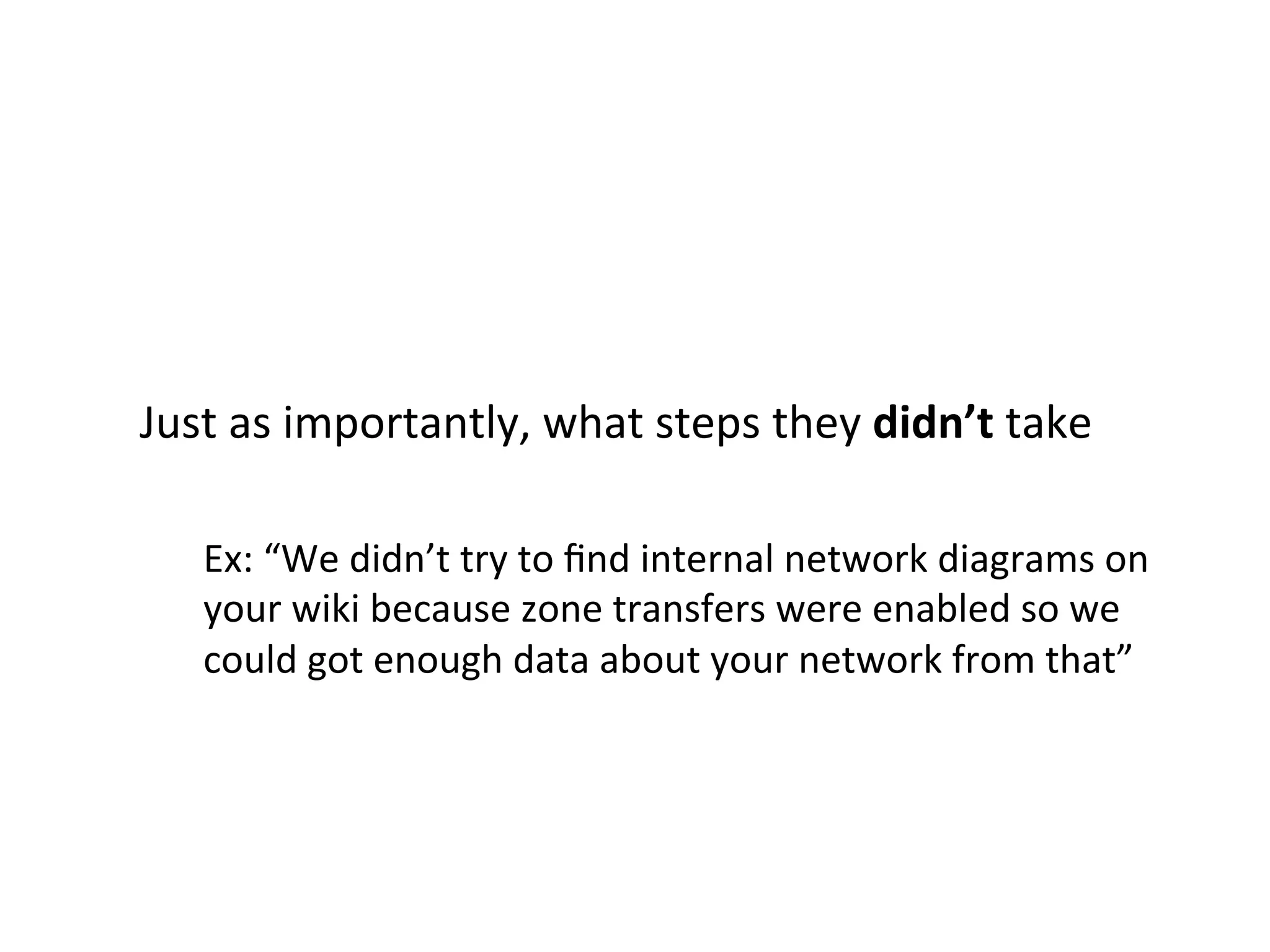
This document provides an overview of an "attack-driven defense" approach presented by the co-founder and CSO of Signal Sciences. The summary focuses on three key points:
1) The approach focuses on building defenses around real-world attack patterns by instrumenting detection mechanisms around the initial compromise, persistence/C2, and lateral movement stages of an attack.
