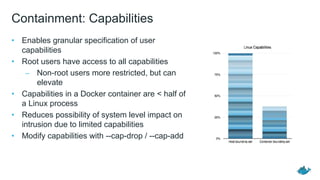
Docker provides security features to secure content, access, and platforms. It delivers integrated security through content trust, authorization and authentication, and runtime containment using cGroups, namespaces, capabilities, seccomp profiles, and Linux security modules.