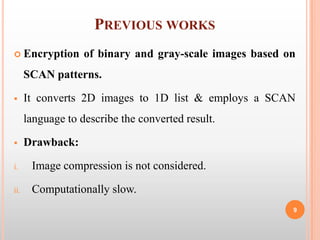
The document describes a modified AES key expansion algorithm for image encryption and decryption. It discusses basics of cryptography and image encryption. It introduces AES and describes the standard AES key expansion process. It then presents a modified AES key expansion algorithm tailored for images where the keys are expanded based on image pixel count, Rcon values are derived from the initial key, and the S-box is shifted based on the initial key. It analyzes the proposed algorithm and shows it offers high encryption quality with minimal time compared to previous techniques.














![2. Shift Rows:
It will not change the values, but will just change their order.
It does a left circular shift to each row as below:
Row 0 Shift 0; Row 1 Shift 1; Row 2 Shift 2;
Row 3 Shift 3;
State[0,0] State[0,1] State[0,2] State[0,3] State[0,0] State[0,1] State[0,2] State[0,3]
State[1,0] State[1,1] State[1,2] State[1,3] State[1,1] State[1,2] State[1,3] State[1,0]
State[2,0] State[2,1] State[2,2] State[2,3] State[2,2] State[2,3] State[2,0] State[2,1]
State[3,0] State[3,1] State[3,2] State[3,3] State[3,3] State[3,0] State[3,1] State[3,2]
18](https://image.slidesharecdn.com/imageencryptionusingaeskeyexpansion-130319103134-phpapp02/85/Image-encryption-using-aes-key-expansion-18-320.jpg)



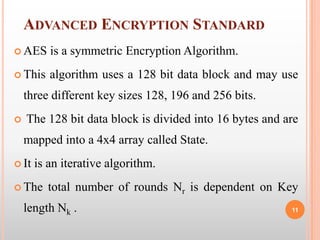
![b. KEY EXPANSION
This routine expands the initial key to 4*(Nr+1) words.
For Nk=4words, Nr=10; this routine creates 44 words.
Process is as follows:
First 4 words of round key are made from initial cipher key,
i.e., w[0]= k[0:3] ; w[1]=k[0:7] and so on.
The rest of the words (wi for i=4 to 43) are derived as follows:
if (i mod 4)!=0 then, wi = wi-1+ wi-4 ;
else if (i mod 4)=0 then, temp = w[i-1];
temp = Sub Word (Rot Word (temp)) + Rcon [i/4]; 22
w[i] = w[i-4] + temp;](https://image.slidesharecdn.com/imageencryptionusingaeskeyexpansion-130319103134-phpapp02/85/Image-encryption-using-aes-key-expansion-22-320.jpg)
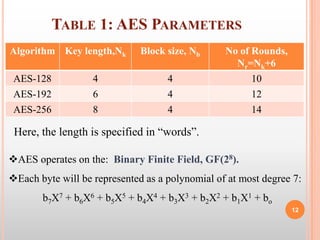
![operations performed to obtain wi when (i mod 4) = 0
i. RotWord: performs one byte circular left shift on wi-1.
ii. SubWord: performs a byte substitution on each byte of its
input word, using the S-box.
iii. The result of step (i) and (ii) is XORed with a round
constant Rcon[j].
Rcon[j]={RC[j],0,0,0},where RC[j]=2*RC[j-1].
j 1 2 3 4 5 6 7 8 9 10
RC[j] 01 02 04 08 10 20 40 80 1B 36
Table 2 : RC values in hex 23](https://image.slidesharecdn.com/imageencryptionusingaeskeyexpansion-130319103134-phpapp02/85/Image-encryption-using-aes-key-expansion-23-320.jpg)

![The above changes in the algorithm can be represented as:
Key Expansion for the image :
Consider a plain image of size mxn. We encrypt a set of
16 pixels (128 bits) using 2 round keys.
∴ No of keys to Encrypt the whole image N=2*{(m*n)/16}.
Formation of Rcon values :
Rcon[0]=key[12:15]; Rcon[1]=key[4:7];
Rcon [2]=key[0 : 3]; Rcon [3]=key[8:11];
25](https://image.slidesharecdn.com/imageencryptionusingaeskeyexpansion-130319103134-phpapp02/85/Image-encryption-using-aes-key-expansion-25-320.jpg)
![ Using Inverse S-Box for key expansion:
The „temp‟ value used in the algorithm is formed as follows,
temp = SubWord(RotWord(temp)) + InvSubWord(Rcon[i/4]);
Shifting of S-box and Inverse S-box:
Sbox_offset = sum(key[0:15])mod256;
Inv_Sbox_offset = (sum(key[0:15])*mean(key[0:15]))mod256;
26](https://image.slidesharecdn.com/imageencryptionusingaeskeyexpansion-130319103134-phpapp02/85/Image-encryption-using-aes-key-expansion-26-320.jpg)








![REFERENCES
[1] B.Subramanyan, Vivek.M.Chhabria, T.G.Sankar babu, Image Encryption
Based On AES Key Expansion, 2011 Second International Conference on
Emerging Applications of Information Technology, page 217-220.
[2] N.J.Bourbakis , C.Alexopoulos, Picture data encryption using SCAN
patterns. Pattern Recognition 256 1992 pp567 -581.
[3] Mitra, Y. V. Subba Rao, and S. R. M. Prasanna, A new image encryption
approach using combinational permutation techniques, International Journal
of Computer Science, vol. 1, no. 2 , pp. 1306- 4428, 2006.
[4] http://en.wikipedia.org/wiki/Rijndael_S-box.
[5] http://csrc.nist.gov/publications/fips/fips197/fips-197.pdf 35](https://image.slidesharecdn.com/imageencryptionusingaeskeyexpansion-130319103134-phpapp02/85/Image-encryption-using-aes-key-expansion-35-320.jpg)
