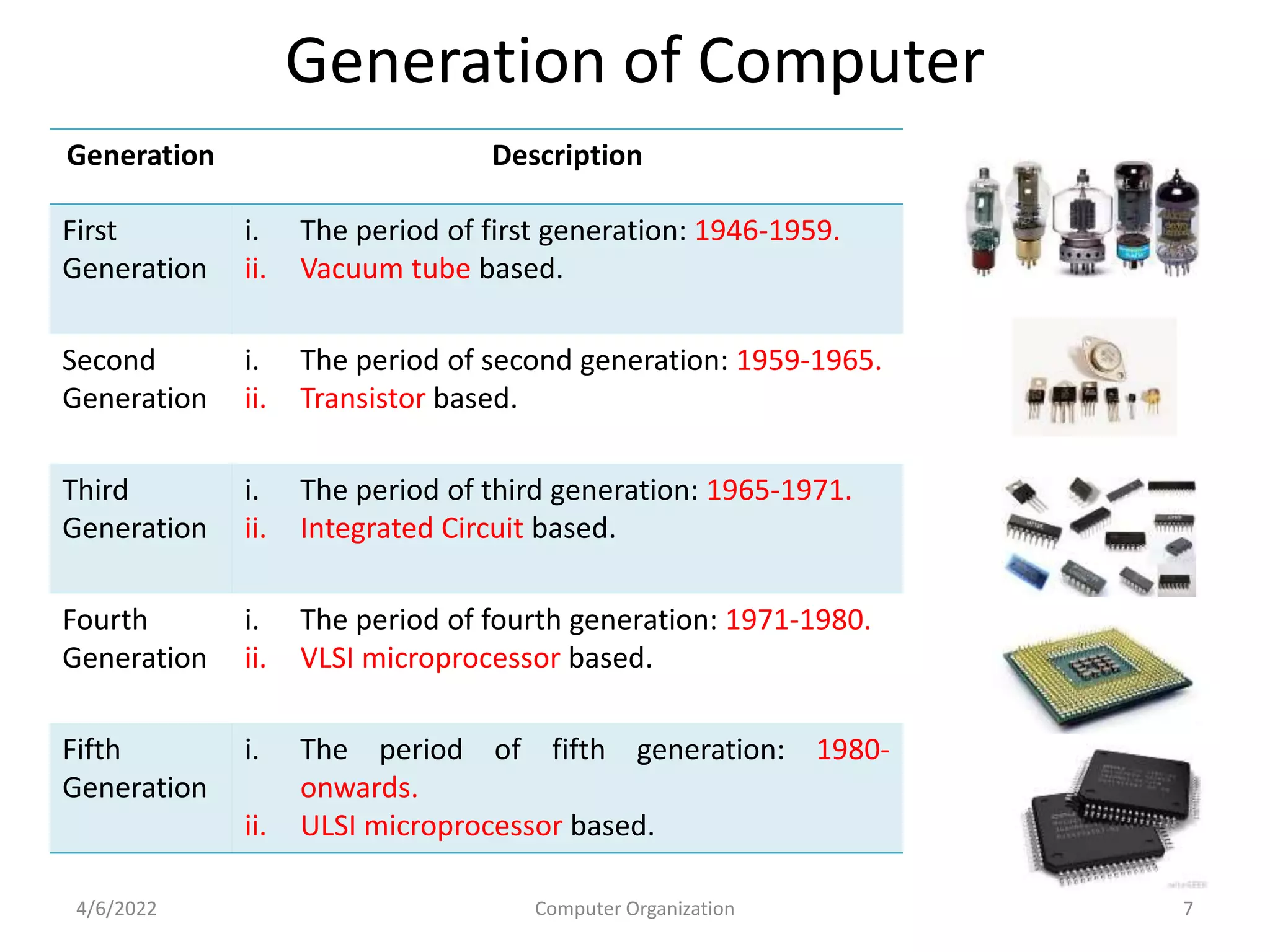
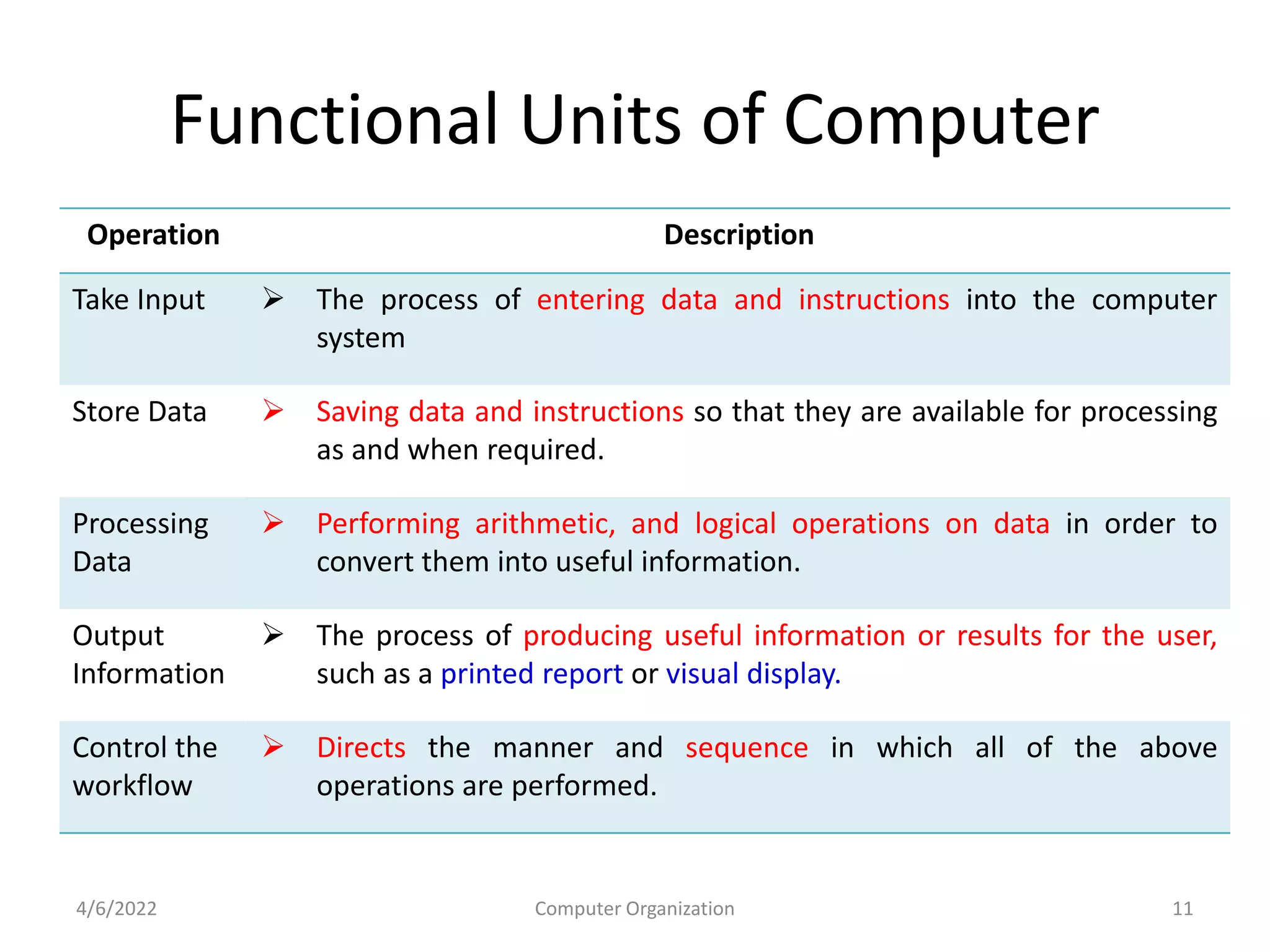
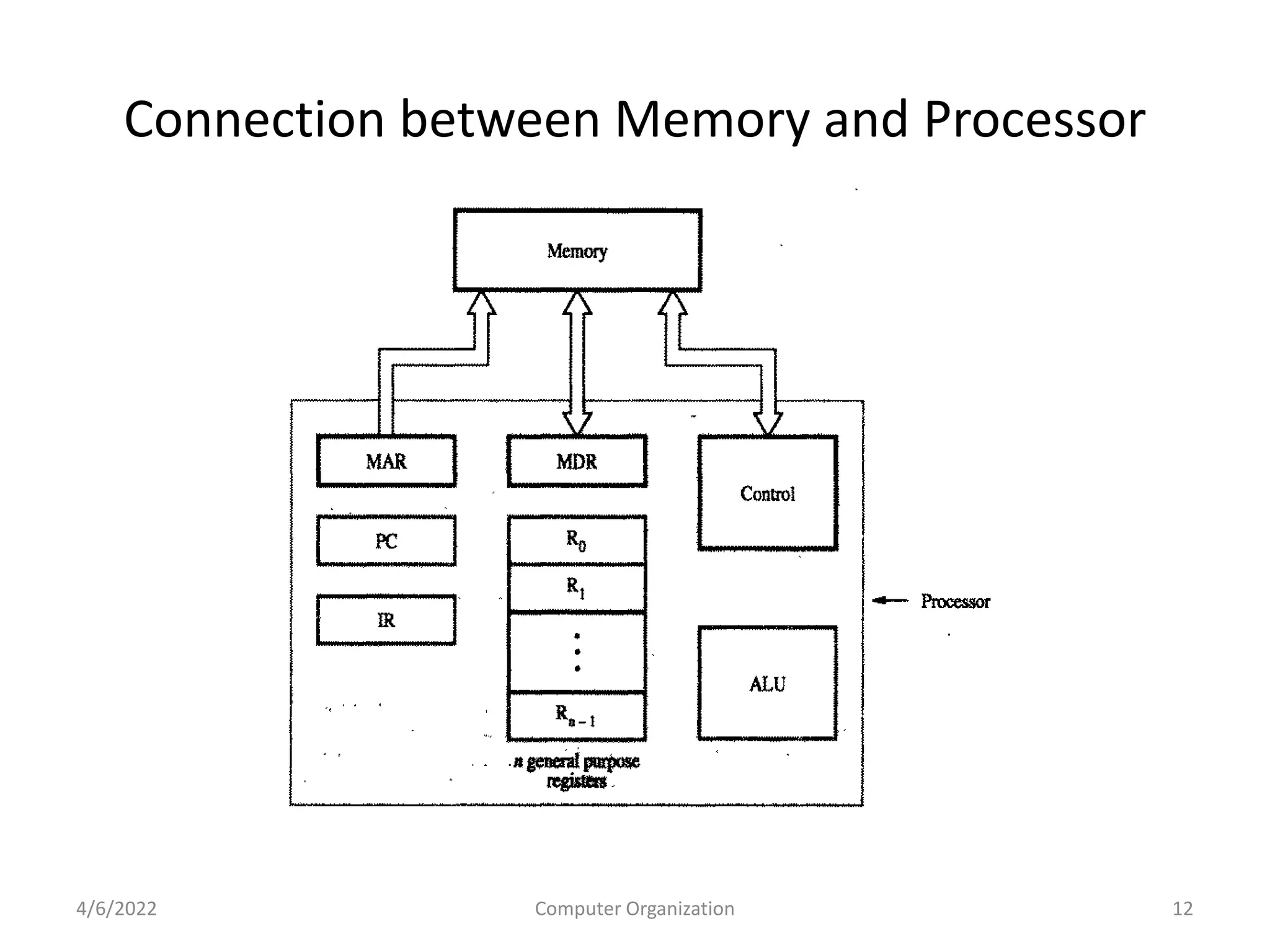
