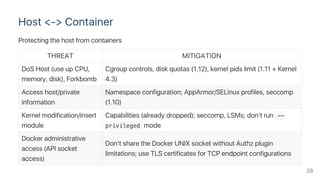
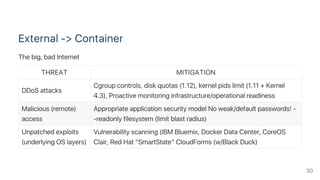
Linux namespaces and control groups (cgroups) provide isolation and security for Docker containers. Namespaces isolate processes by PID, network, IPC, mount points, etc. Cgroups limit CPU, memory, storage resources. Capabilities and security models like seccomp, AppArmor further harden containers by dropping privileges and blocking risky syscalls. Together, these mechanisms isolate containers and applications from hosts, other containers, and external attacks while still allowing resource sharing through the kernel.




![clone()
static char container_stack[STACK_SIZE];
char* const container_args[] = {"/bin/bash", NULL};
int container_main(void* arg)
{
// Open a shell
execv(container_args[0], container_args);
// Should never be here
}
int main()
{
int container_pid = clone(container_main, container_stack+STACK_SIZE,
SIGCHLD, NULL);
waitpid(container_pid, NULL, 0);
return 0;
}
6](https://image.slidesharecdn.com/dockerisolationandsecurity-170518014158/85/Docker-Container-isolation-and-security-6-320.jpg)
![UTS Namespace ( CLONE_NEWUTS )
Isolates system identifiers: nodename and domainname .
int container_main(void* arg)
{
sethostname("container", 10);
// Open a shell
execv(container_args[0], container_args);
// Should never be here
}
7](https://image.slidesharecdn.com/dockerisolationandsecurity-170518014158/85/Docker-Container-isolation-and-security-7-320.jpg)
![User namespace ( CLONE_NEWUSER )
Isolates the user and group ID spaces.
A process's UID and GID can be different inside and outside a user namespace.
void set_map(char* file, int inside_id, int outside_id, int len) {
FILE *fd = fopen(file, "w");
fprintf(fd, "%d %d %d", inside_id, outside_id, len);
fclose(fd);
}
void set_uid_map(pid_t pid, int inside_id, int outside_id, int len) {
char file[256];
sprintf(file, "/proc/%d/uid_map", pid);
set_map(file, inside_id, outside_id, len);
}
void set_gid_map(pid_t pid, int inside_id, int outside_id, int len) {
char file[256];
sprintf(file, "/proc/%d/gid_map", pid);
set_map(file, inside_id, outside_id, len);
}
12](https://image.slidesharecdn.com/dockerisolationandsecurity-170518014158/85/Docker-Container-isolation-and-security-12-320.jpg)







![Seccomp
Block specific syscalls from being used by container binaries.
$ cat policy.json
{
"defaultAction": "SCMP_ACT_ALLOW",
"syscalls": [
{
"name": "chmod",
"action": "SCMP_ACT_ERRNO"
}
]
}
$ docker run --rm -it --security-opt seccomp:policy.json busybox chmod 640
/etc/resolv.conf
chmod: /etc/resolv.conf: Operation not permitted
25](https://image.slidesharecdn.com/dockerisolationandsecurity-170518014158/85/Docker-Container-isolation-and-security-25-320.jpg)