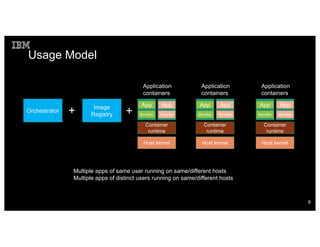
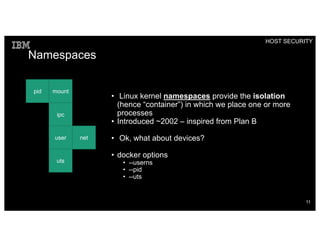
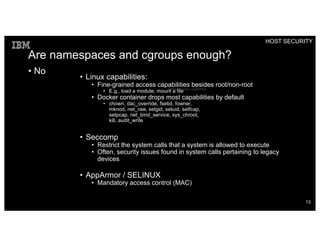
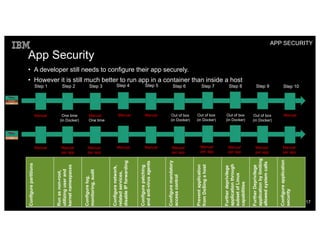
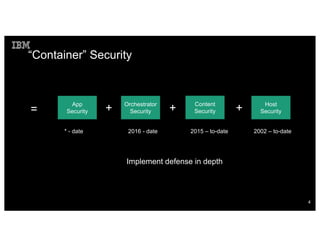
Container security involves securing the host, container content, orchestration, and applications. The document discusses how container isolation evolved over time through namespaces, cgroups, capabilities, and other Linux kernel features. It also covers securing container images, orchestrators, and applications themselves. Emerging technologies like LinuxKit, Katacontainers, and MirageOS aim to provide more lightweight and secure container environments.



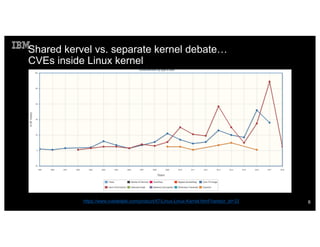
![The previous chart can be misleading…
• Gain privilege exploits in 2017: 36
• Includes CVEs in previous kernel versions
• 1 eCryptfs 3.18 or earlier
• Drivers: 5 Qualcomm drives, 2 NVIDIA, 1 USB, 1 BROADCOM, 1 GPU,
1 TTY
• KVM: 1 (that is, CVE found in kvm also)
• Not all CVEs are [easily] exploitable, but nevertheless…
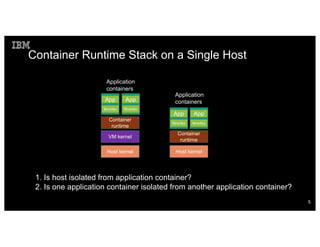
Host kernel
Container
runtime
App
Bins/libs
App
Bins/libs
Application
containers
Focus of this talk
7](https://image.slidesharecdn.com/containersecurity-2018-180515184758/85/Container-Security-7-320.jpg)