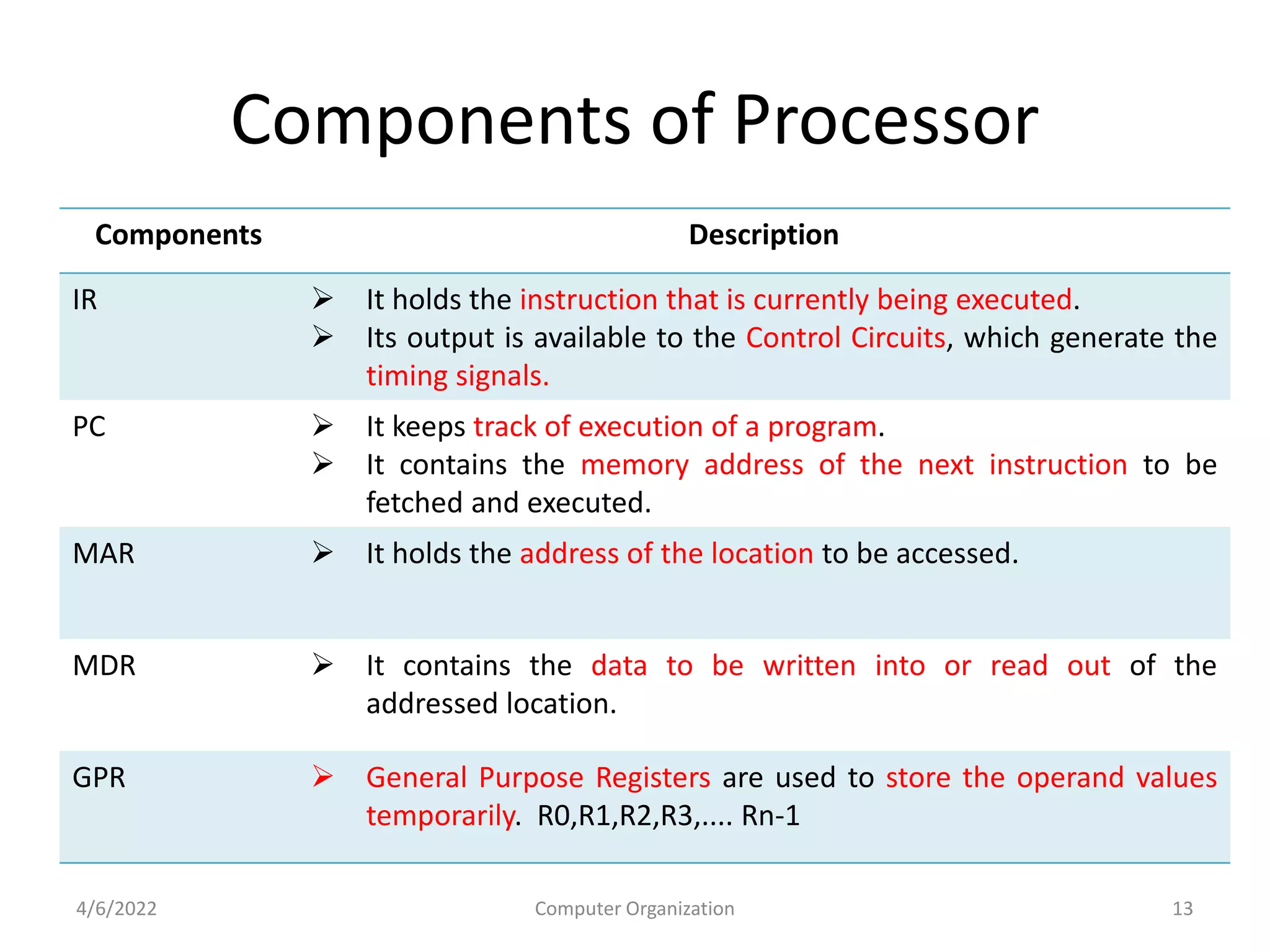
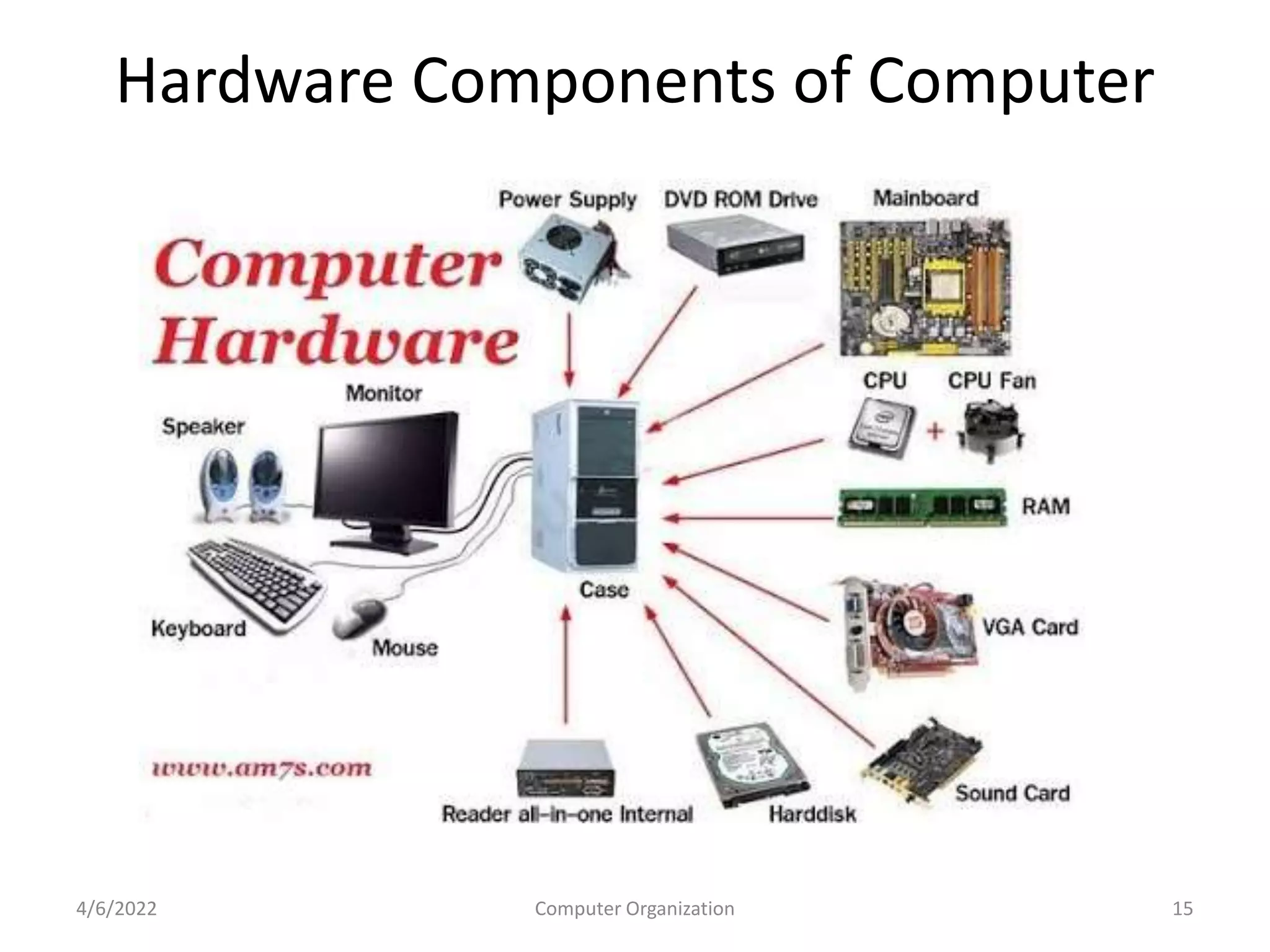
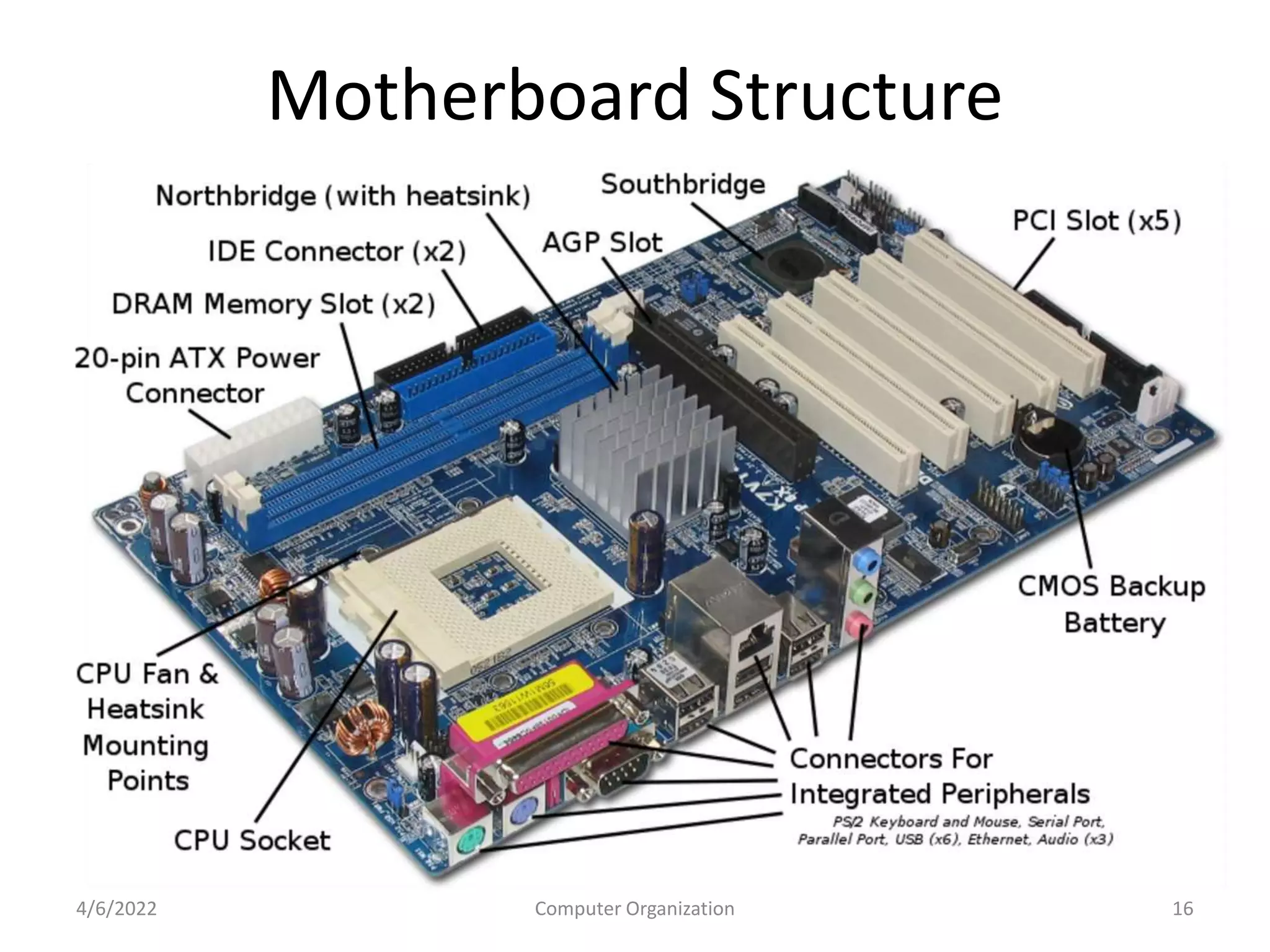
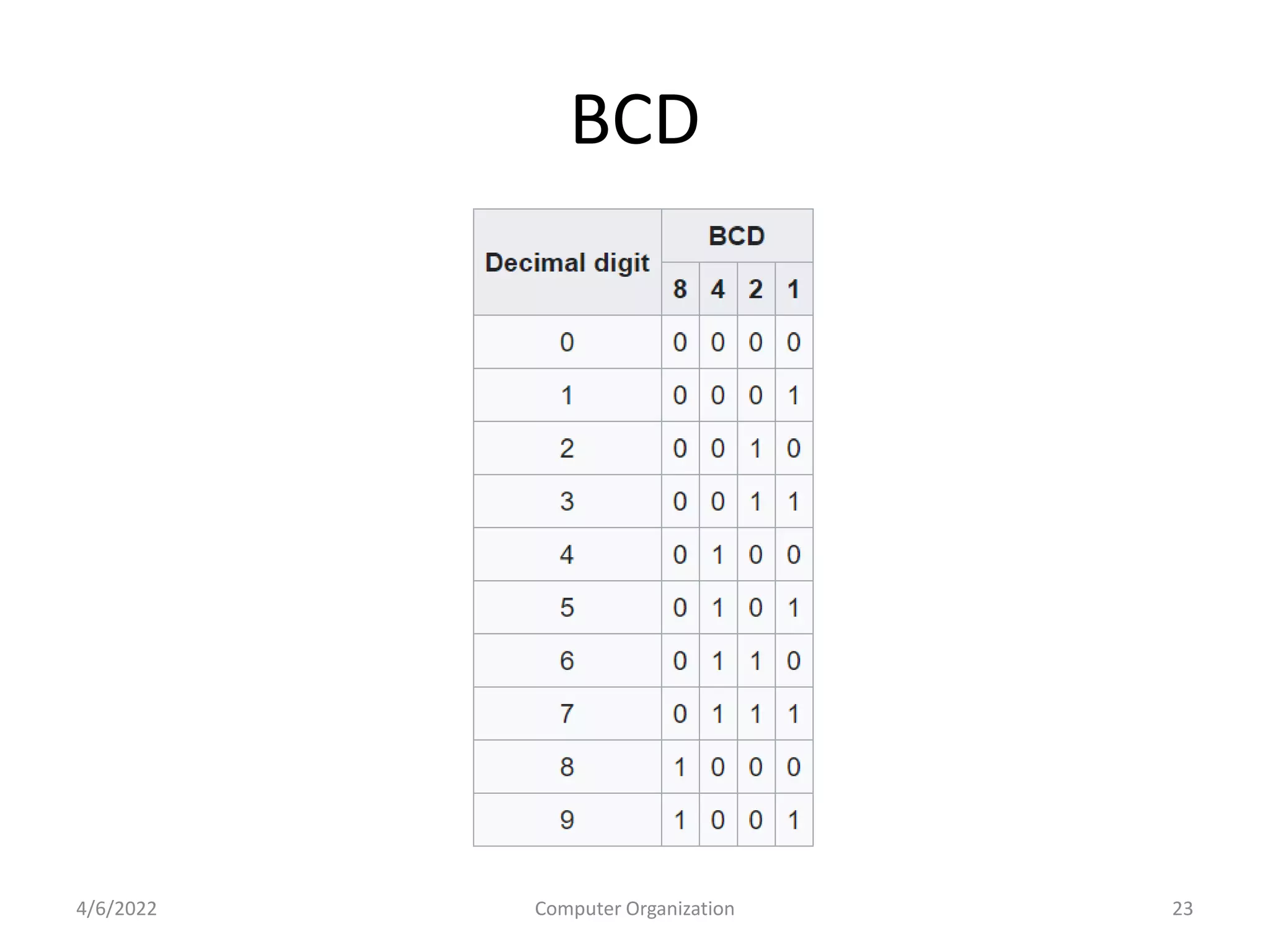
