The document covers the essential aspects of container security, detailing the history of Red Hat and containers, the architecture of container technology, and the various security mechanisms involved. Key topics include Linux kernel namespaces, control groups, the Docker daemon, and security measures like SELinux and Linux capabilities. The presentation emphasizes best practices for securing containers and the importance of regular maintenance to ensure safety and efficiency in application deployment.




















![24
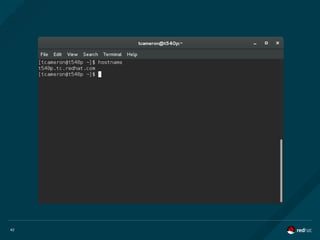
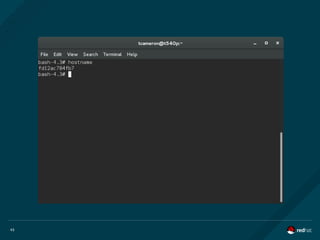
LINUX KERNEL NAMESPACES
What are they?
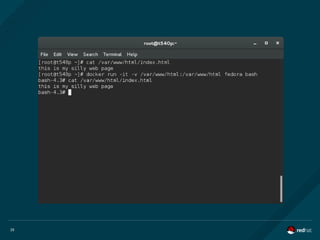
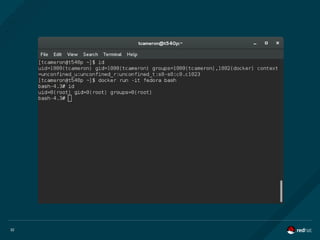
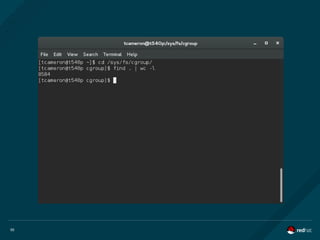
Mount namespaces allow a container to “think” that a directory which is actually
mounted from the host OS is exclusively the container's.
When you start a container with the -v [host-path]:[container-path]:[rw|ro] argument,
you can mount a directory from the host in the container. The container “sees” the
directory in its own mount namespace, not knowing that it is actually on the host. So
multiple containers could, for instance use the host's /var/www/html directory without
having to copy content to all the containers.](https://image.slidesharecdn.com/redhatdockercon2016containersandsecurity-160624231257/85/Practical-Container-Security-by-Mrunal-Patel-and-Thomas-Cameron-Red-Hat-24-320.jpg)