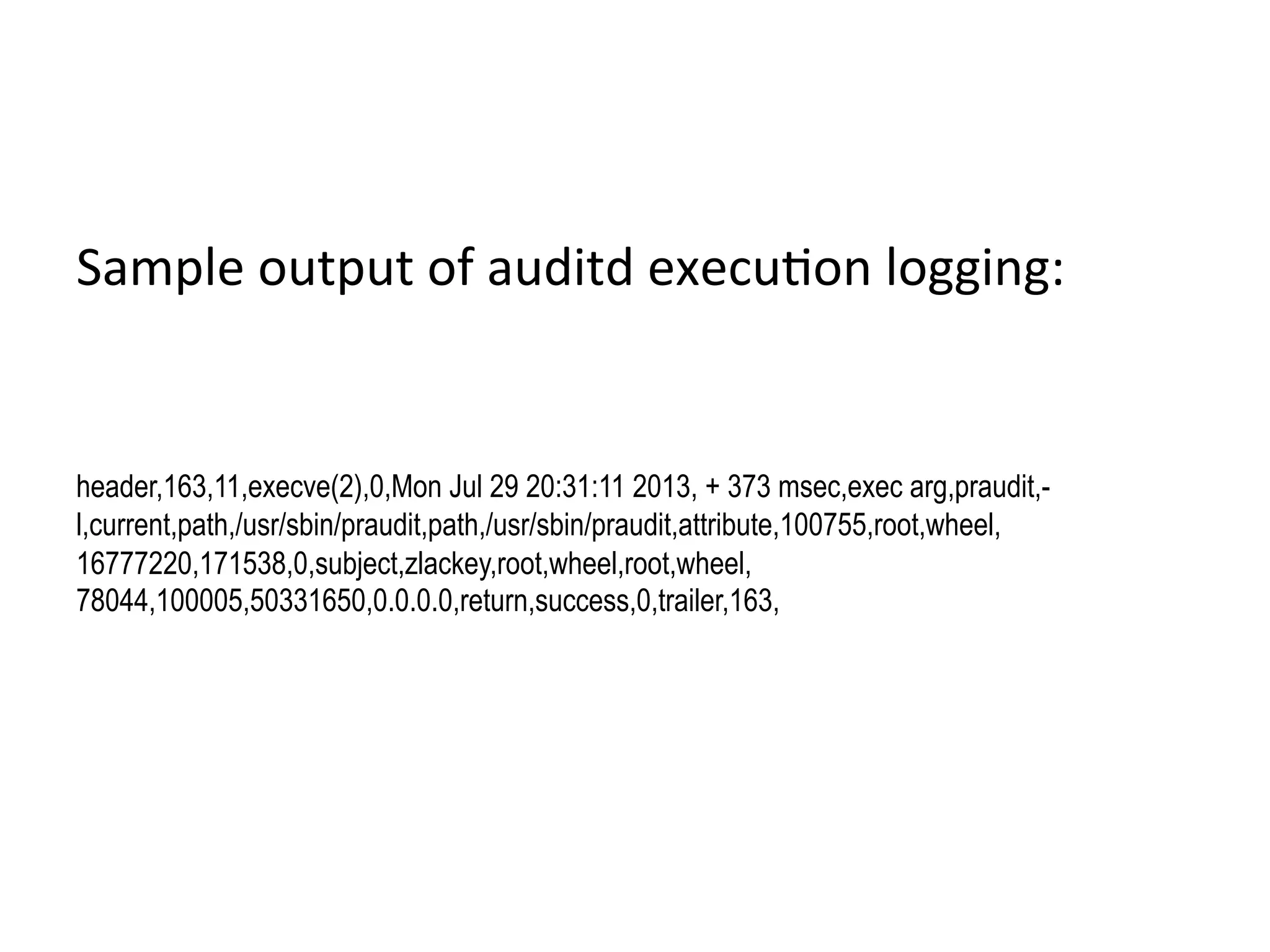
2) Detection involves analyzing endpoint command logs to identify anomalous commands for non-technical users or unique command combinations/bursts for technical users. Common attack patterns are also flagged.