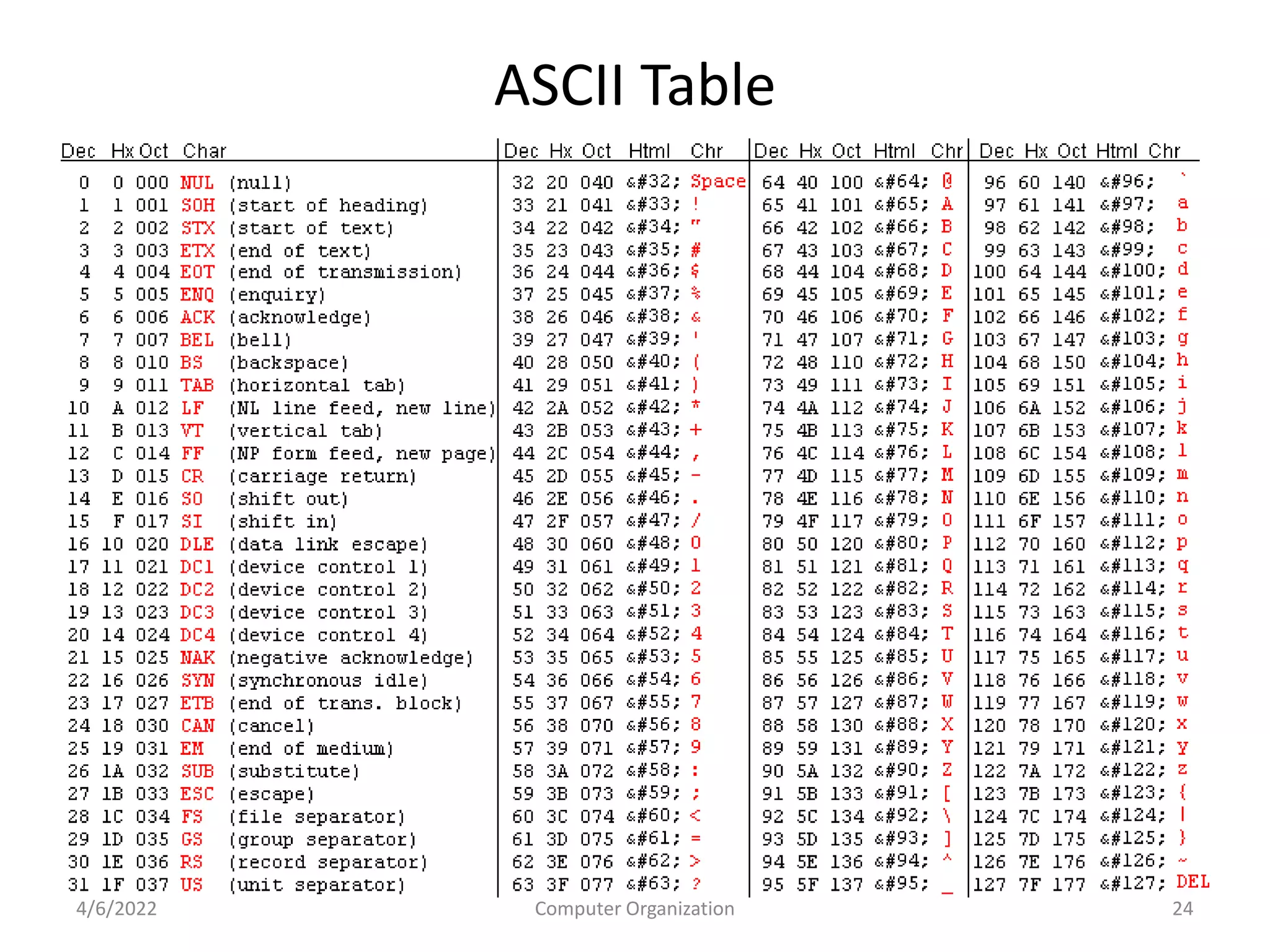
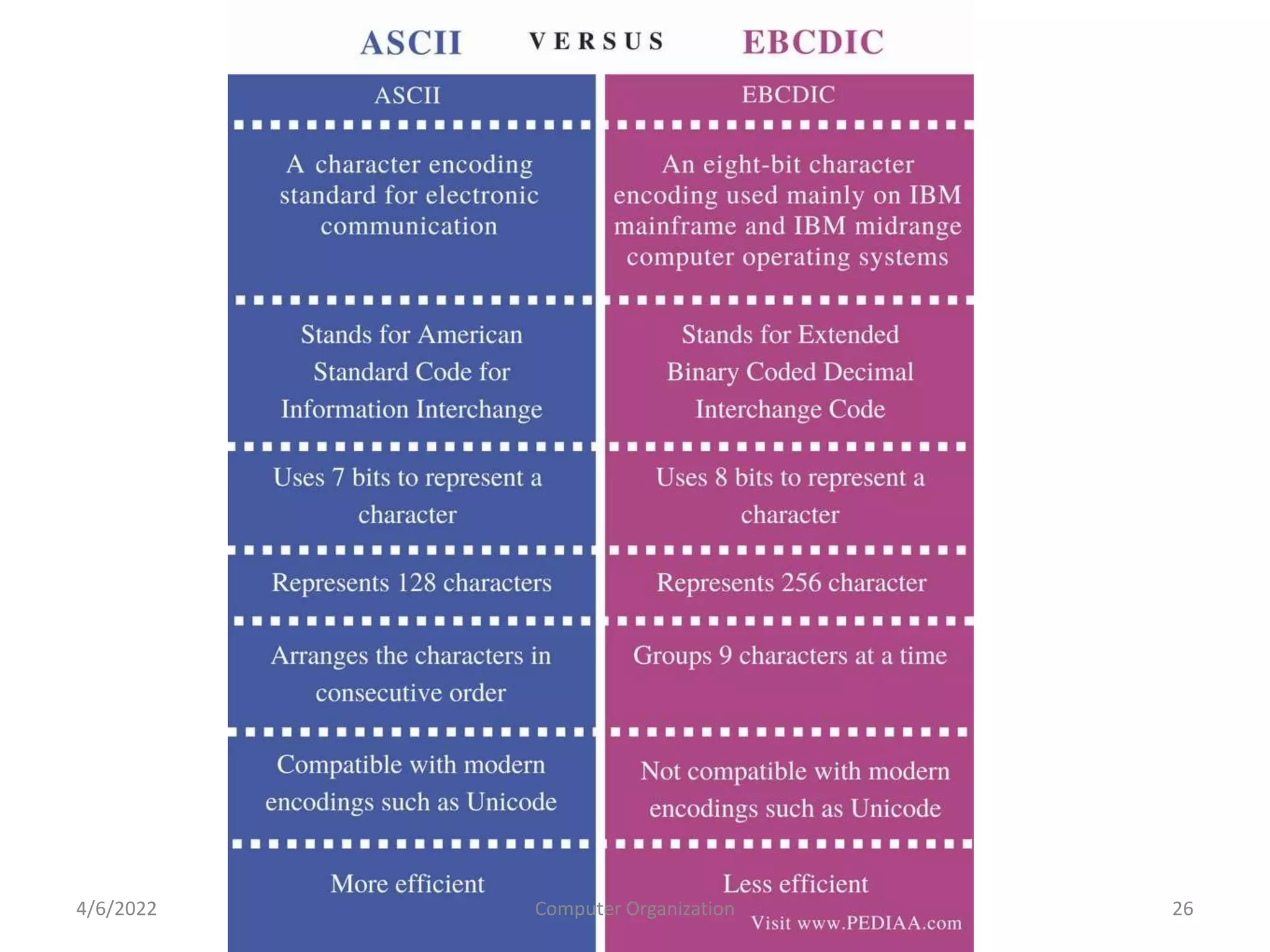
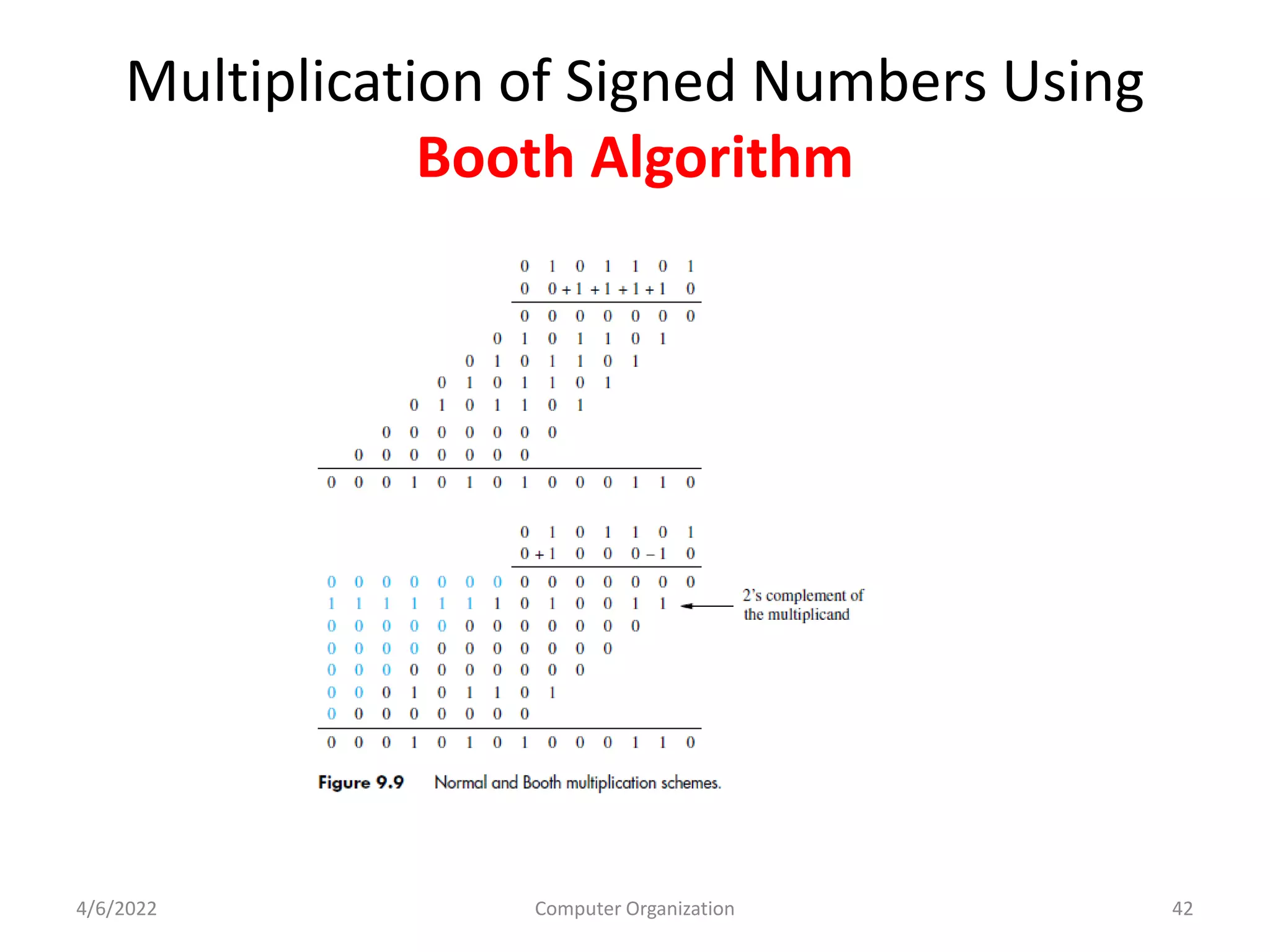
