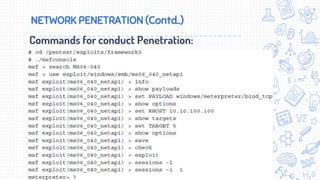
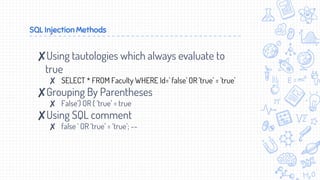
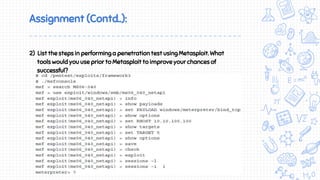
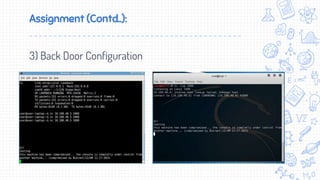
This document provides an overview of penetration testing techniques, including forms of cyber attacks like buffer overflows and SQL injection. It discusses using Metasploit and other commercial tools like Canvas to conduct network penetration testing. It also covers post-exploitation techniques such as password cracking, privilege escalation, and data exfiltration. The goal of a penetration test is to simulate a real attack to evaluate system defenses and identify vulnerabilities.