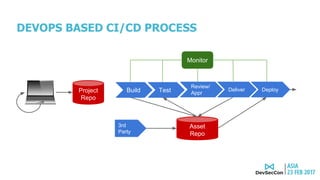
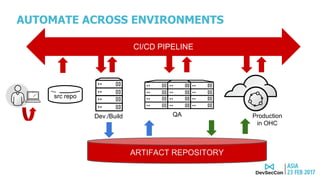
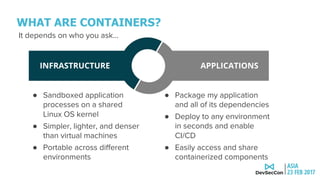
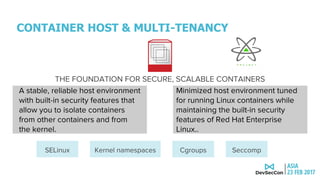
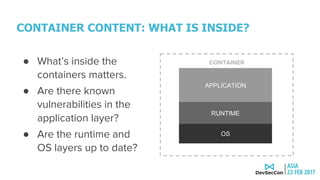
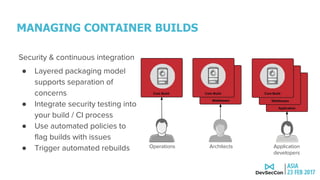
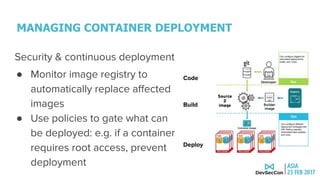
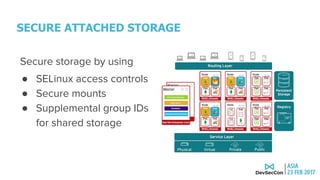
This document discusses securing the container DevOps pipeline. It begins by explaining why the term "DevSecOps" emerged, as integrating security into DevOps practices at scale became important. It then outlines the modern DevOps CI/CD process using containers and APIs. The rest of the document details how to secure different aspects of the container lifecycle, such as the container host, content, registries, builds, deployments, orchestration, networking, storage, APIs, and federated clusters. It argues for taking a lifecycle approach to container security and integrating practices like role-based access controls, network isolation, secure storage, and API management across the container platform.