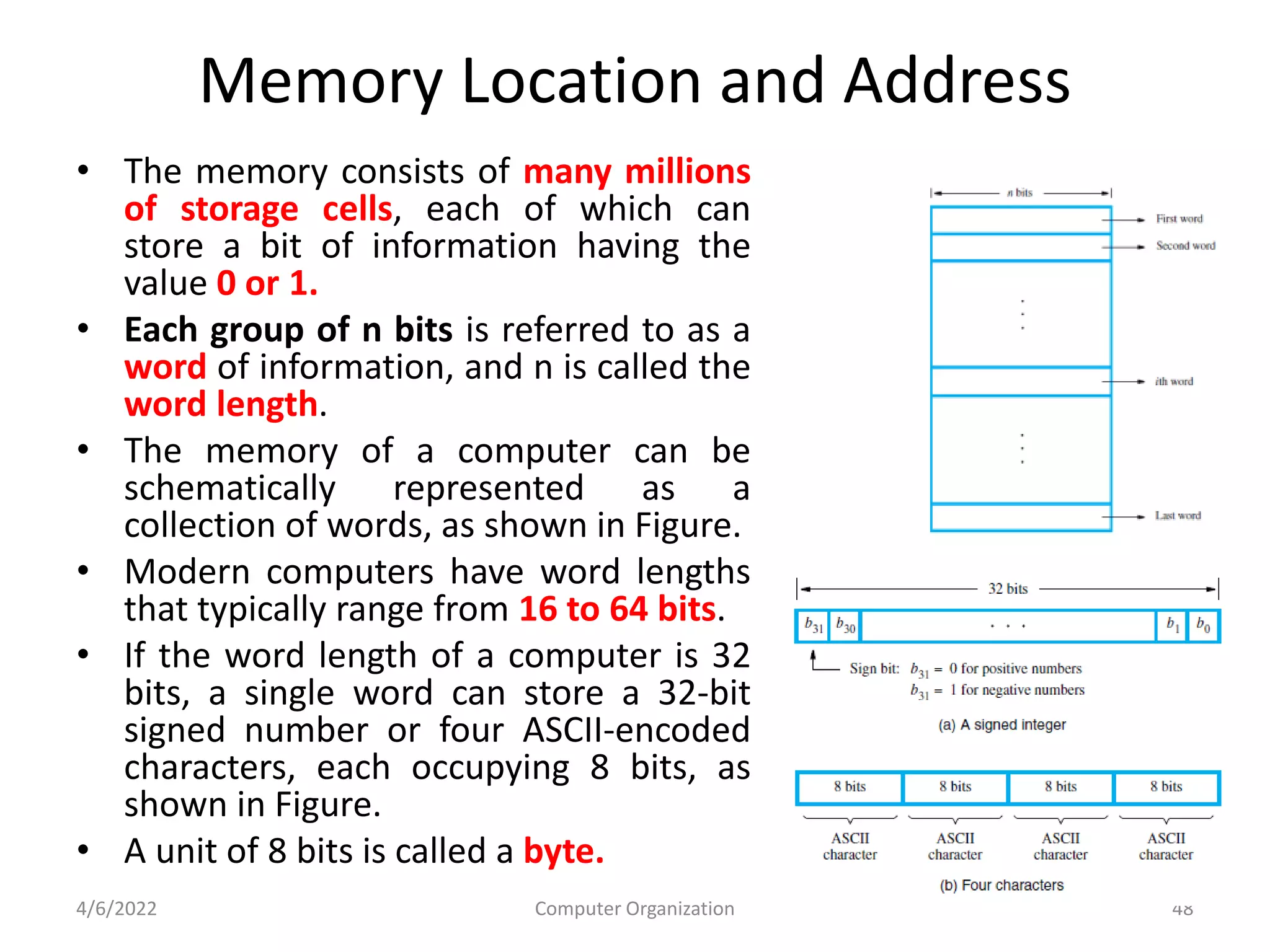
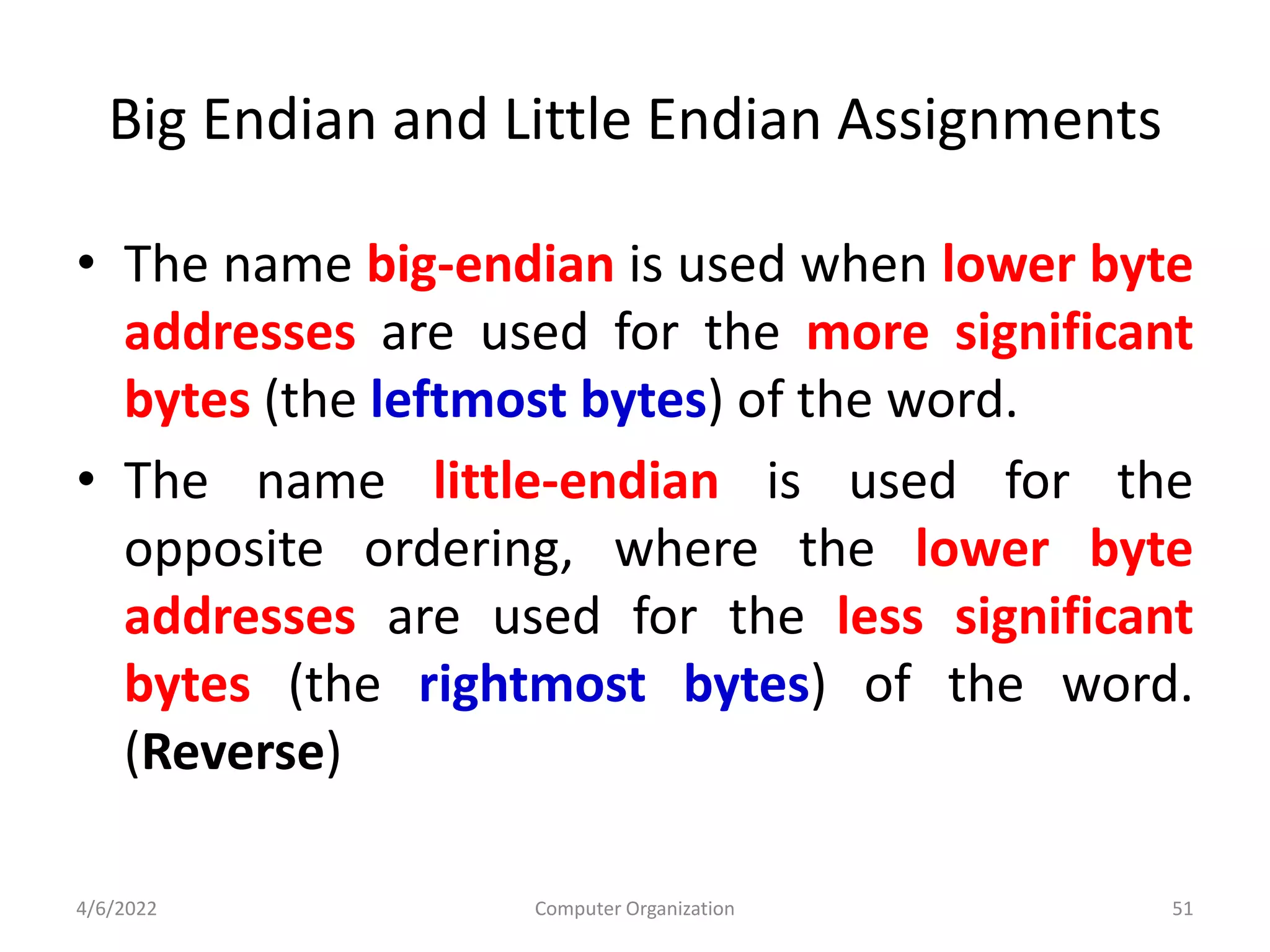
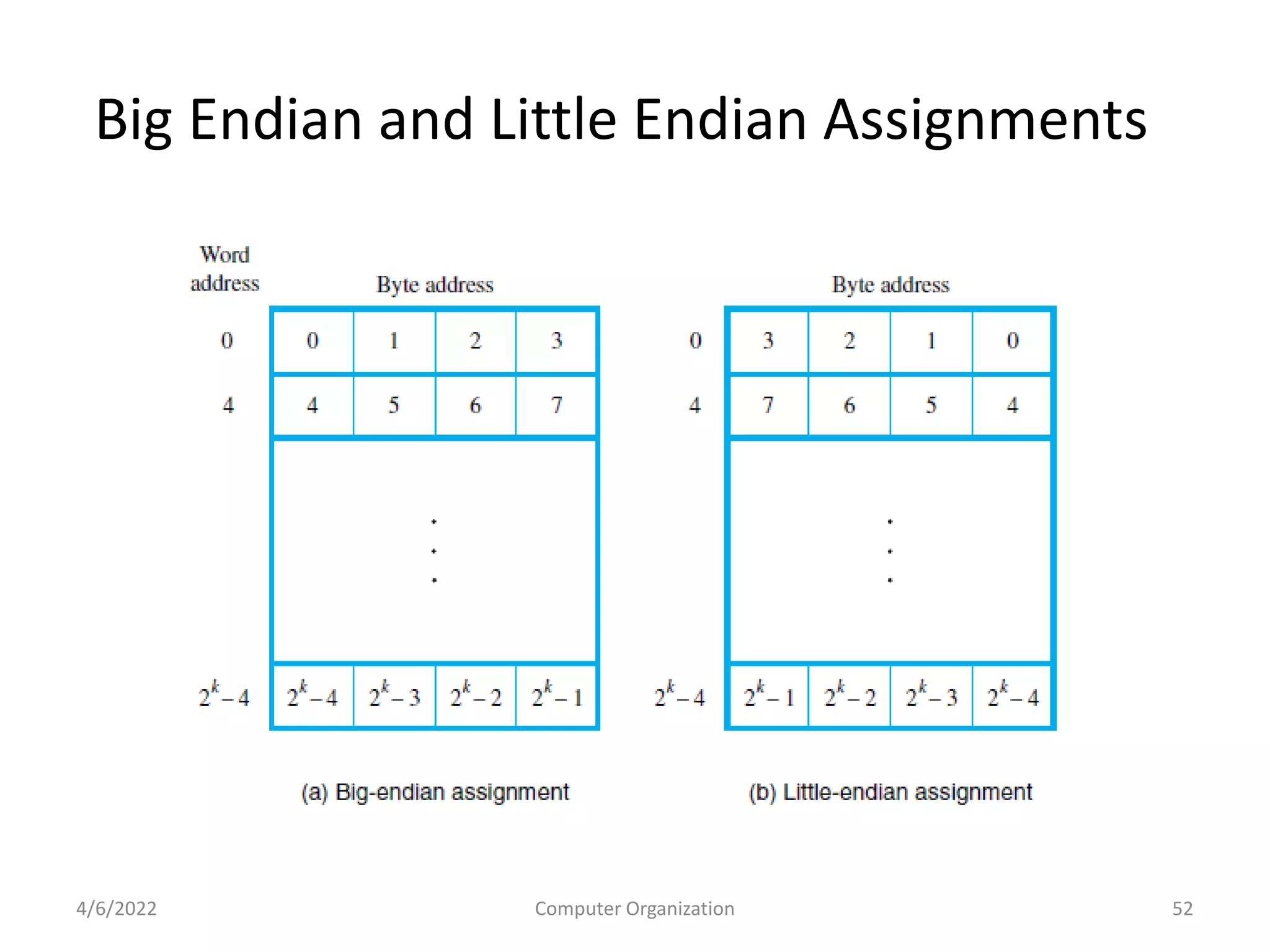
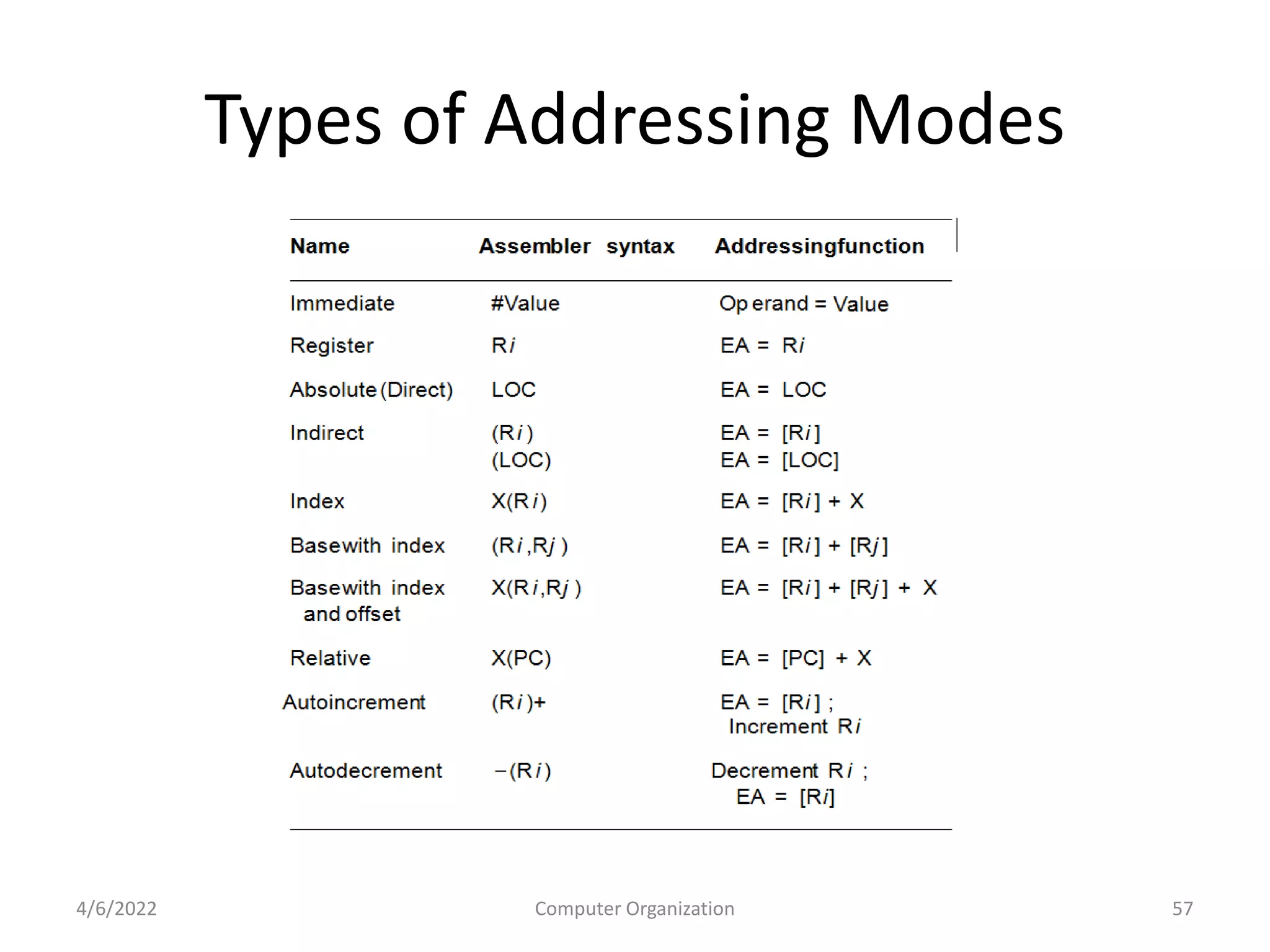
