Unraveling Docker Security: Lessons From a Production Cloud
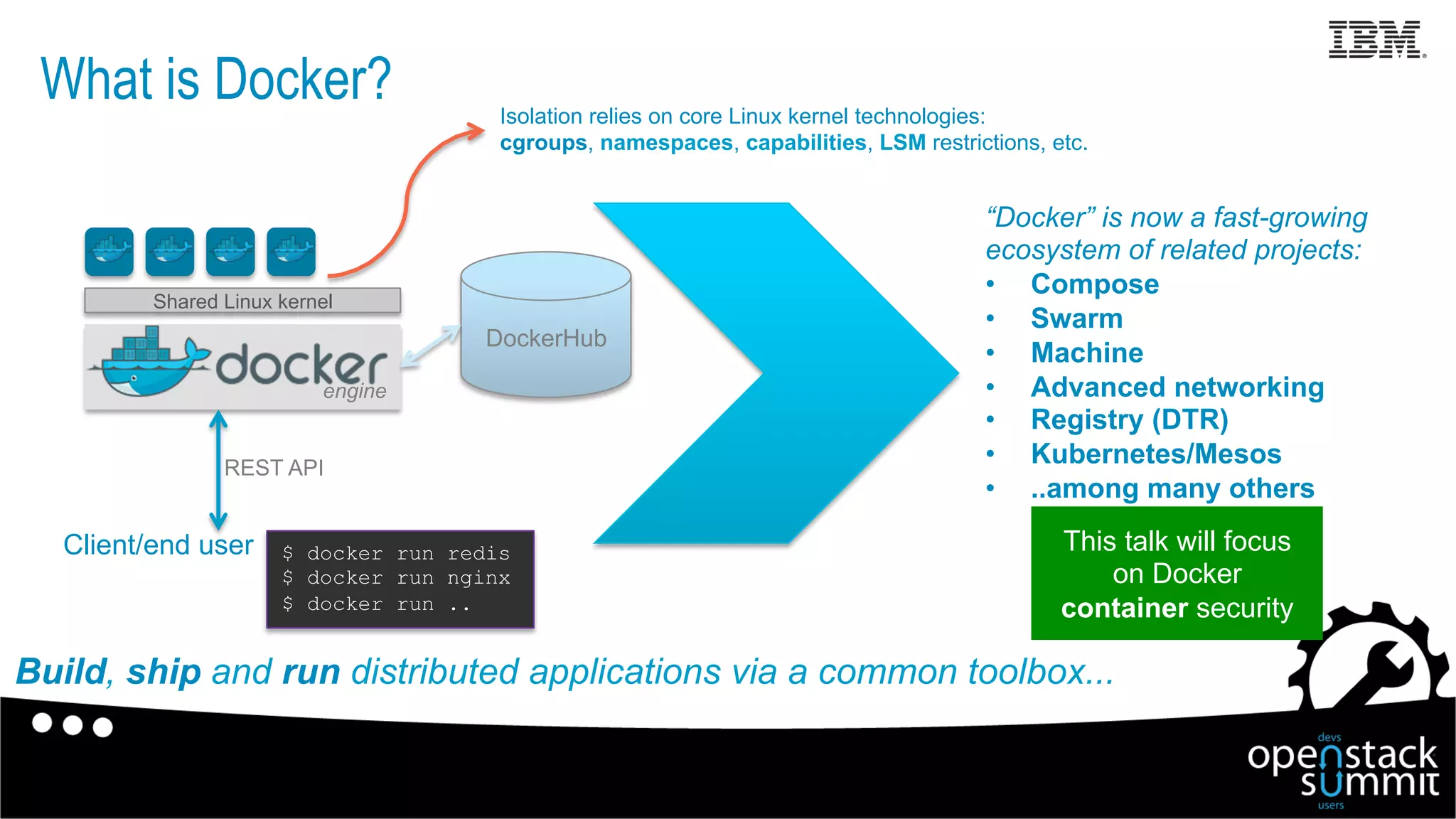
