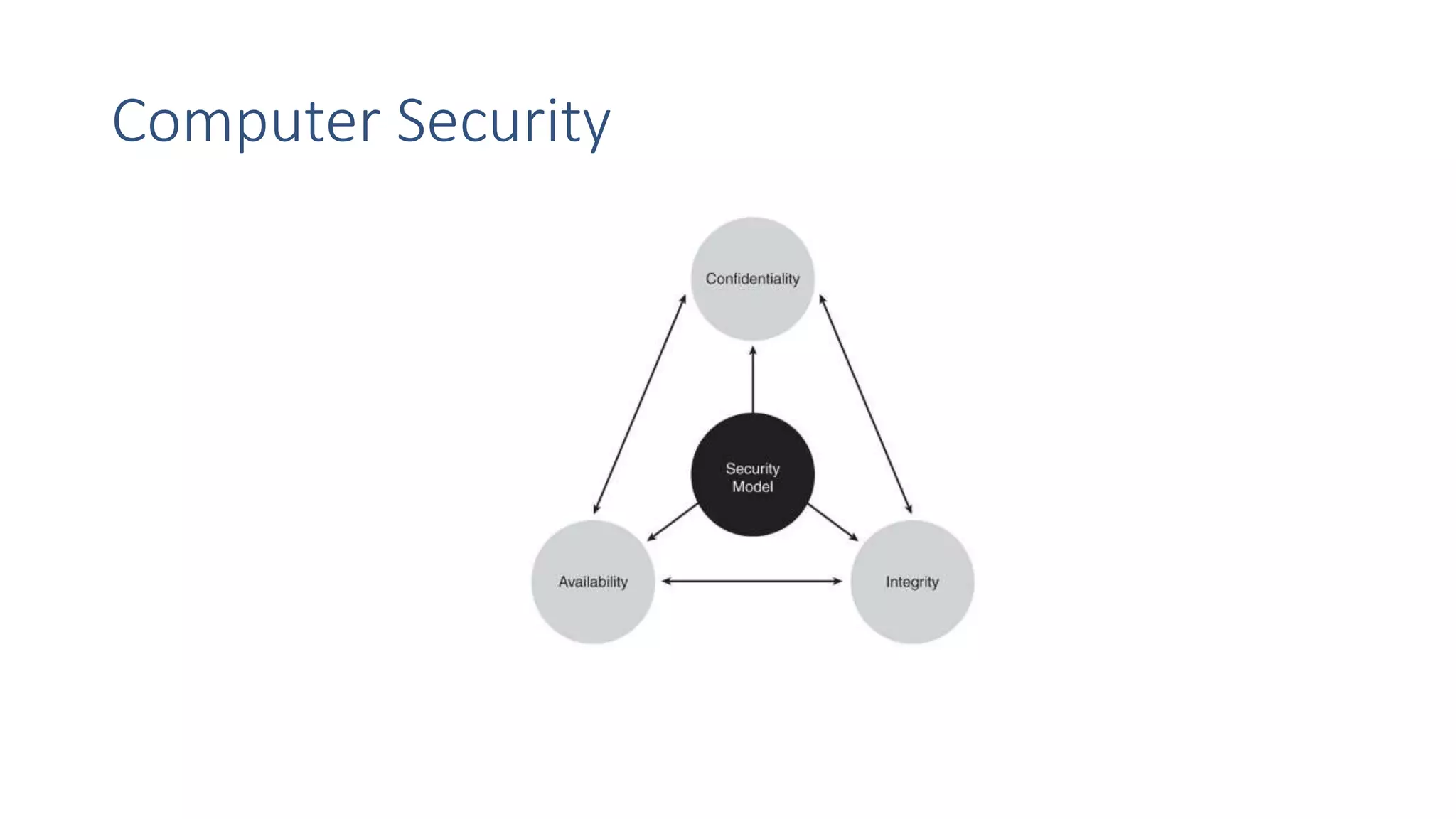
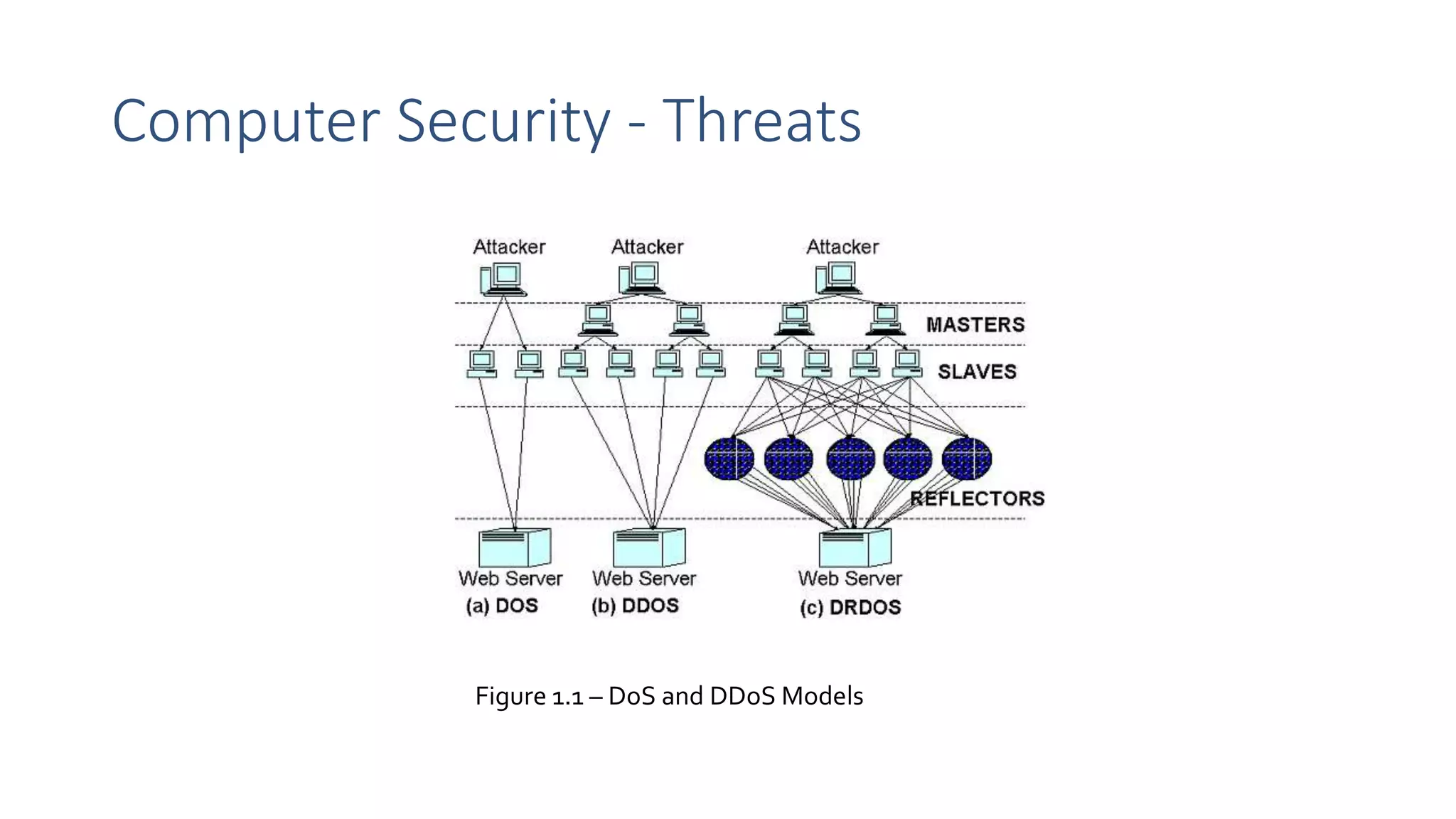
The document discusses the critical need for cybersecurity in light of the increasing complexity and interconnectivity of IT systems, which present significant challenges and vulnerabilities. It highlights the evolving nature of cyber threats, especially against public online services, and the growth of cybercrime markets. Additionally, it emphasizes the importance of basic cybersecurity principles such as confidentiality, integrity, and availability, while outlining various categories and methods of cybercrime.