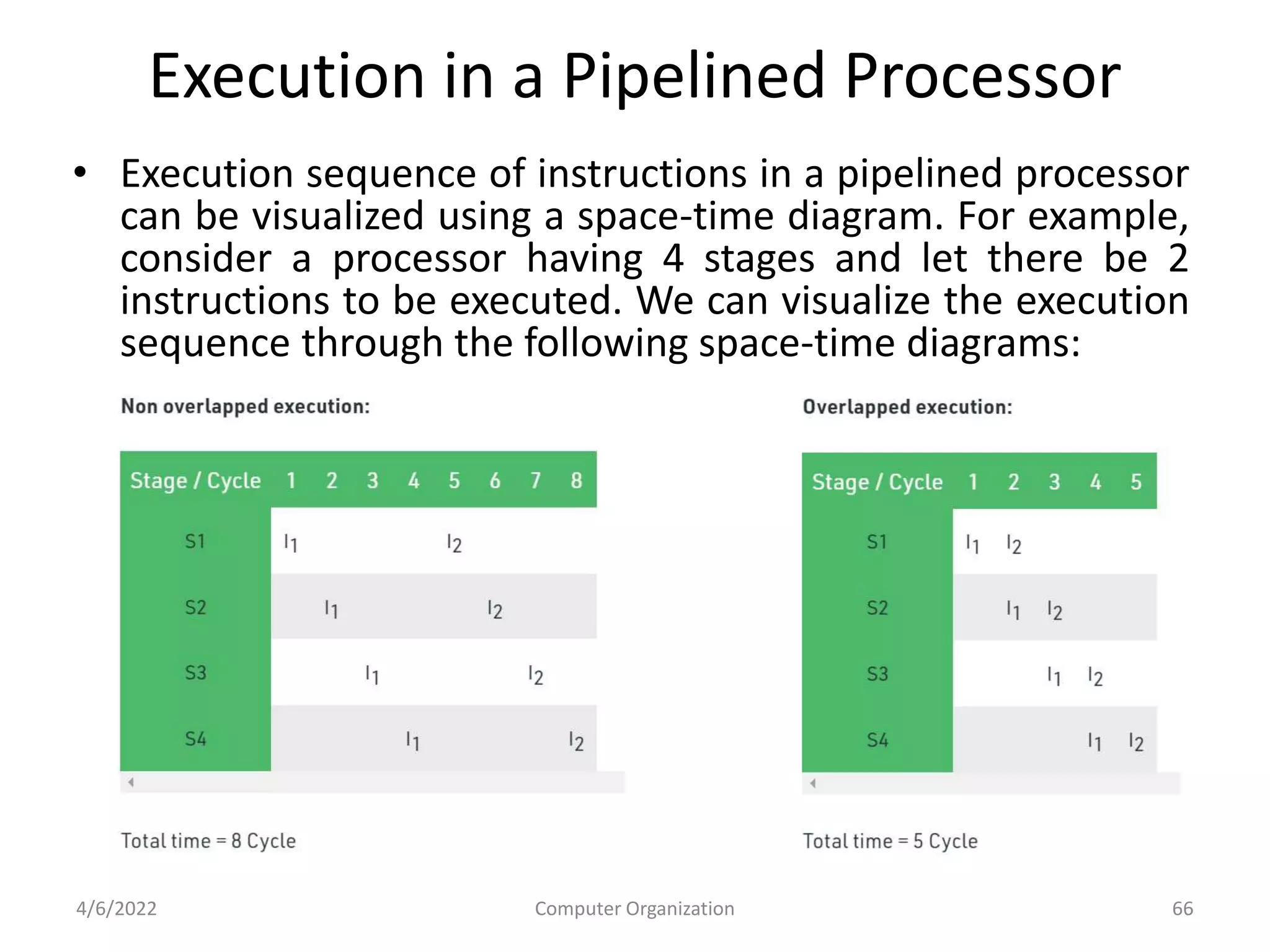
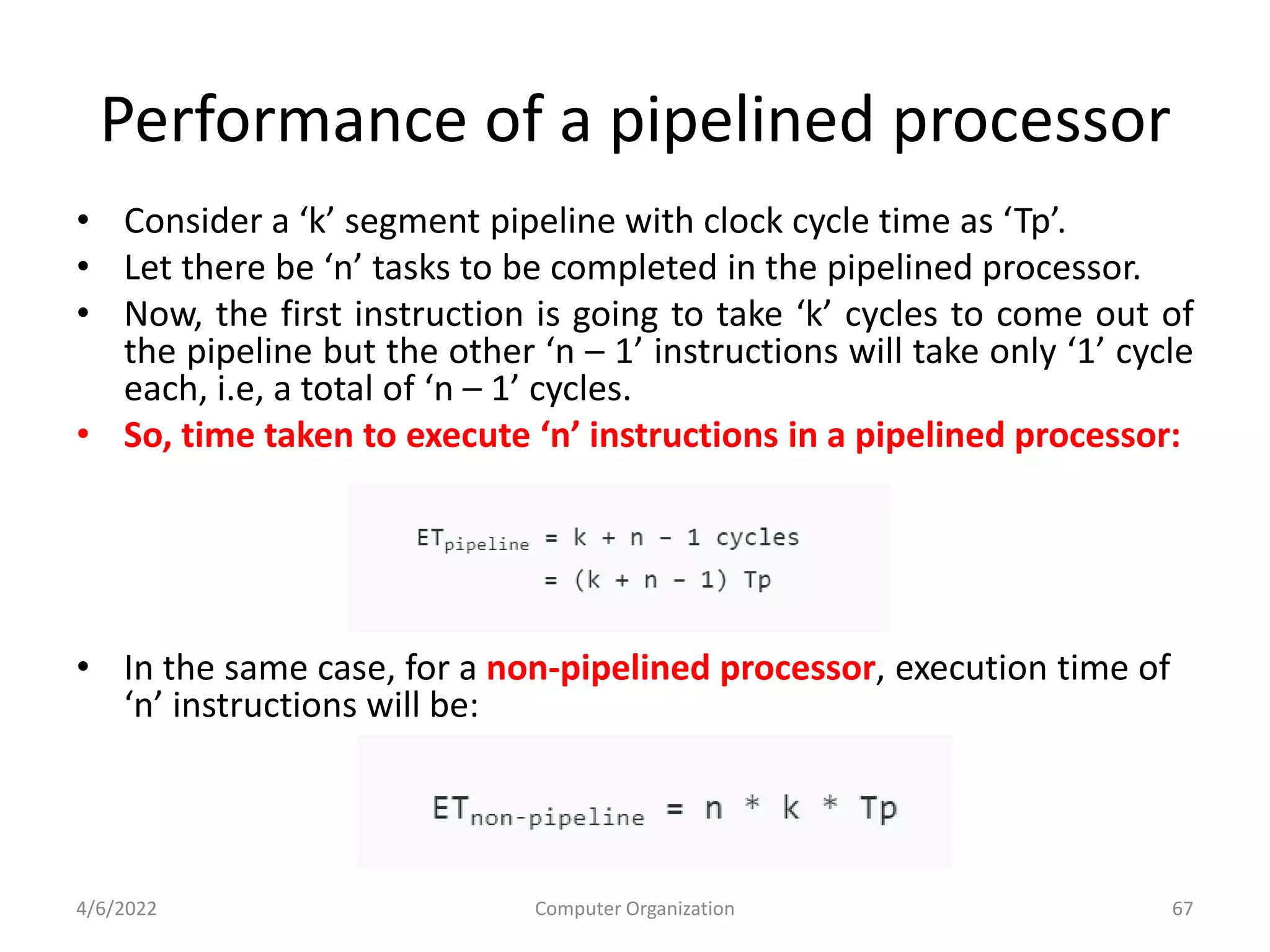
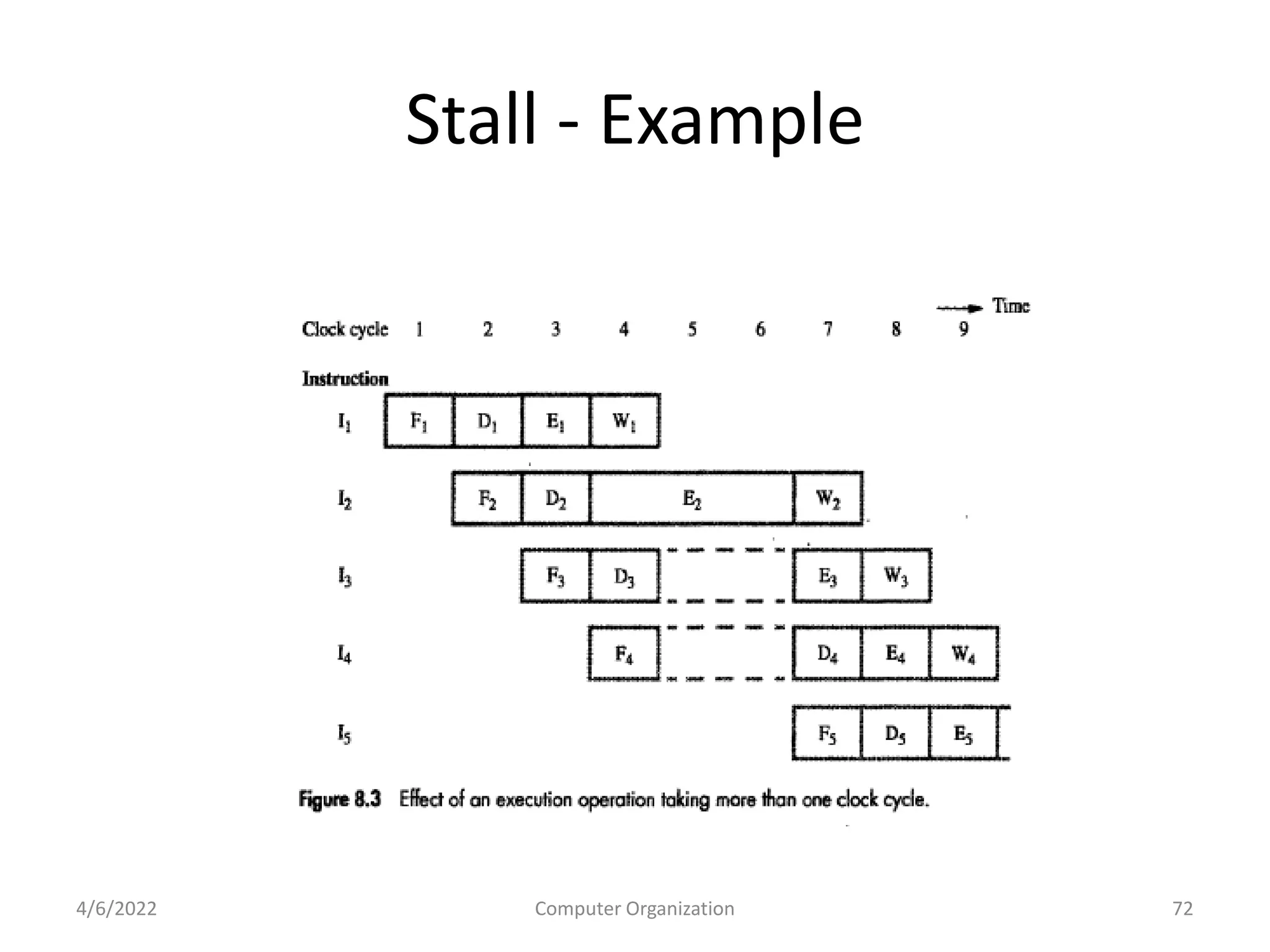
