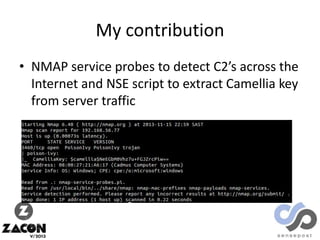
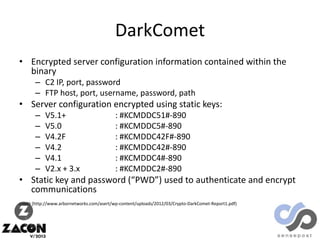
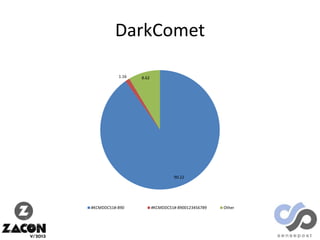
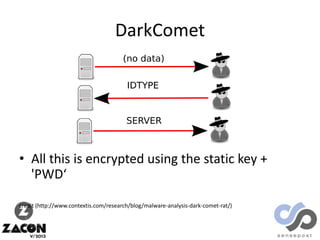
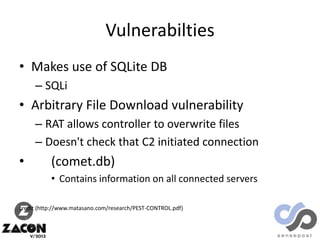
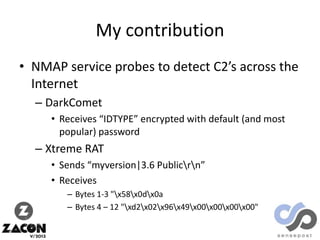
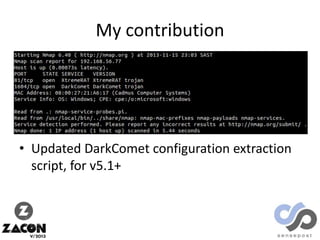
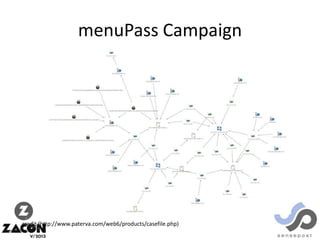
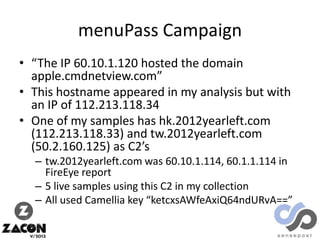
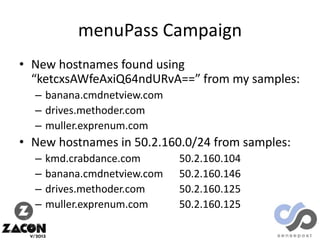
The document discusses research on two remote access Trojans (RATs), Poison Ivy and DarkComet, detailing methods for analysis, sample collection, and vulnerabilities. It highlights the use of tools like Cuckoo Sandbox and VirusTotal for malware analysis and references specific campaigns targeting defense contractors. The author encourages defenders to leverage these findings to improve security and investigate attacks.