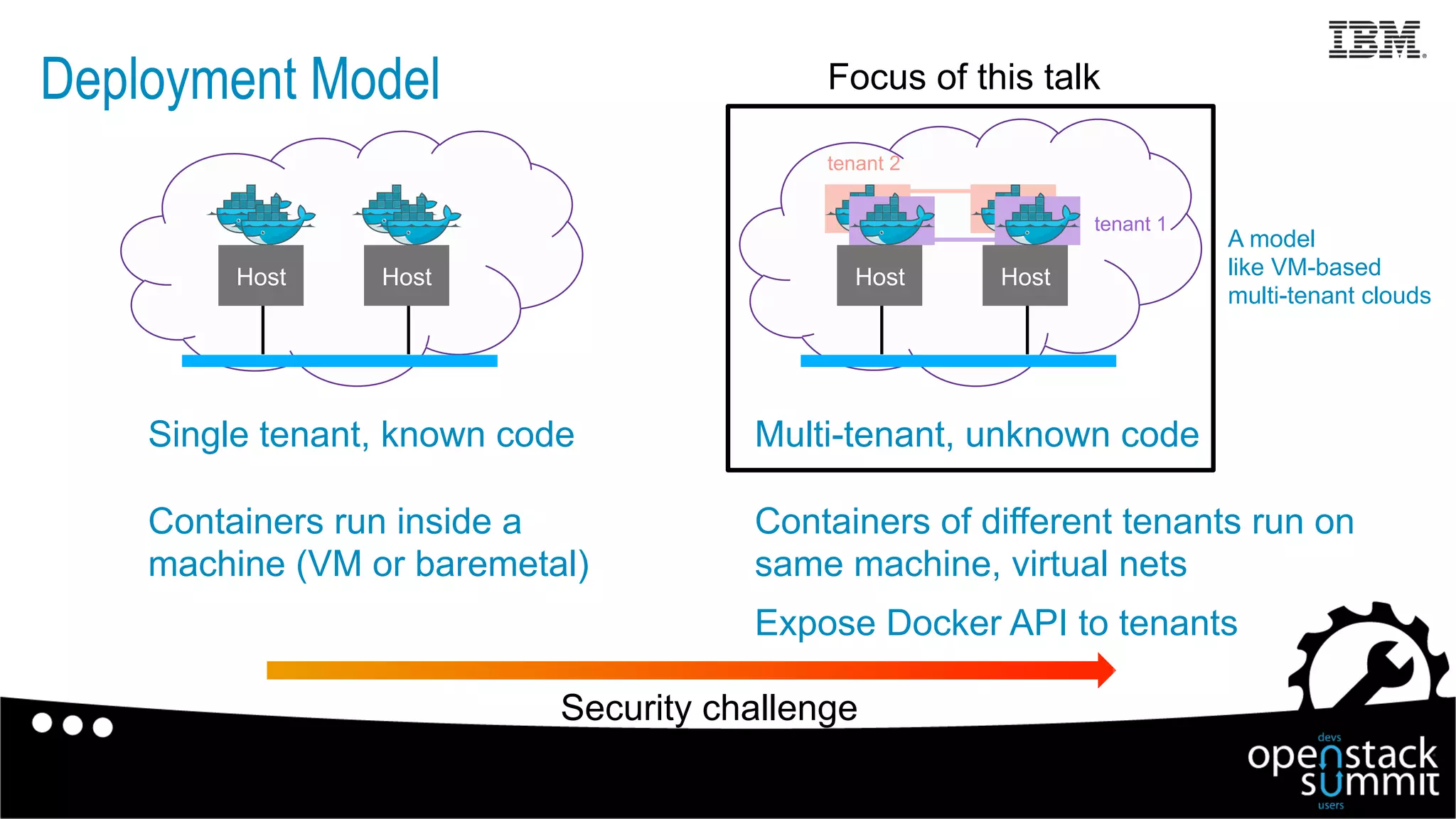
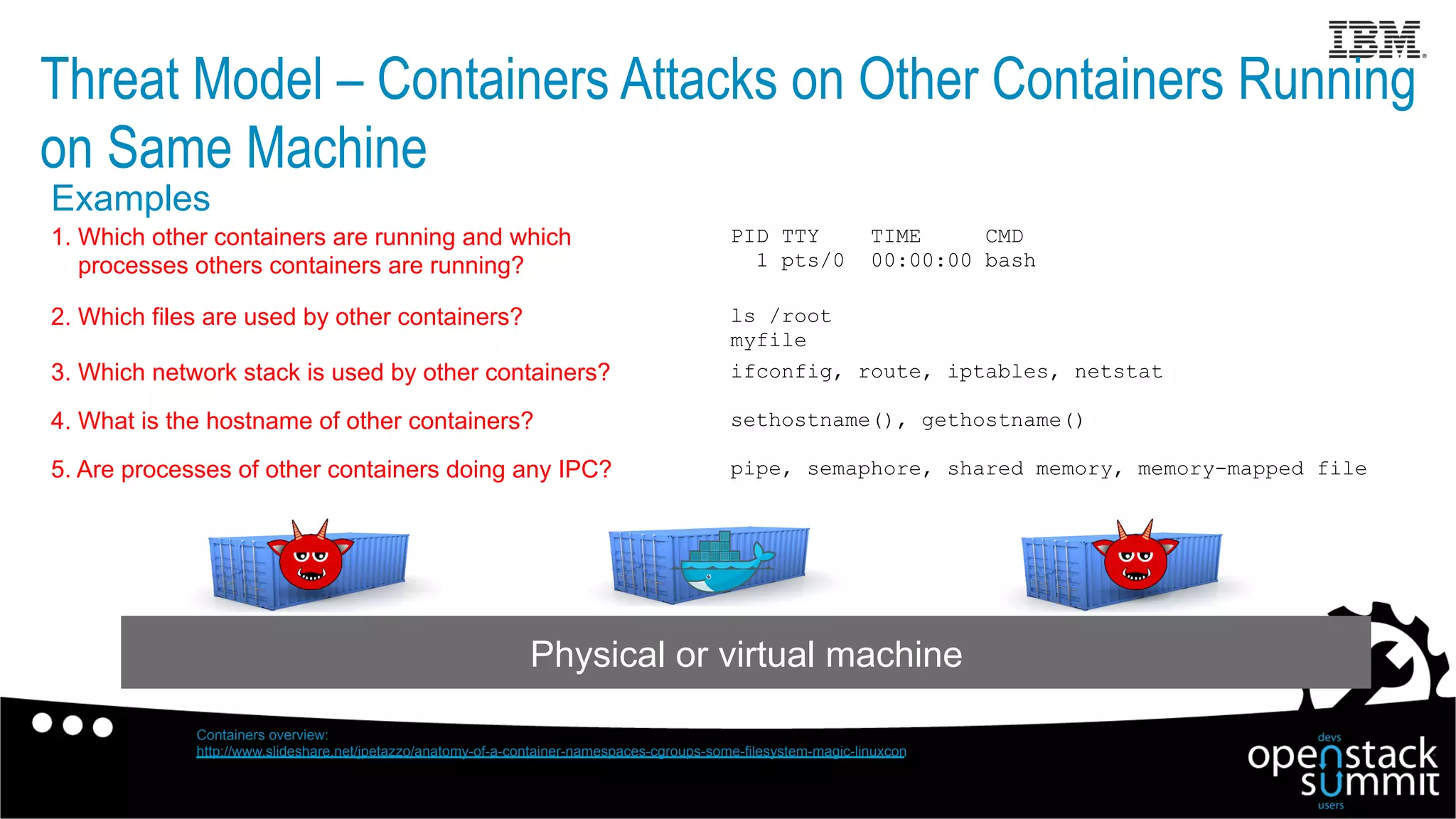
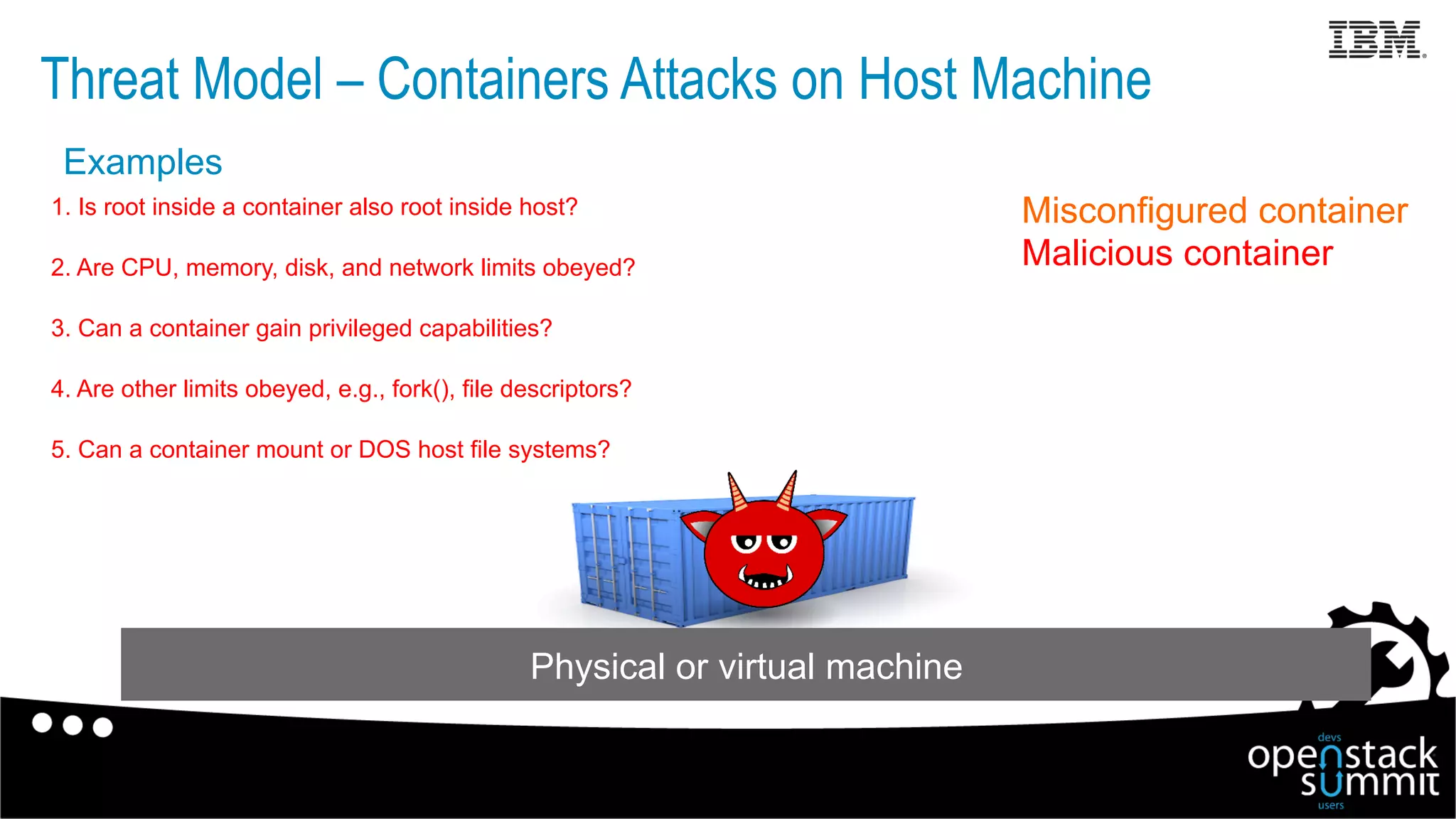