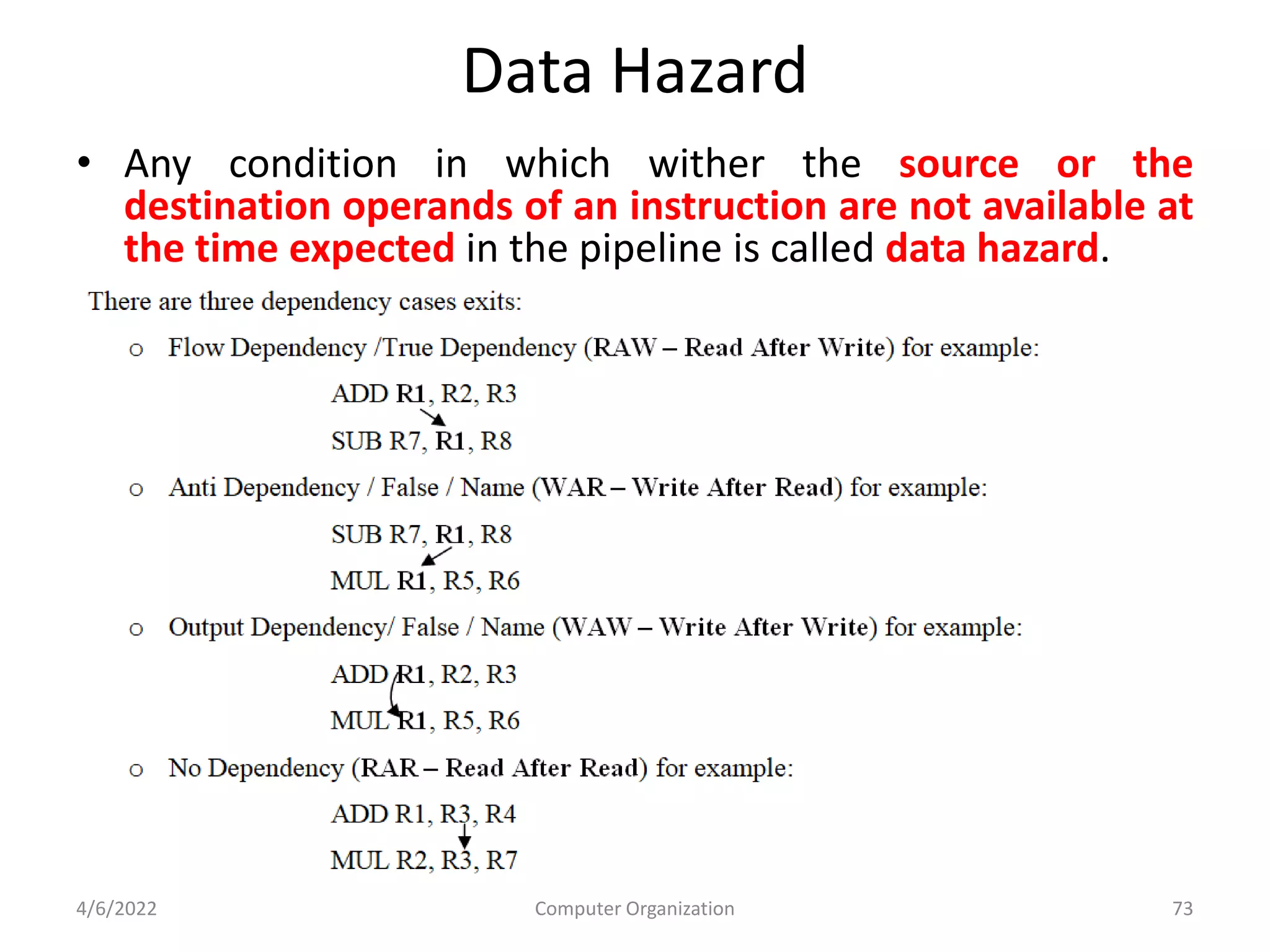
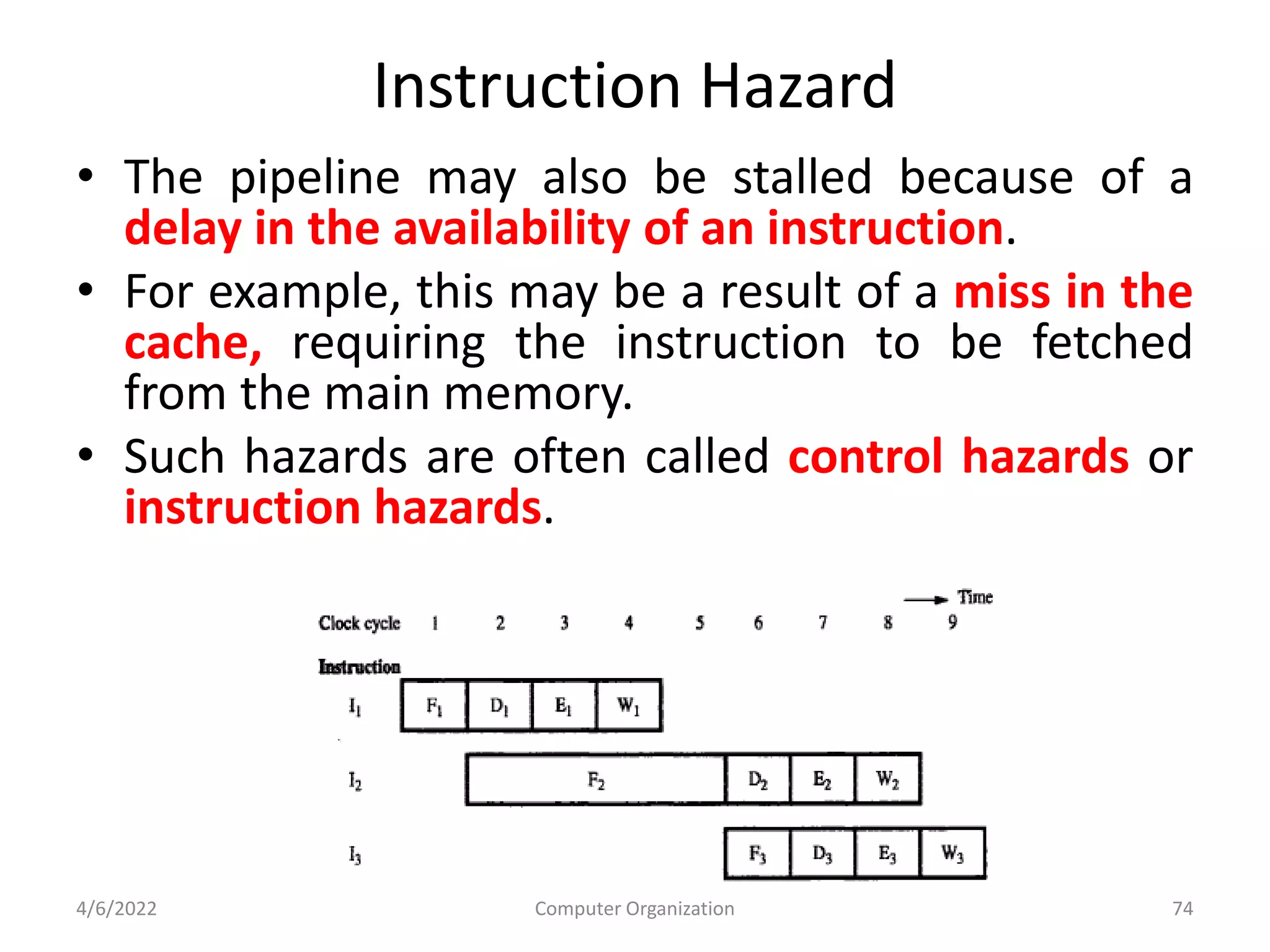
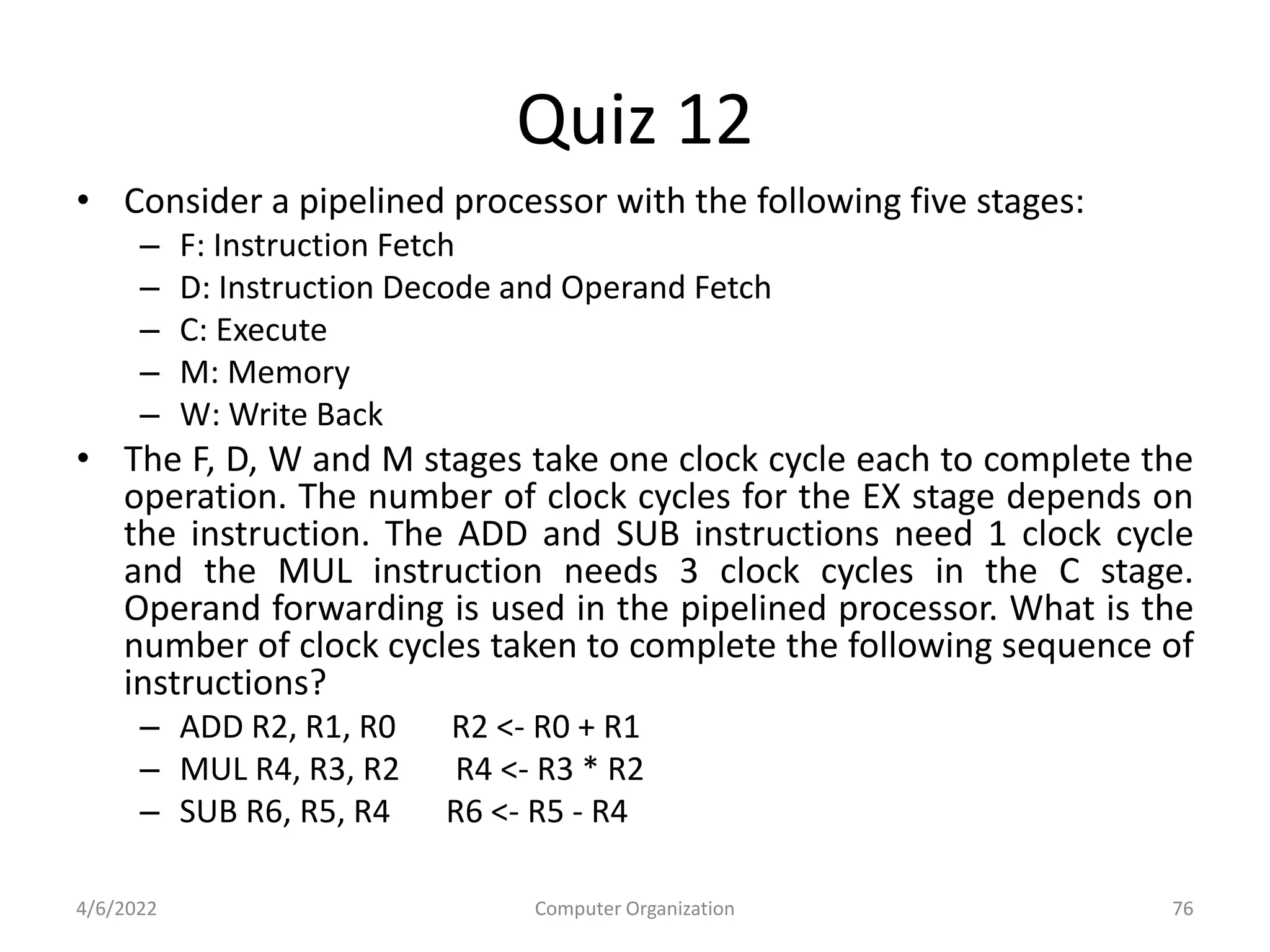
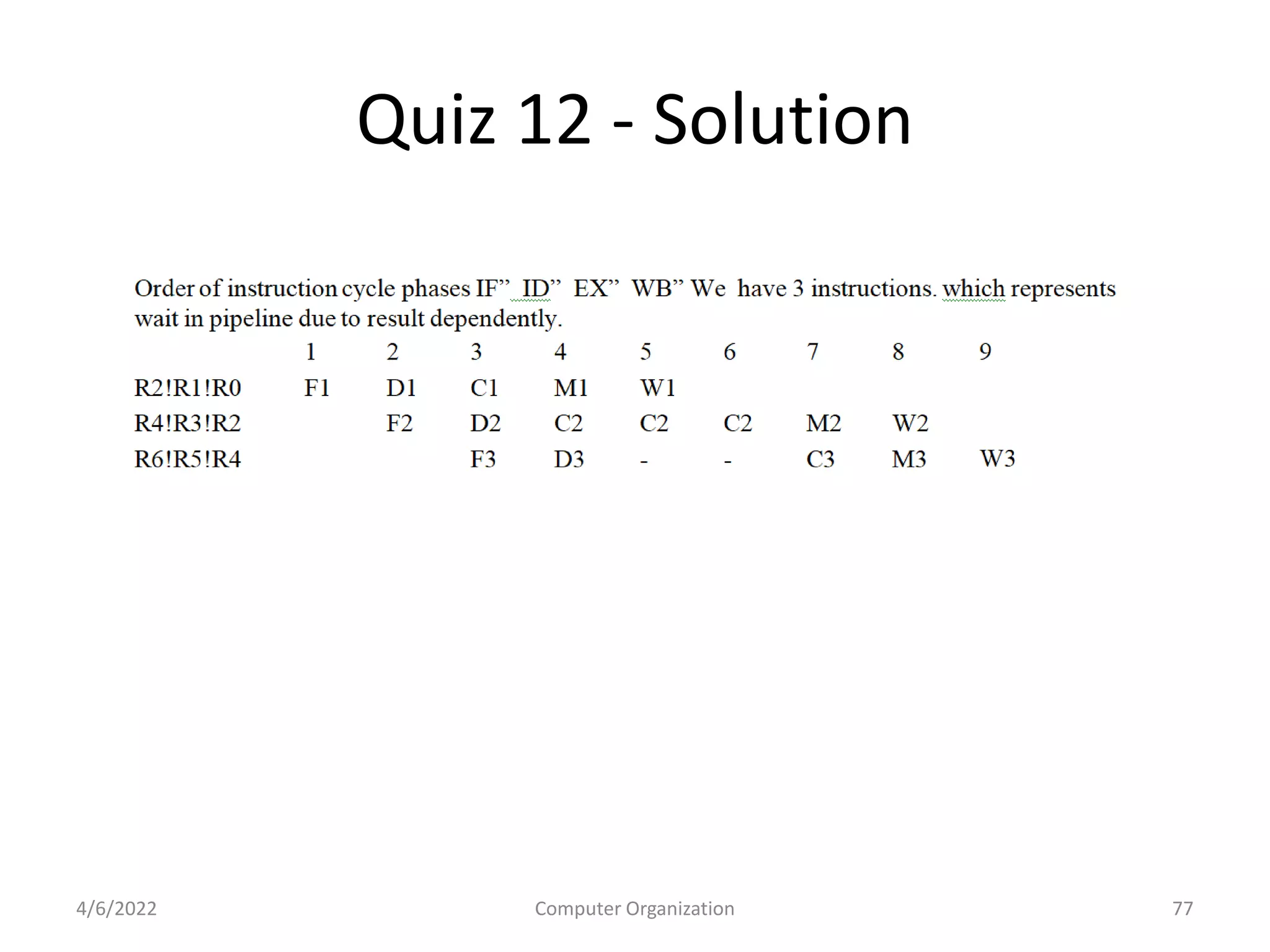
