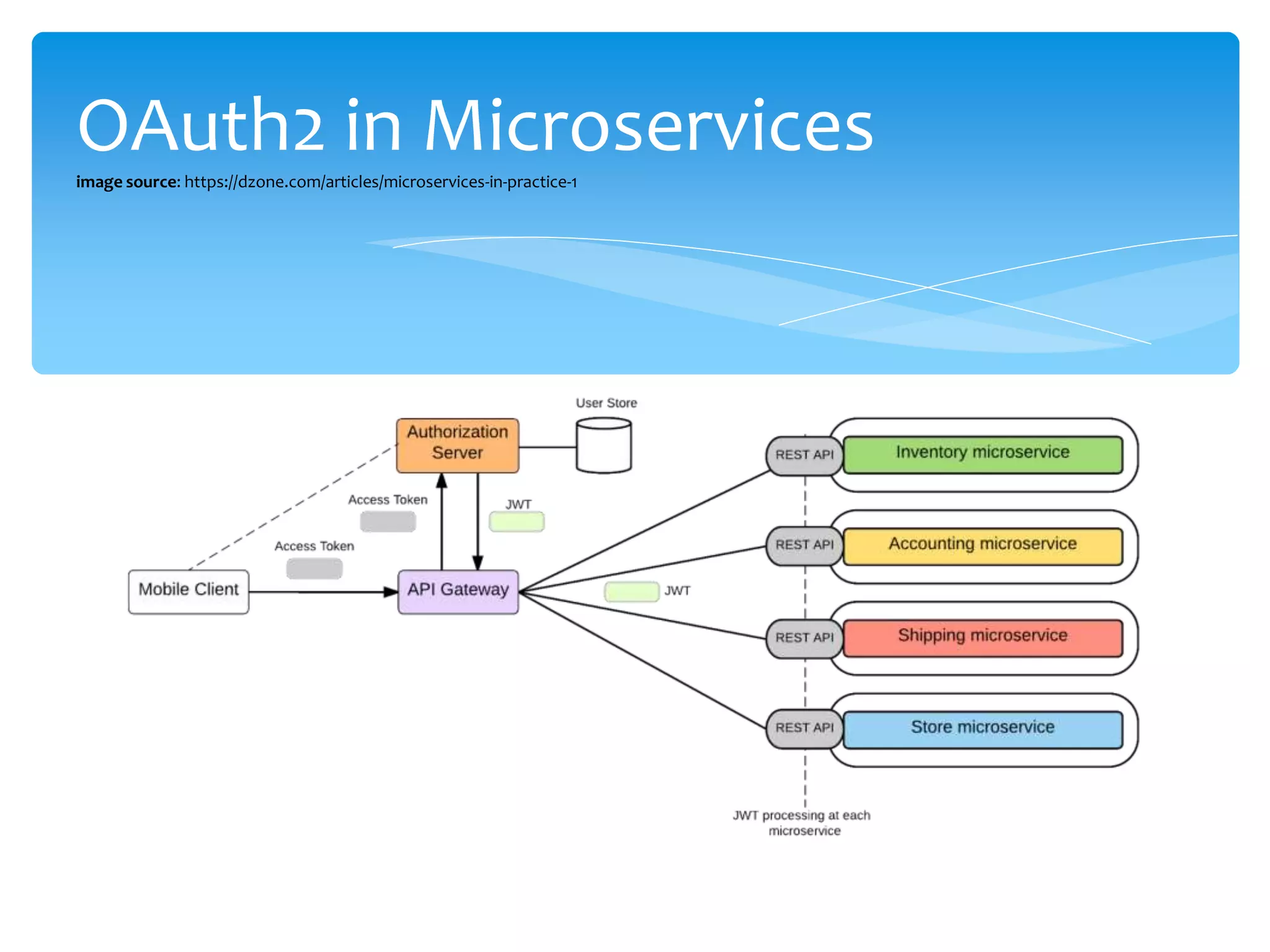
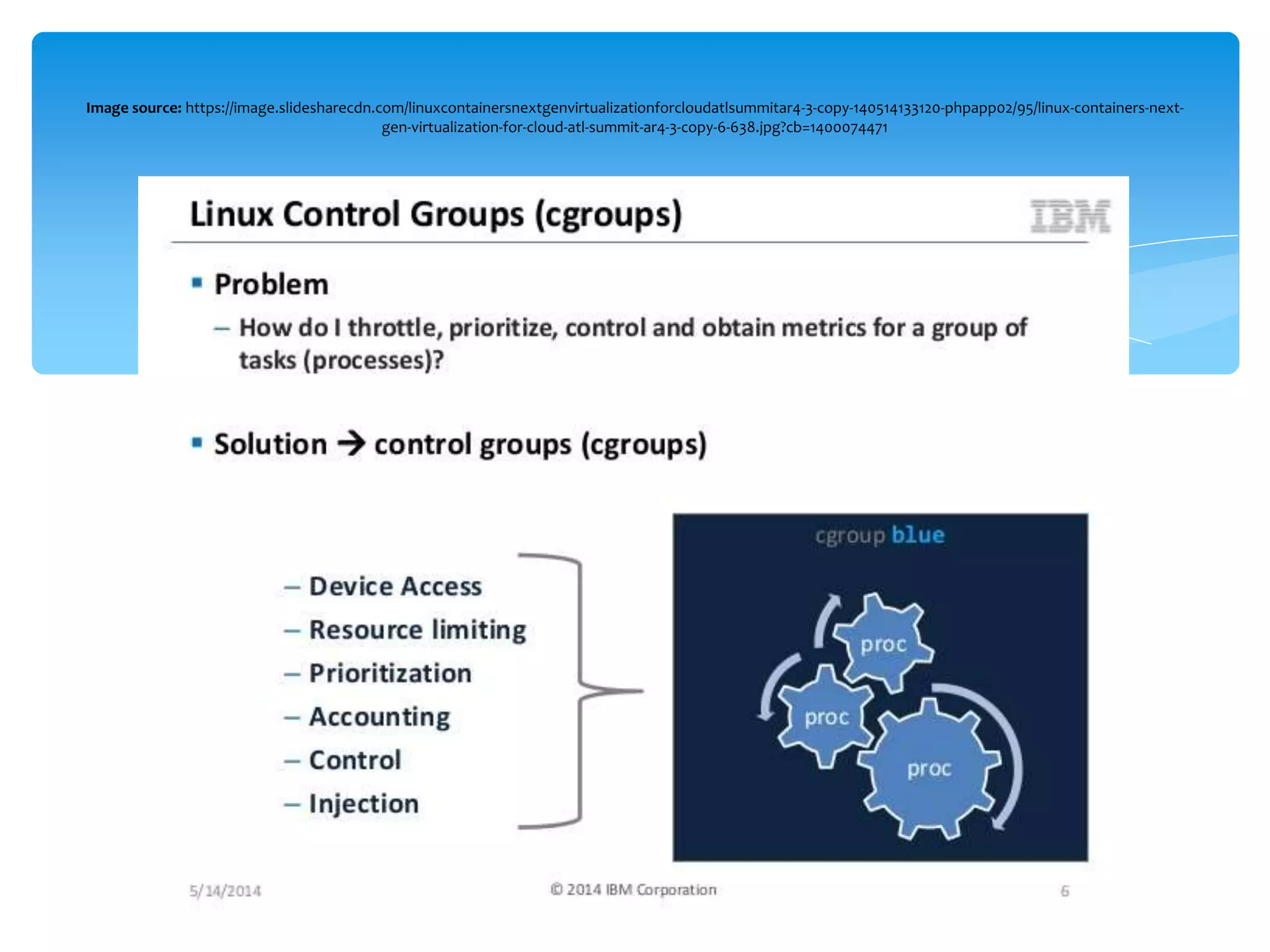
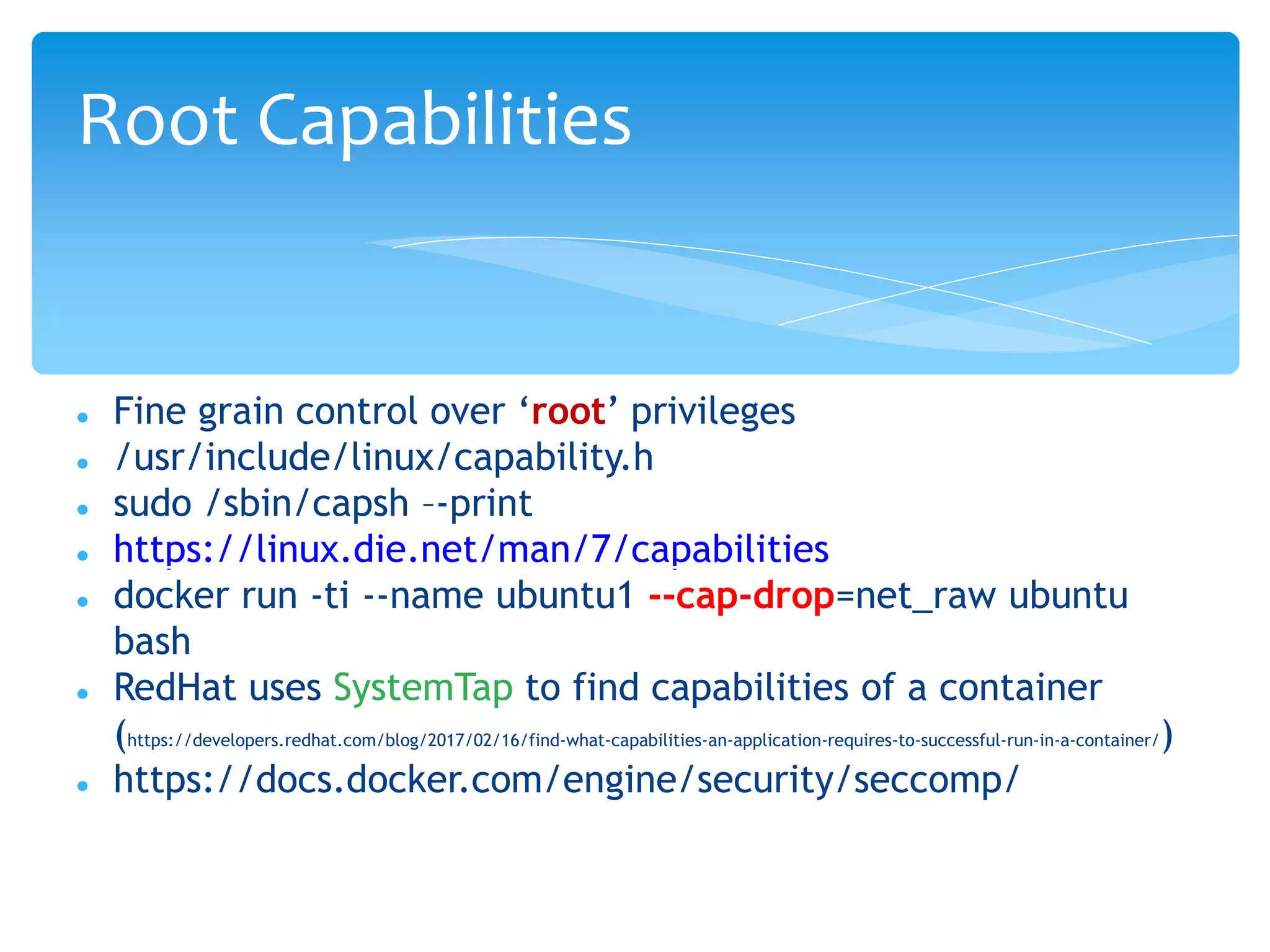
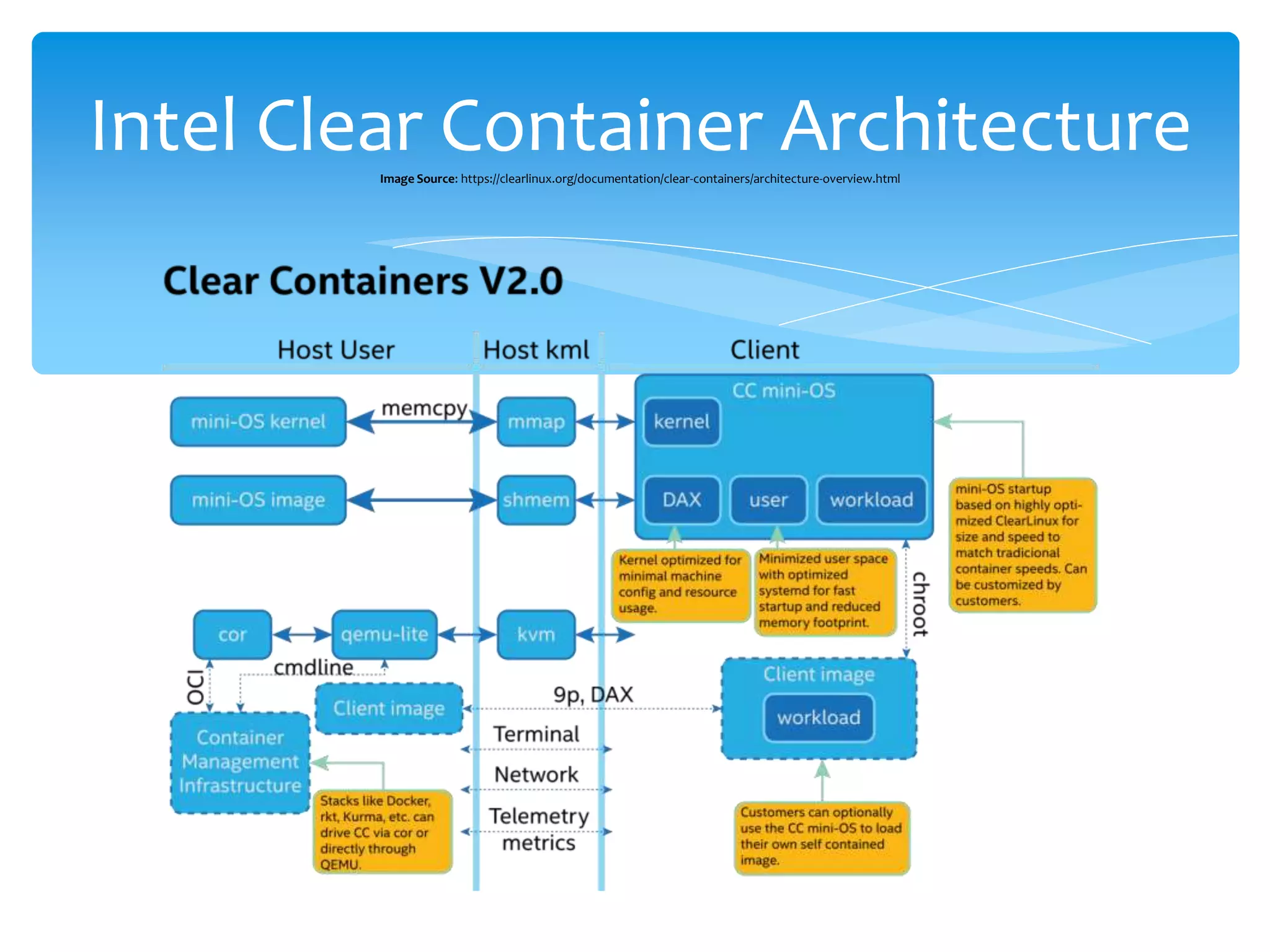
The document discusses container security, providing advantages and disadvantages of containers as well as threats. It outlines different approaches to container security including host-based methods using namespaces, control groups, and capabilities as well as container-based scanning and digital signatures. Third-party security tools are also mentioned. The document concludes with examples of using containers for microservices and network policies for protection.














![onboot:
- name: dhcpcd
image: linuxkit/dhcpcd:<hash>
command: ["/sbin/dhcpcd", "--nobackground", "-f", "/dhcpcd.conf", "-1"]
- name: wg
image: linuxkit/ip:<hash>
net: new
binds:
- /etc/wireguard:/etc/wireguard
command: ["sh", "-c", "ip link set dev wg0 up; ip address add dev wg0 192.168.2.1 peer 192.168.2.2; wg setconf wg0 /etc/wireguard/wg0.conf; wg show wg0"]
runtime:
interfaces:
- name: wg0
add: wireguard
createInRoot: true
bindNS:
net: /run/netns/wg
services:
- name: nginx
image: nginx:alpine
net: /run/netns/wg
capabilities:
- CAP_NET_BIND_SERVICE
- CAP_CHOWN
- CAP_SETUID
- CAP_SETGID
- CAP_DAC_OVERRIDE](https://image.slidesharecdn.com/containersecurity-171124073434/75/Container-security-23-2048.jpg)