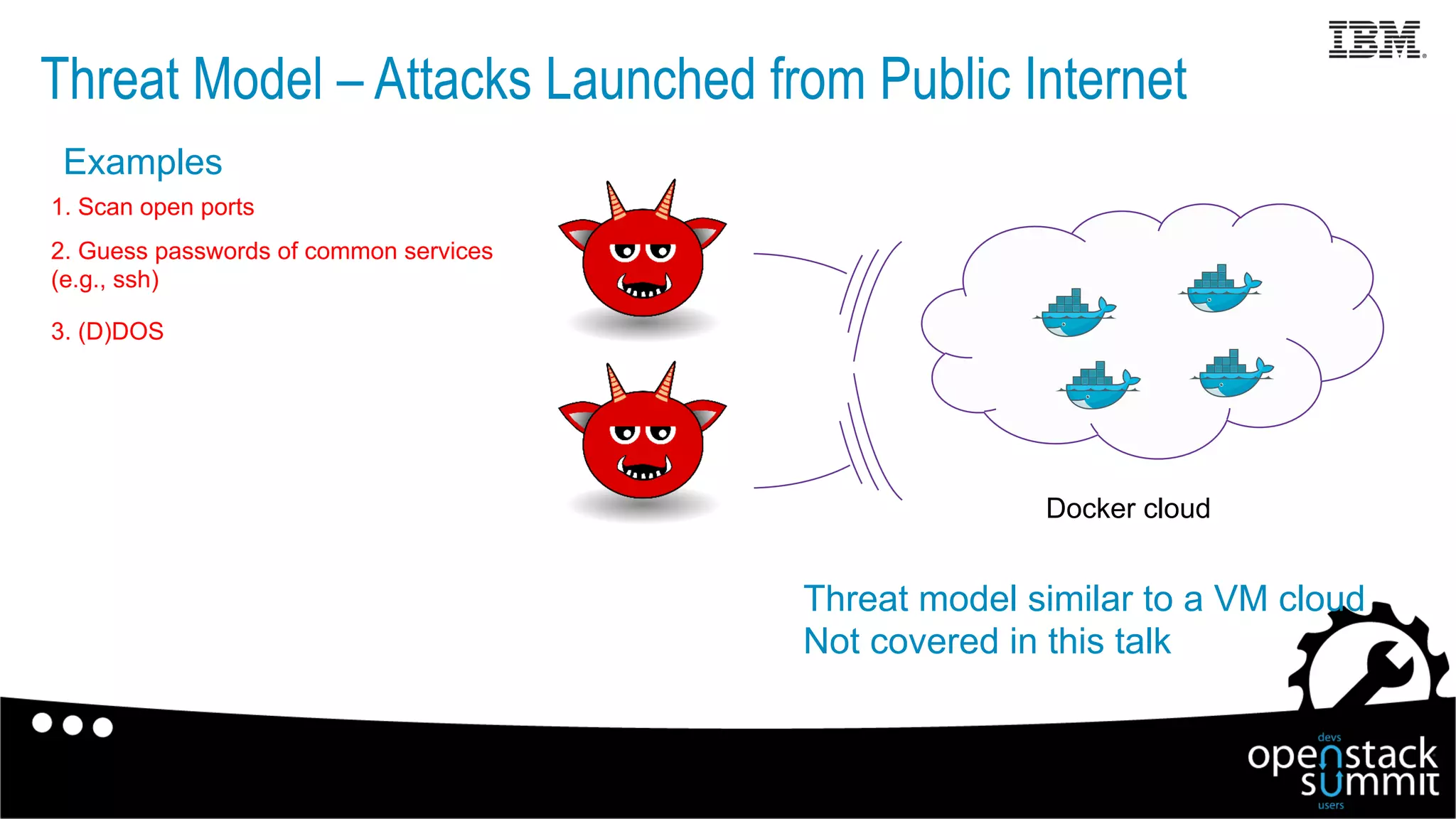
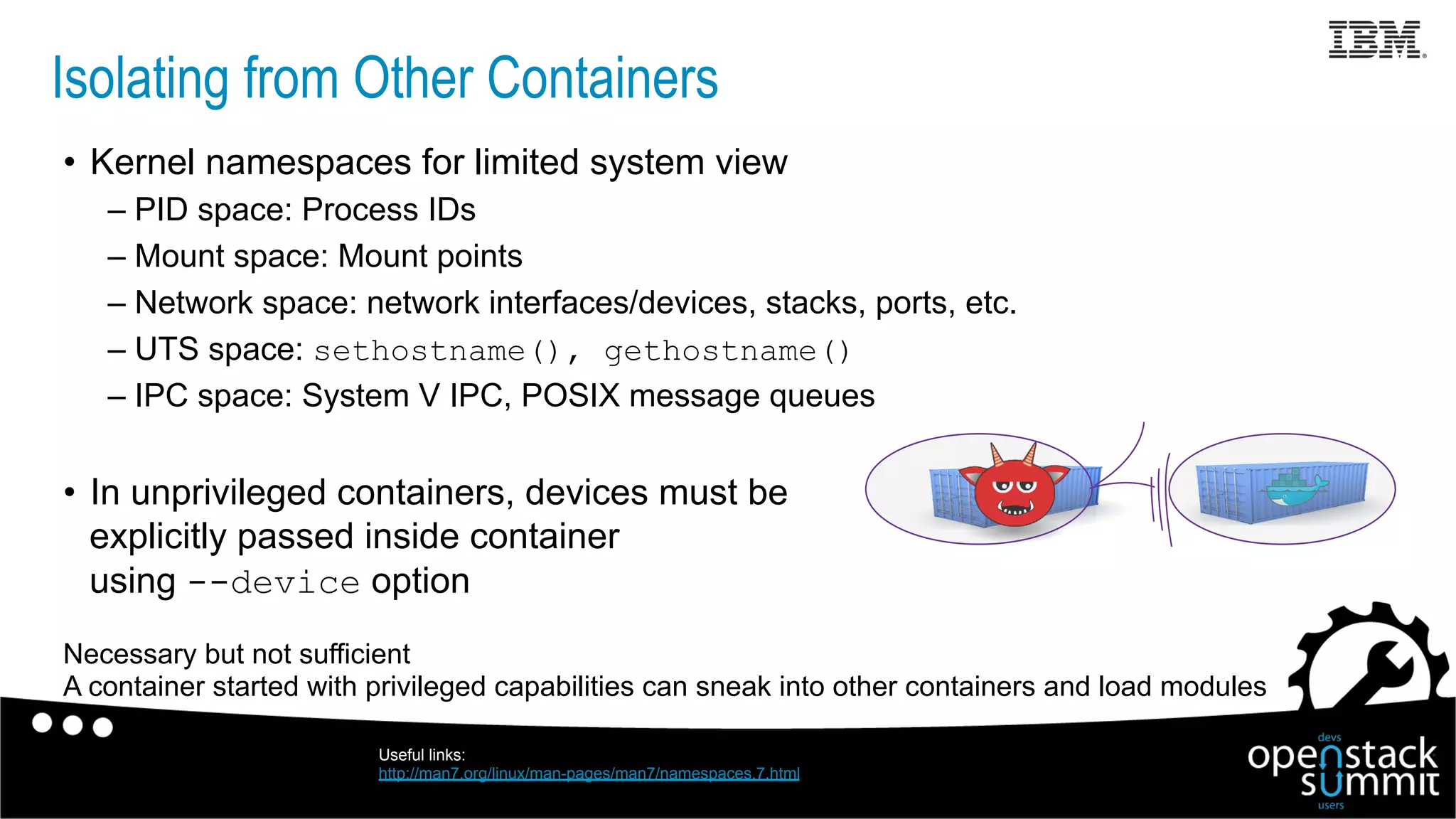
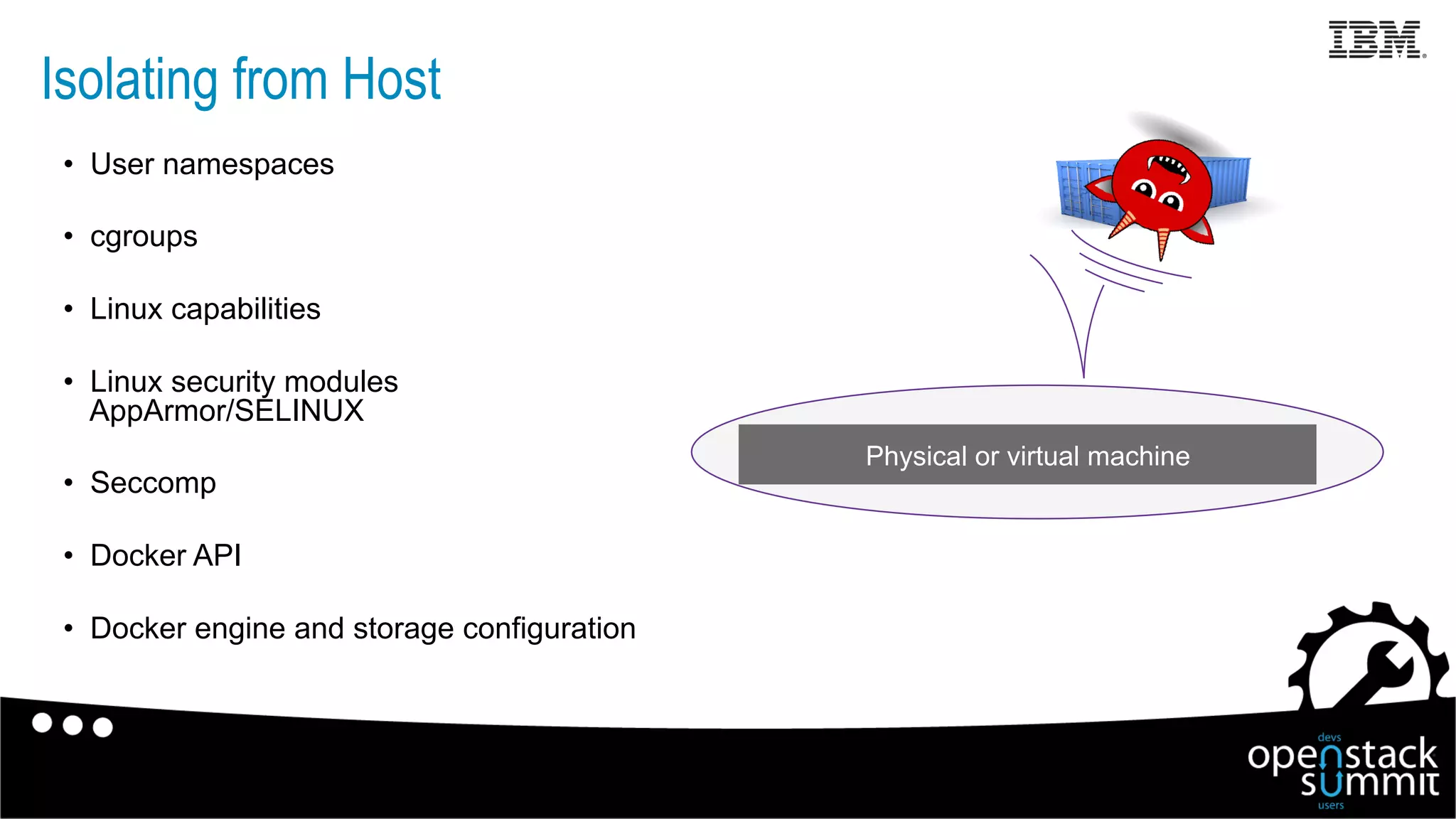