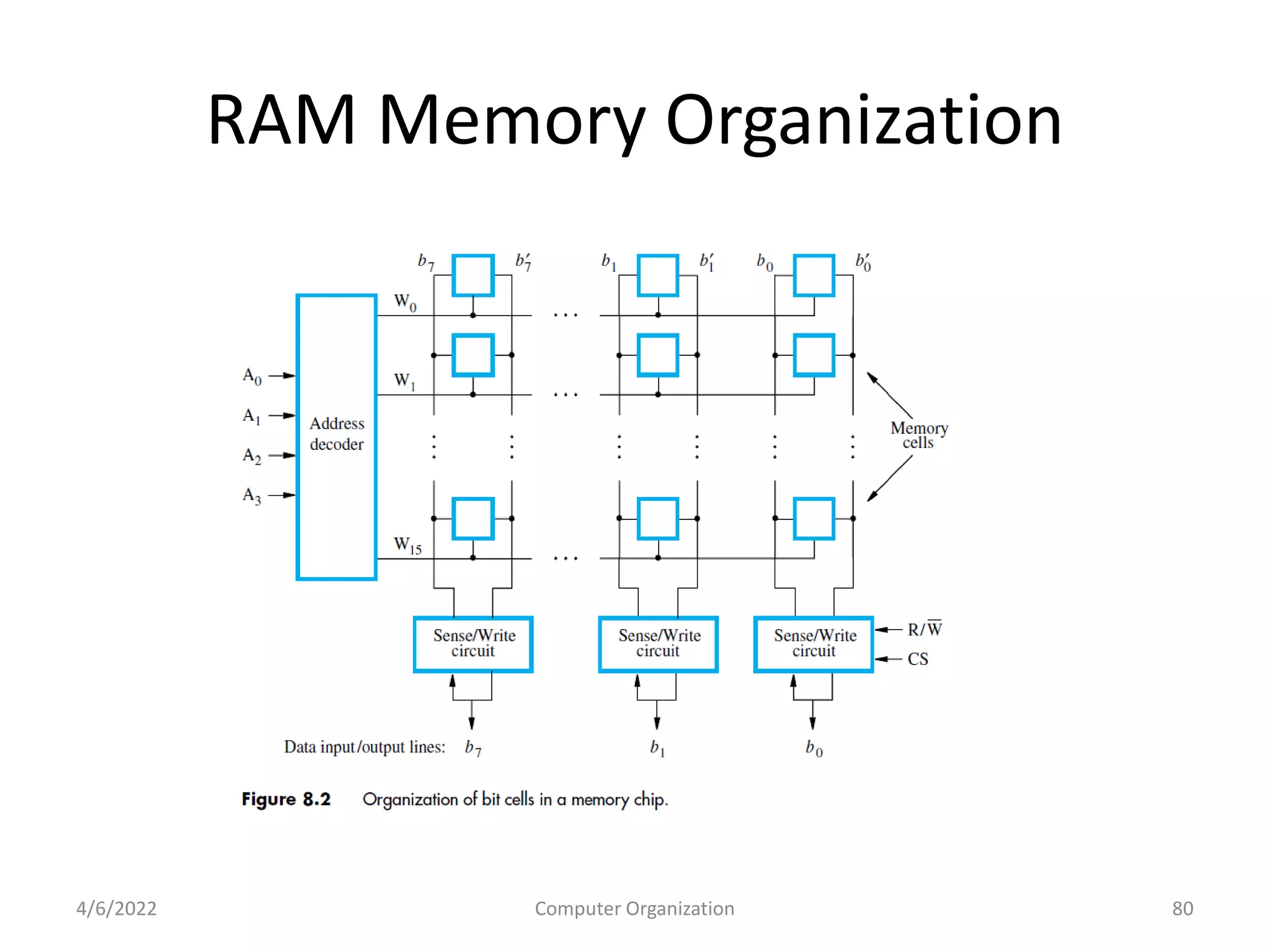
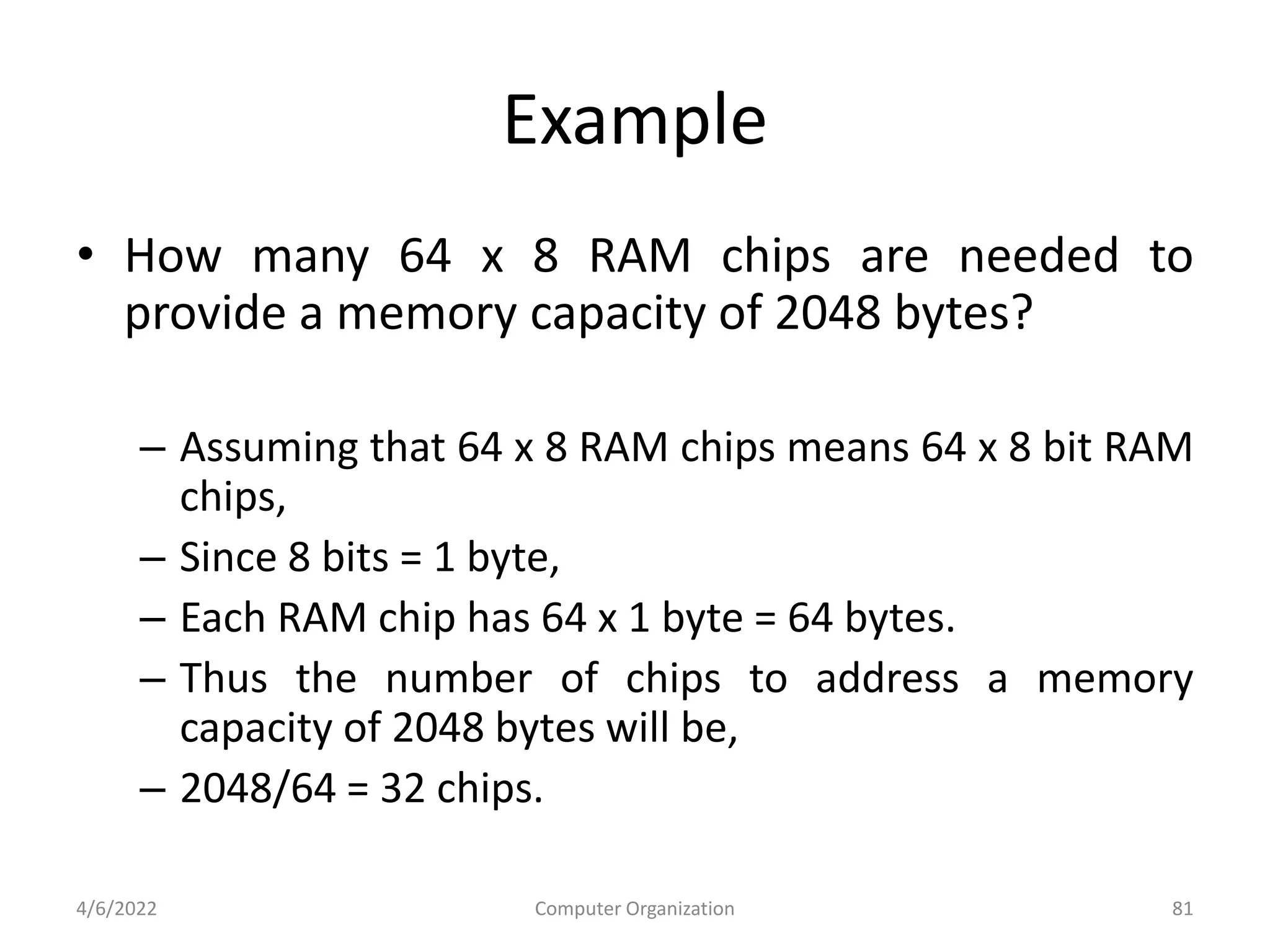
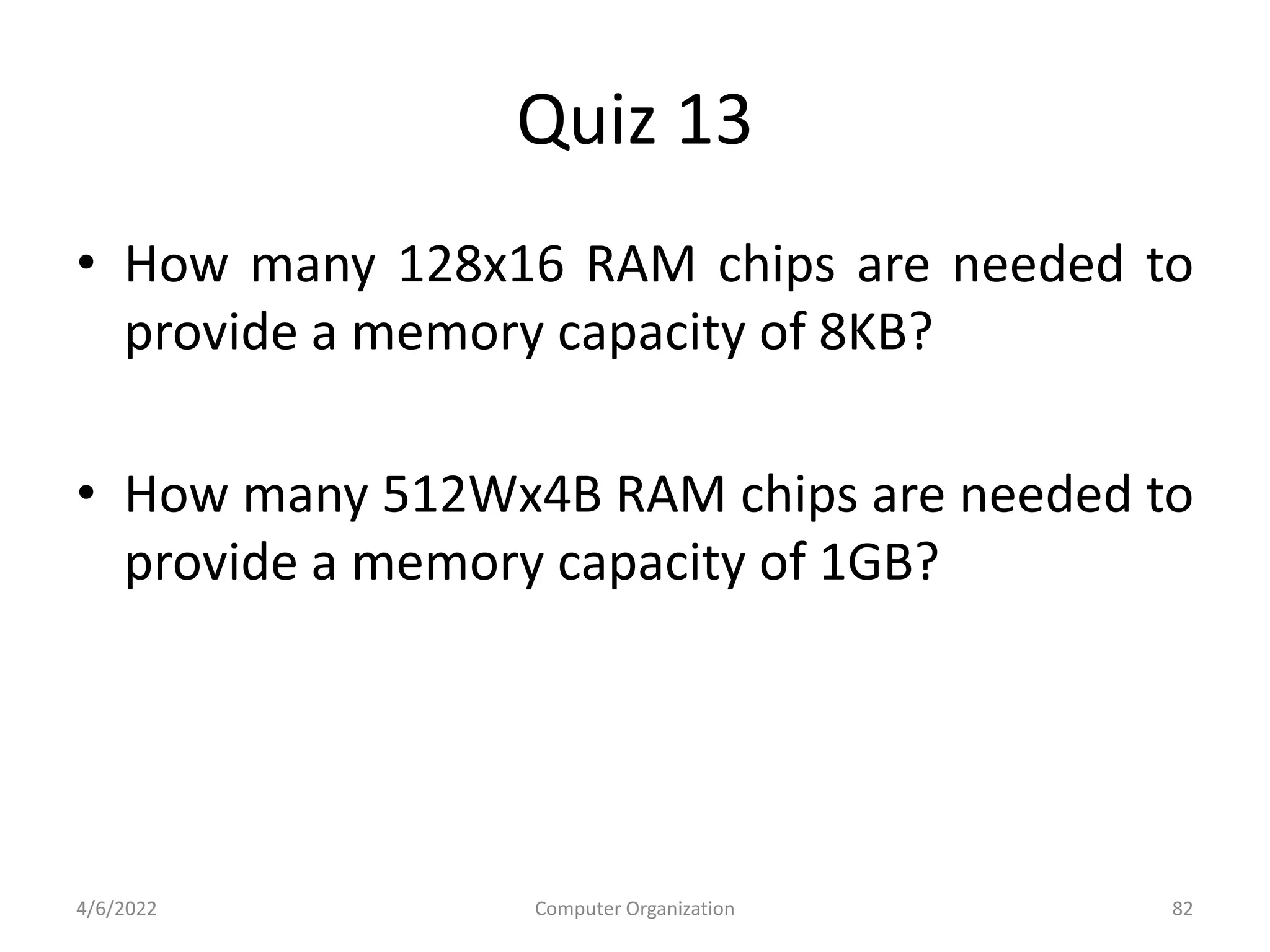
