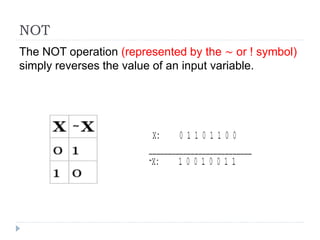
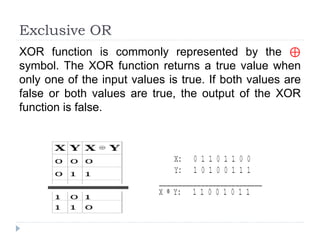
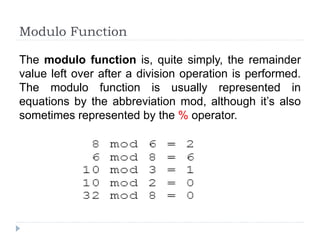
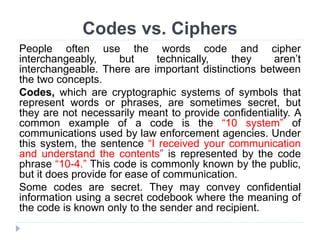
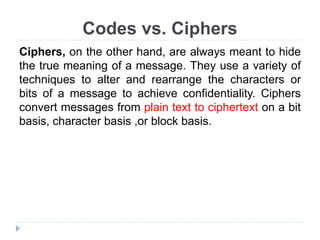
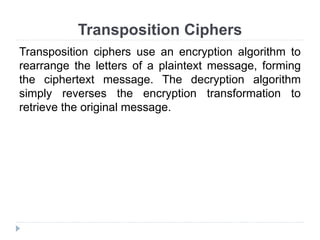
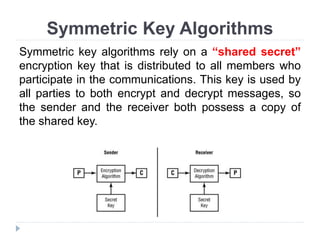
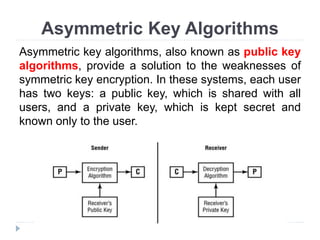
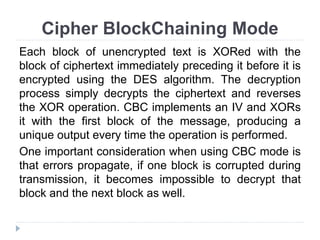
This document provides an overview of cryptography, focusing on symmetric key algorithms and their historical context, including systems like the Caesar cipher. It outlines fundamental goals of cryptography such as confidentiality, integrity, authentication, and nonrepudiation, along with key concepts such as keys, algorithms, and types of ciphers like transposition and substitution ciphers. Additionally, it discusses mathematical foundations, including boolean operations and one-way functions, that underpin encryption processes.