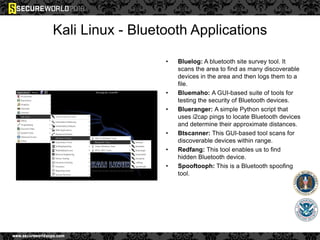
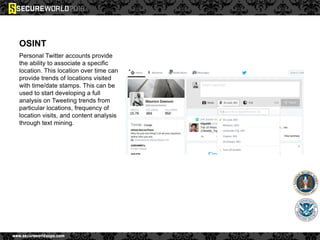
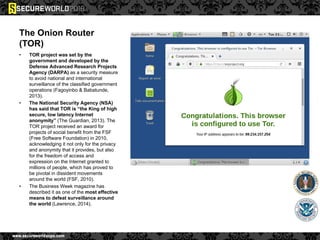
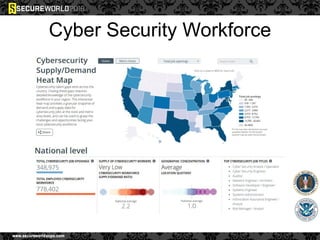
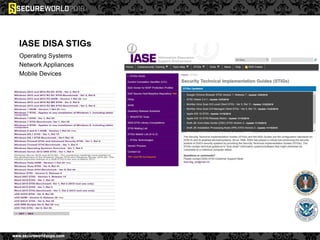
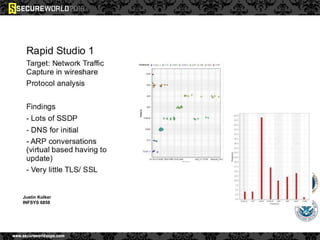
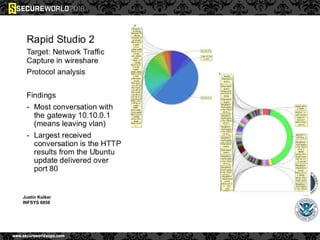
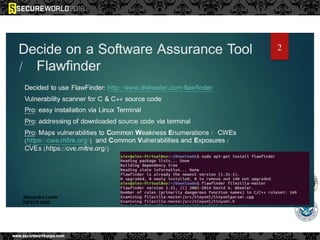
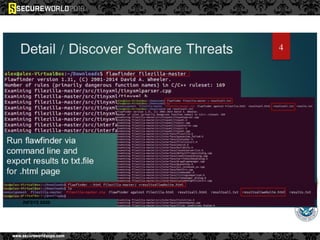
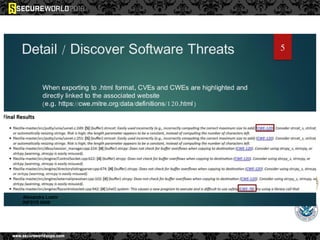
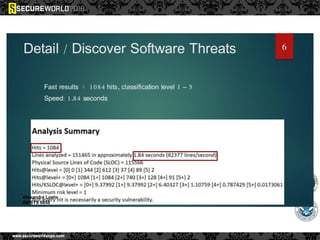
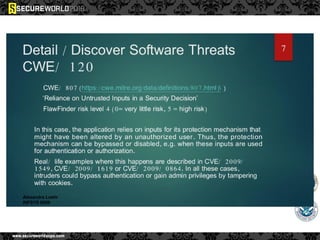
Dr. Maurice Dawson discusses security solutions for hyperconnectivity and the Internet of Things, highlighting the risks of interconnectivity that make devices susceptible to cyber-attacks. He explains key vulnerabilities associated with mobile devices and the implications of mass surveillance on privacy, particularly in the context of tools like the Tor network. The presentation emphasizes the need for effective countermeasures against cyber threats while addressing the ethical concerns surrounding anonymity and government surveillance.