3) A host-based intrusion detection system called "Tripyarn" is presented, which aims to alert on common host-level persistence mechanisms used by attackers



































































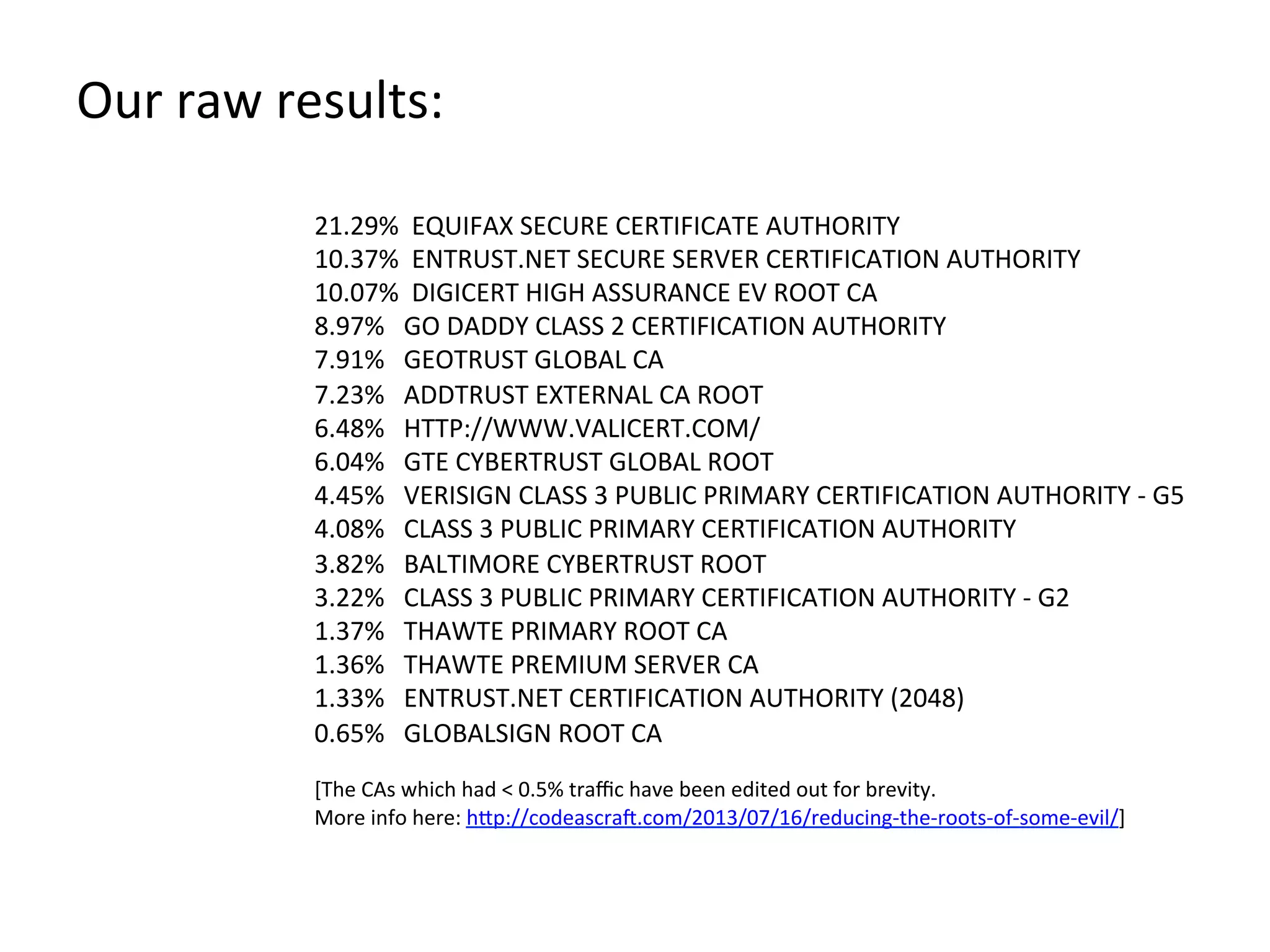
![21.29%
EQUIFAX
SECURE
CERTIFICATE
AUTHORITY
10.37%
ENTRUST.NET
SECURE
SERVER
CERTIFICATION
AUTHORITY
10.07%
DIGICERT
HIGH
ASSURANCE
EV
ROOT
CA
8.97%
GO
DADDY
CLASS
2
CERTIFICATION
AUTHORITY
7.91%
GEOTRUST
GLOBAL
CA
7.23%
ADDTRUST
EXTERNAL
CA
ROOT
6.48%
HTTP://WWW.VALICERT.COM/
6.04%
GTE
CYBERTRUST
GLOBAL
ROOT
4.45%
VERISIGN
CLASS
3
PUBLIC
PRIMARY
CERTIFICATION
AUTHORITY
-‐
G5
4.08%
CLASS
3
PUBLIC
PRIMARY
CERTIFICATION
AUTHORITY
3.82%
BALTIMORE
CYBERTRUST
ROOT
3.22%
CLASS
3
PUBLIC
PRIMARY
CERTIFICATION
AUTHORITY
-‐
G2
1.37%
THAWTE
PRIMARY
ROOT
CA
1.36%
THAWTE
PREMIUM
SERVER
CA
1.33%
ENTRUST.NET
CERTIFICATION
AUTHORITY
(2048)
0.65%
GLOBALSIGN
ROOT
CA
[The
CAs
which
had
<
0.5%
traffic
have
been
edited
out
for
brevity.
More
info
here:
h"p://codeascraX.com/2013/07/16/reducing-‐the-‐roots-‐of-‐some-‐evil/]
Our
raw
results:](https://image.slidesharecdn.com/attackdrivendefense-130829101820-phpapp01/75/Attack-driven-defense-76-2048.jpg)