Embed presentation
Downloaded 36 times



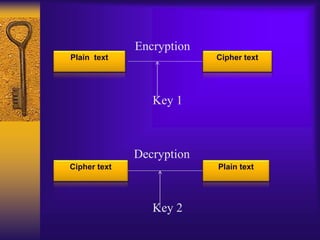

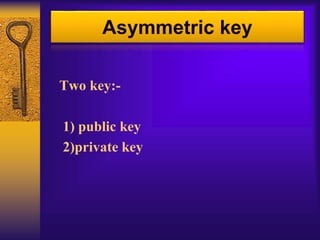
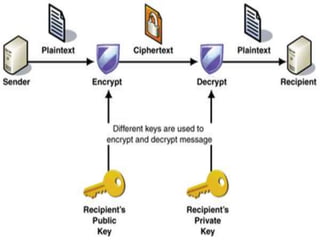





Asymmetric key cryptography uses two keys: a public key and a private key. The public key can encrypt messages but only the private key can decrypt them. This allows for convenience, message authentication, detection of tampering, and non-repudiation. However, public keys need authentication, it is slower than symmetric key cryptography, uses more computer resources, a security compromise could affect many users, and loss of the private key would be irreparable.










