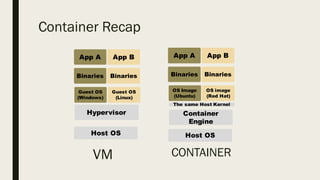
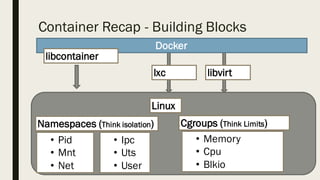
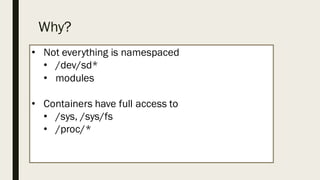
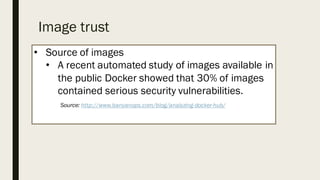
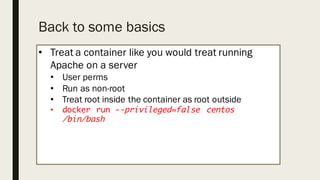
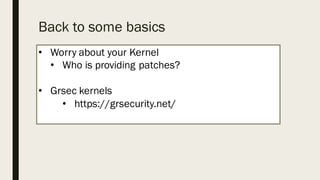
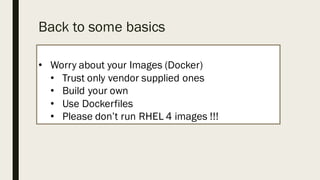
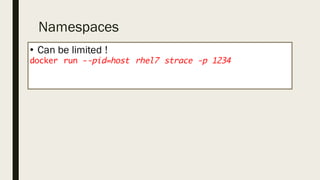
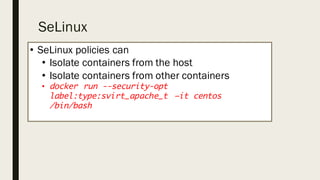
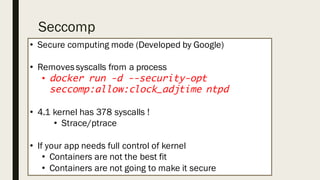
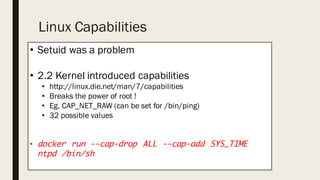
This document discusses the security aspects of containers compared to virtual machines. While containers provide better performance through thin isolation layers, this reduces security compared to fully virtualized systems. Containers run applications with full access to the host operating system's kernel and have limited isolation of things like devices and modules. The document recommends treating container security like a networked server by running as non-root users, using tools like SELinux for additional isolation, and only using trusted container images. Backing containers with security features of the Linux kernel like capabilities and seccomp can also help restrict what containers can access.