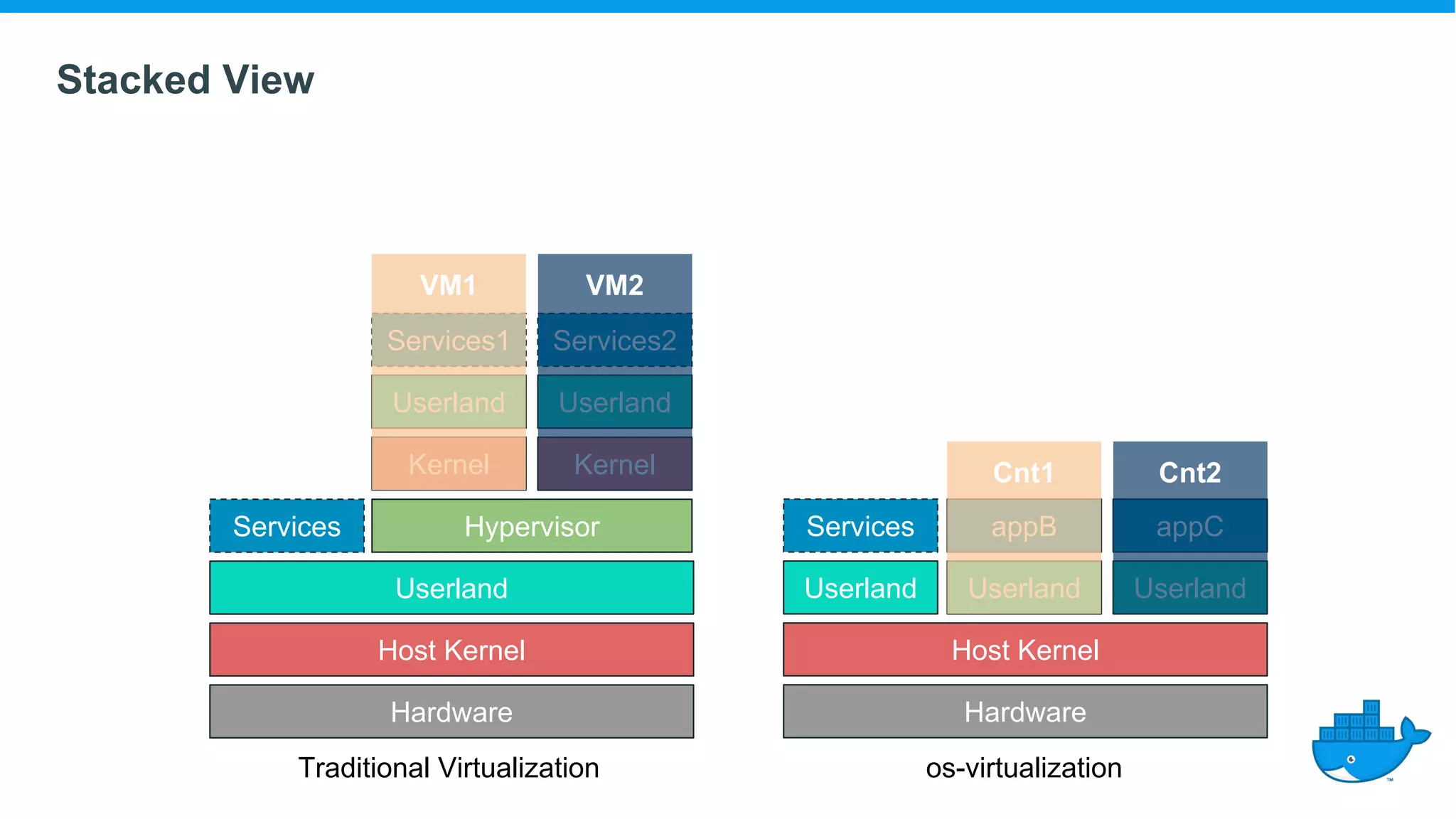
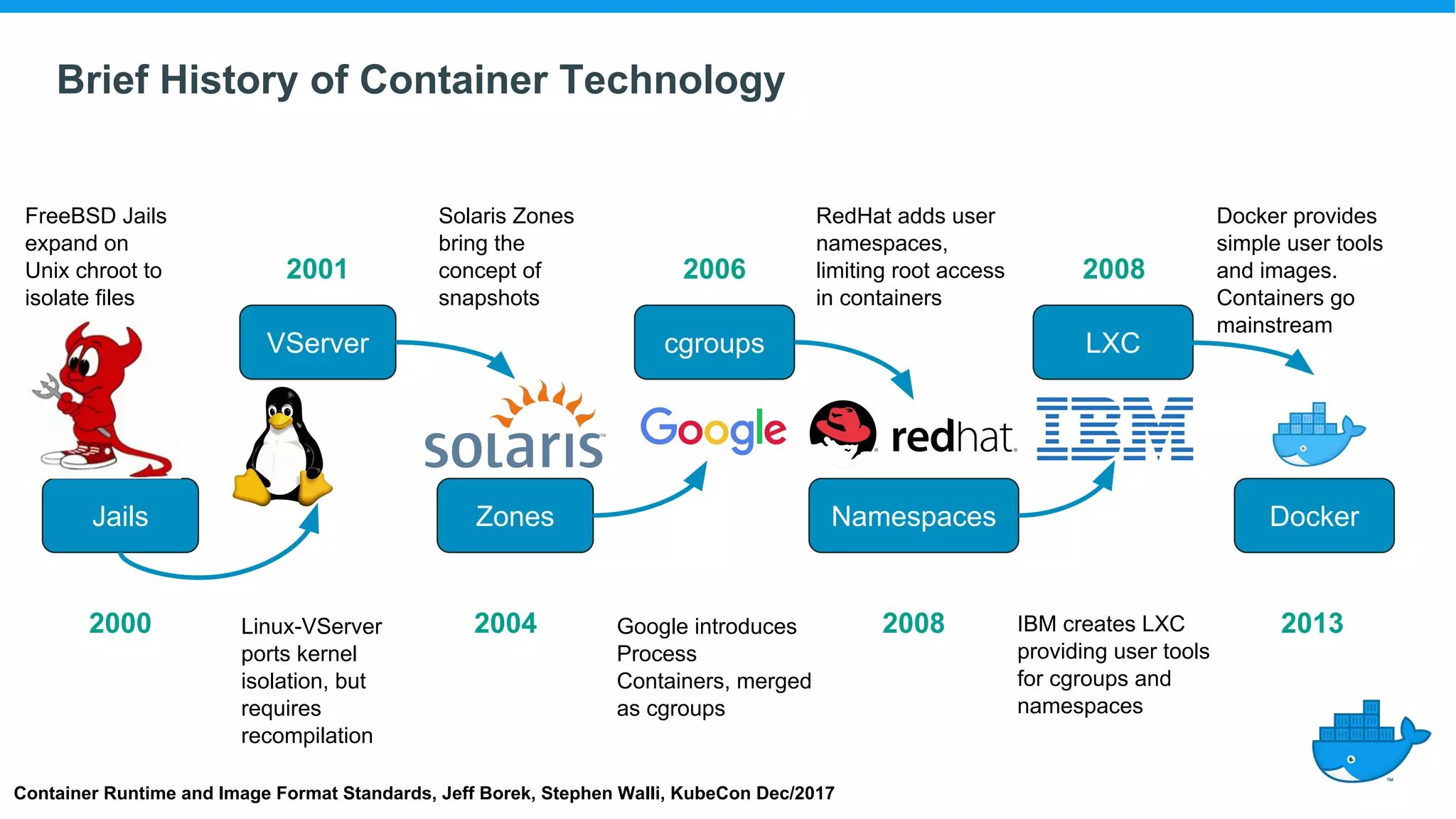
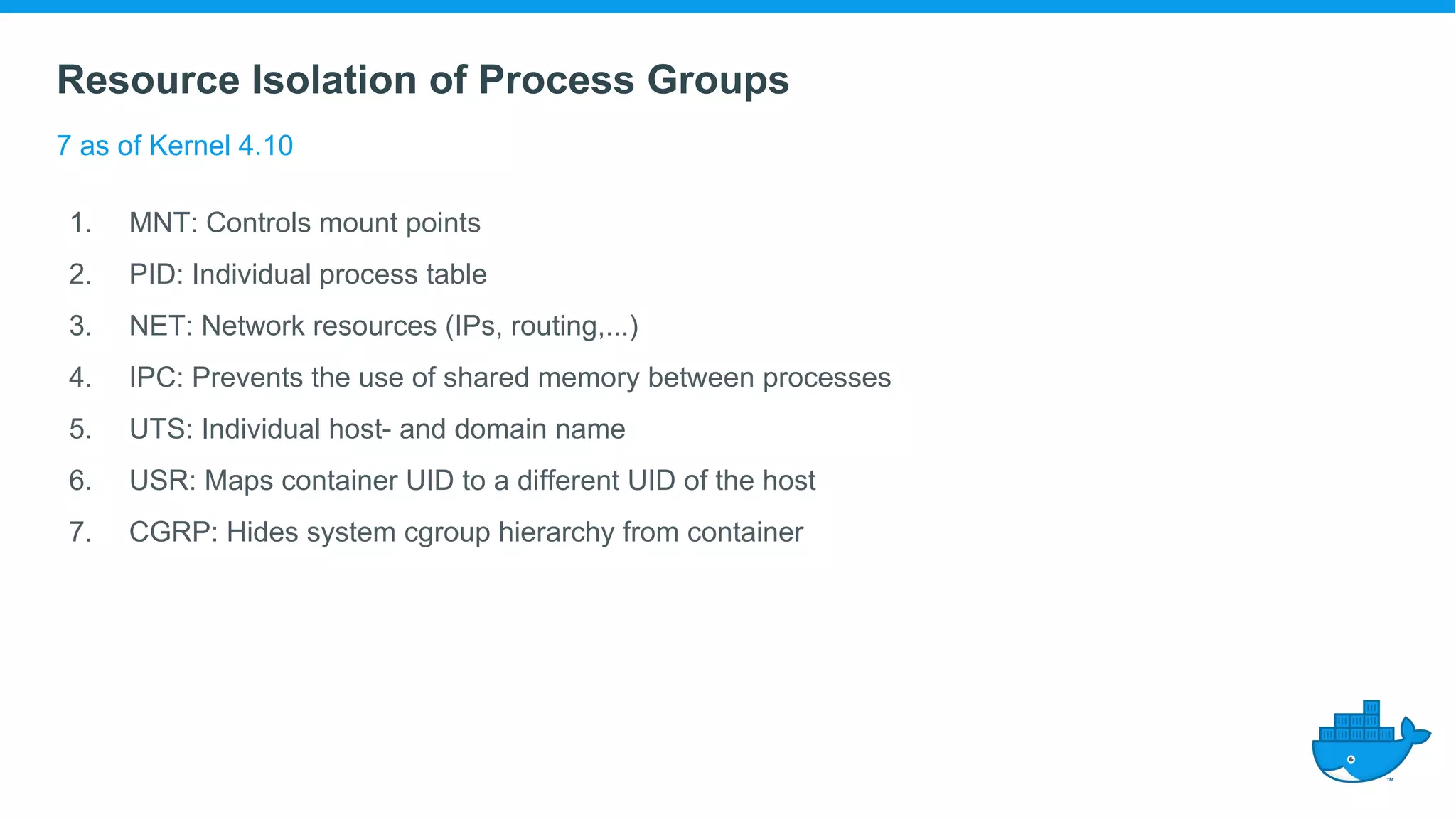
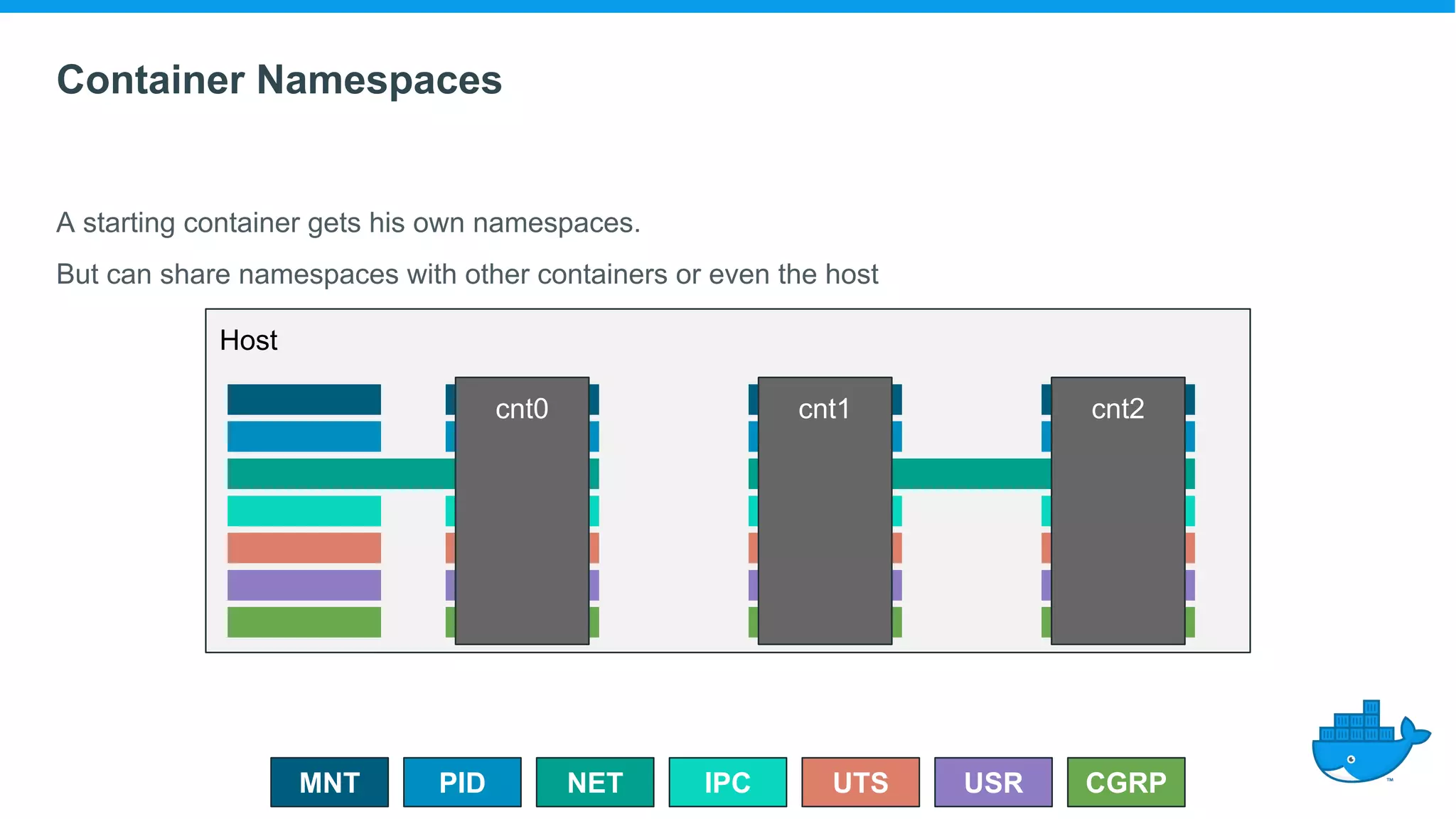
The document provides an overview of container technology, highlighting its historical development and technical components, including namespaces and control groups (cgroups). It discusses how containers isolate processes and manage resources in a virtualized environment. Additionally, it touches on the evolution of container standards and tools, emphasizing the role of Docker in popularizing container usage.






![CGroups / Filesystem Layering
Short Recap [cont]](https://image.slidesharecdn.com/containertechnology1011-180221180827/75/Linux-Container-Technology-101-10-2048.jpg)
![Overlay Filesystem
Compose a FS from multiple pieces
ubuntu:16.04
openjre:9-b114
appA.jar:1.1 appB.jar
ARG FROM openjre:9-b114
COPY appB.jar /usr/local/bin/
CMD [“java”, “-jar”, “/usr/local/bin/appB.jar”]
ARG FROM openjre:9-b114
COPY appA.jar /usr/local/bin/
CMD [“java”, “-jar”, “/usr/local/bin/appA.jar”]
FROM ubuntu:16.04
ARG JRE_VER=9~b114-0ubuntu1
RUN apt-get update
&& apt-get install -y openjdk-9-jre-headless=${JRE_VER}
&& java -version
openjre:9-b117](https://image.slidesharecdn.com/containertechnology1011-180221180827/75/Linux-Container-Technology-101-11-2048.jpg)