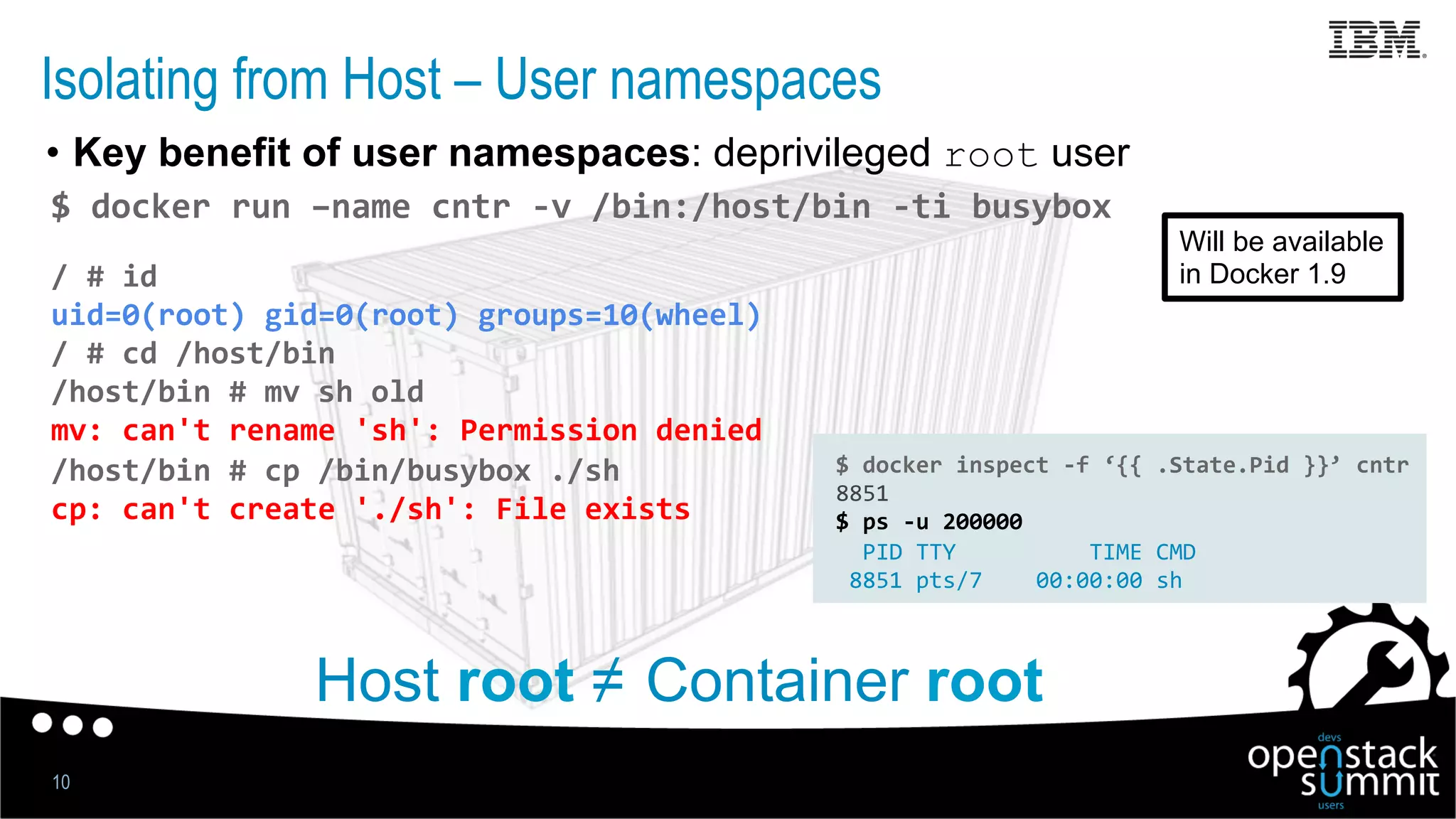
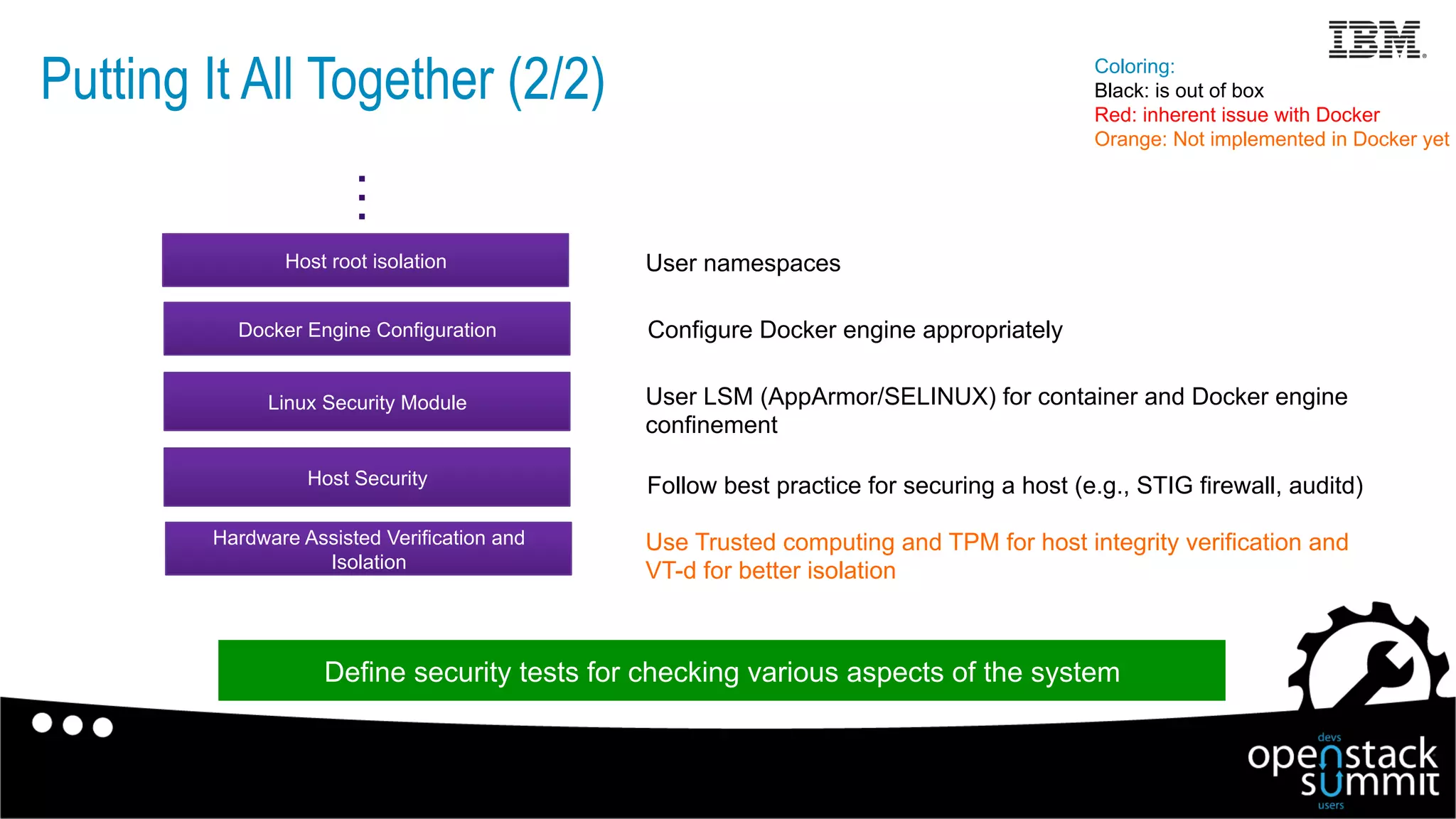
This document discusses Docker security issues in a multi-tenant cloud deployment model where containers from different tenants run on the same host machine. It outlines threats like containers attacking other containers or the host, and describes Docker features for isolation like namespaces, cgroups, capabilities, AppArmor, and restricting the Docker API. Putting these protections together can help provide security, but inherent issues remain with shared kernel access and some features needing further implementation.