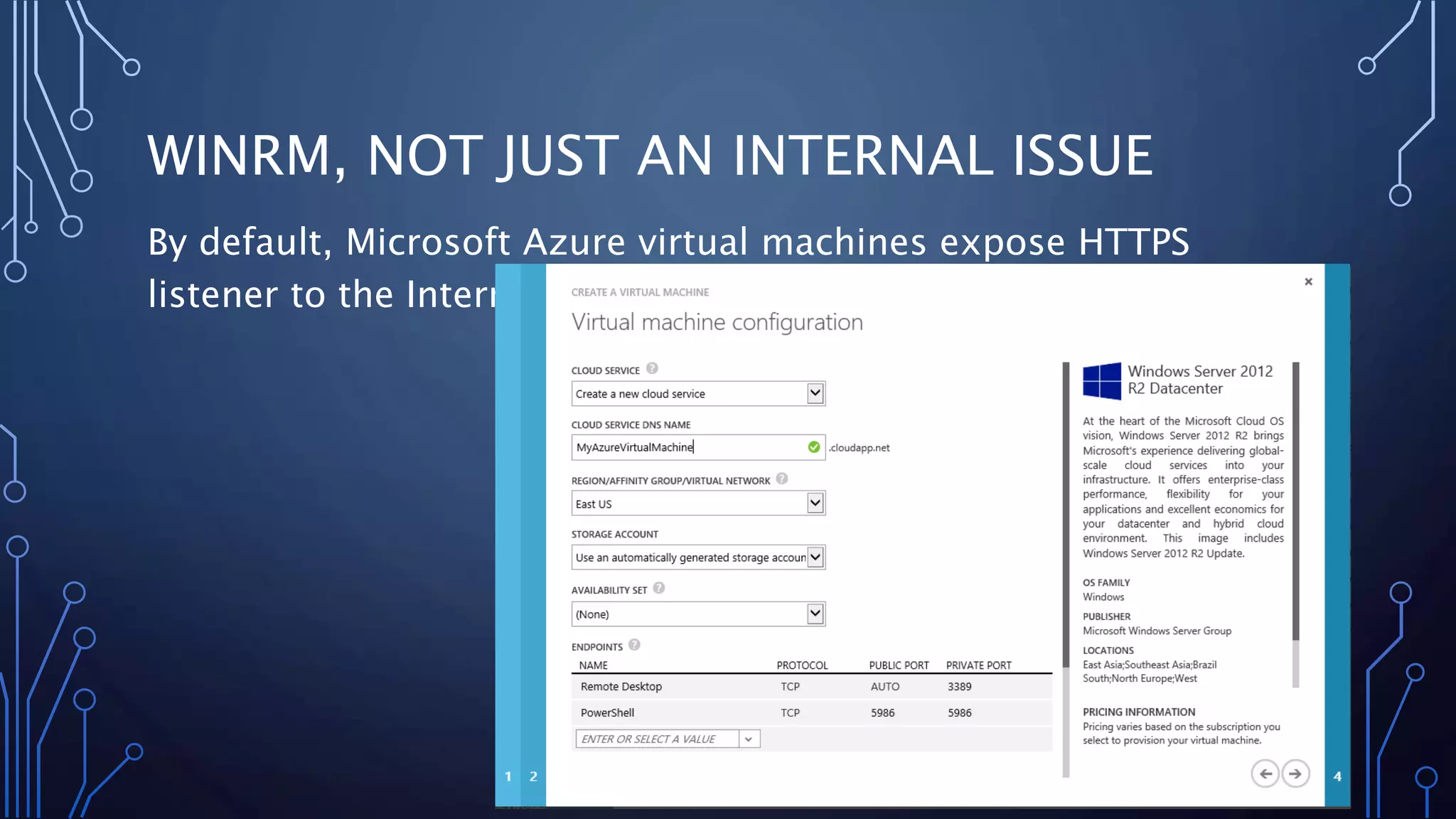
The document discusses the use of PowerShell as an attack platform, detailing its advantages for lateral movement and remote execution in corporate environments. It covers real-world PowerShell malware examples, such as 'Powerworm' and 'Poshcoder', and describes techniques for bypassing PowerShell security features like execution policies. The presentation also highlights defense mechanisms against PowerShell-based attacks, including application whitelisting and changes to Windows Firewall settings.