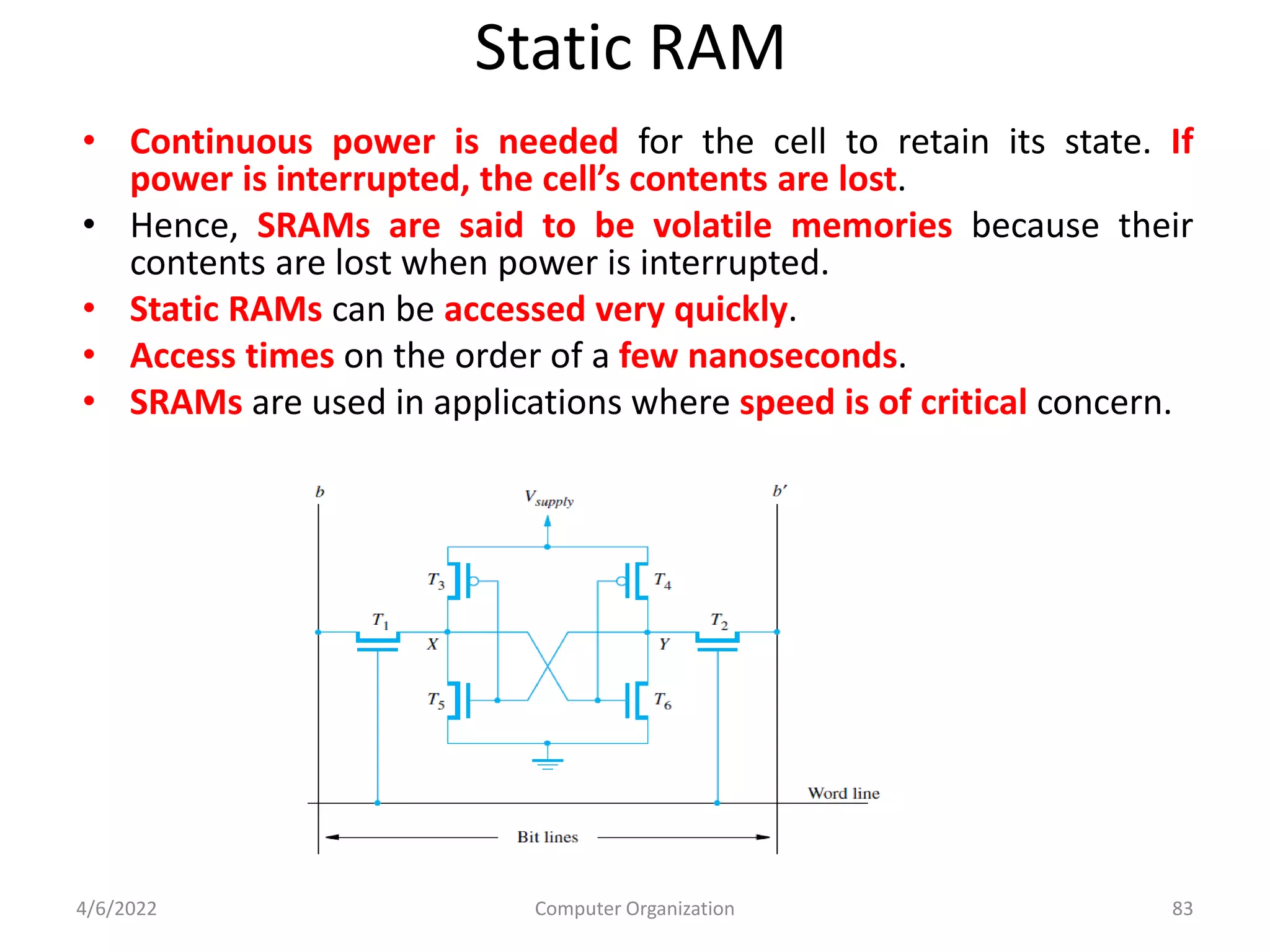
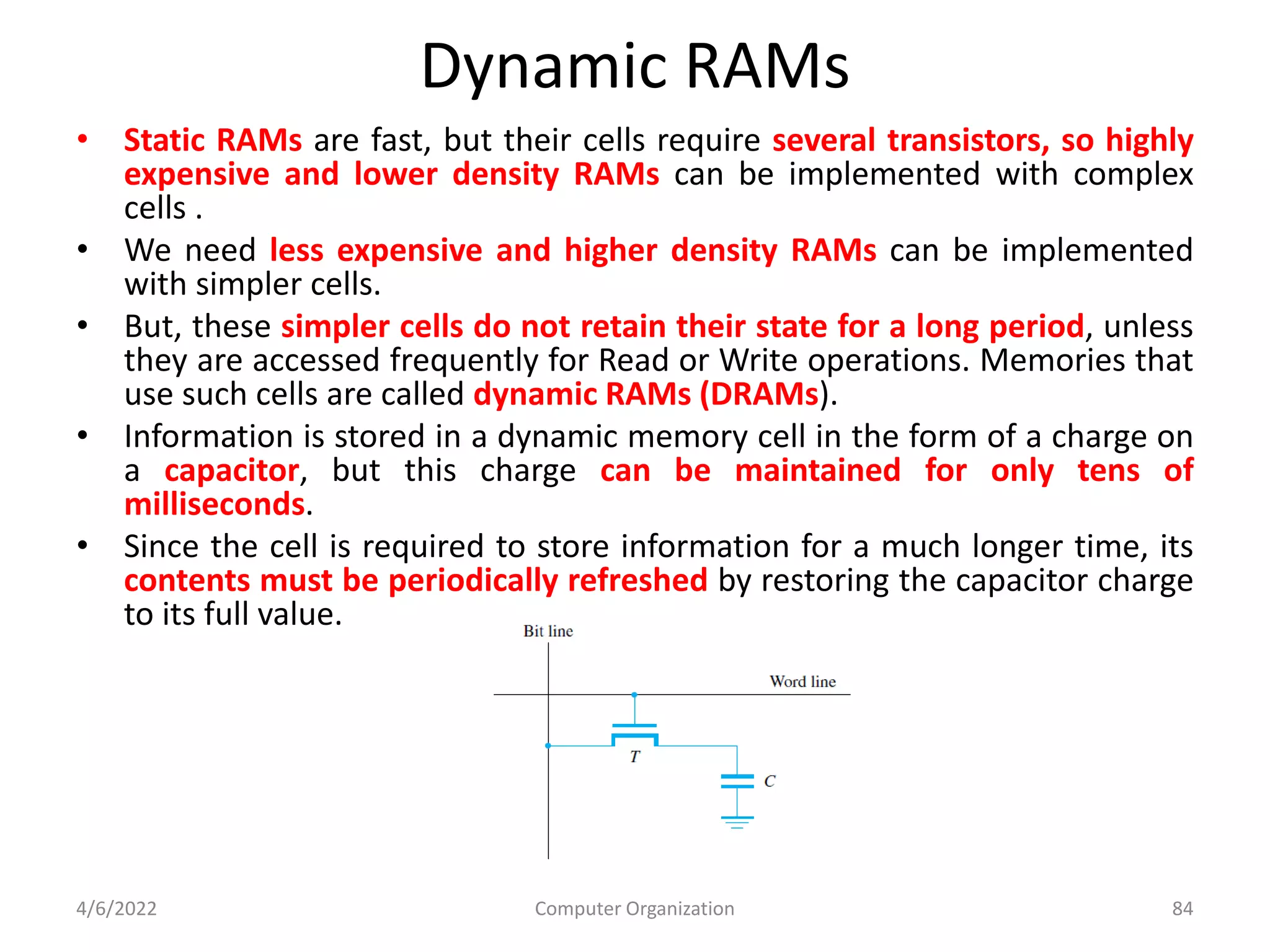
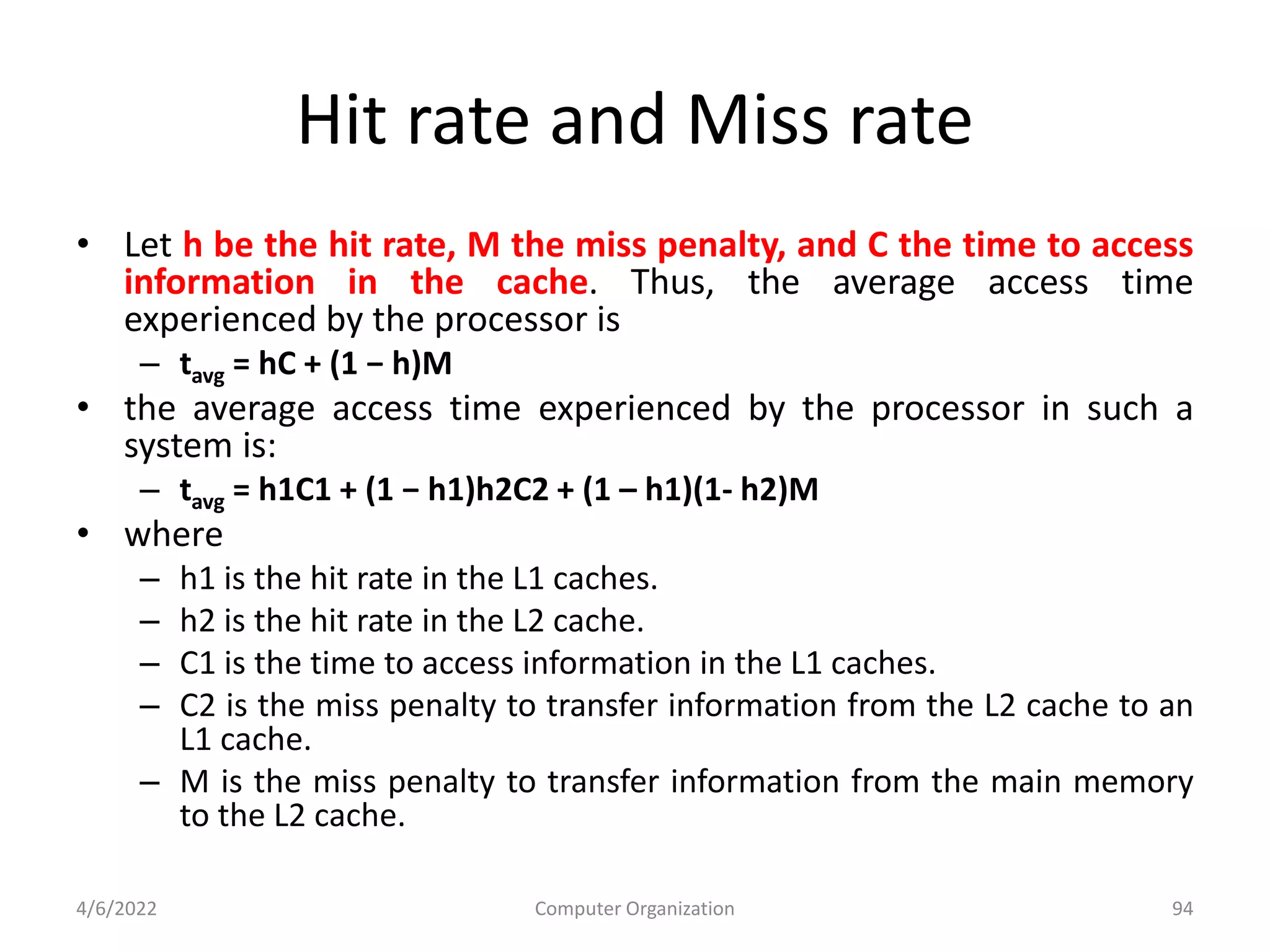
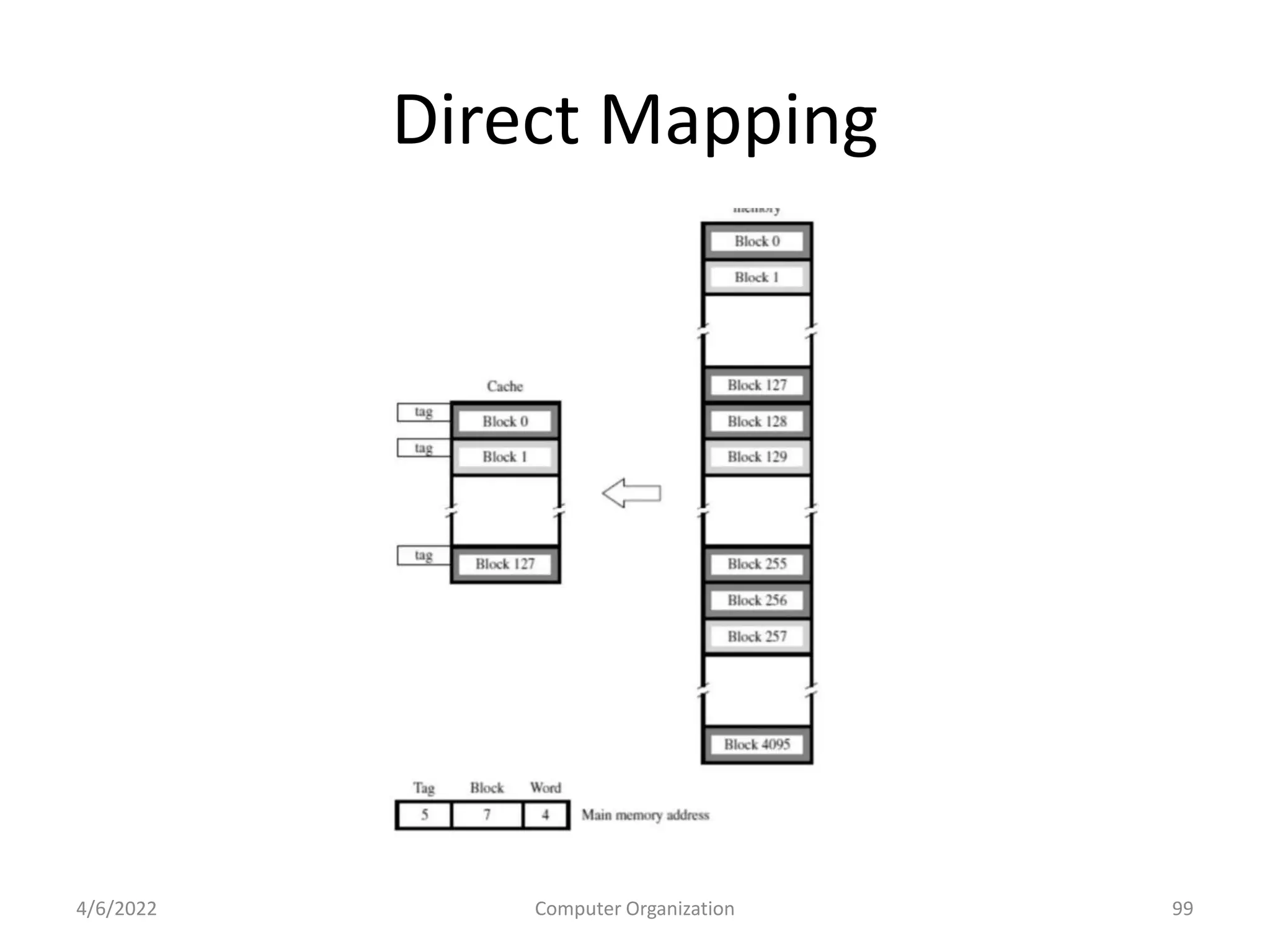
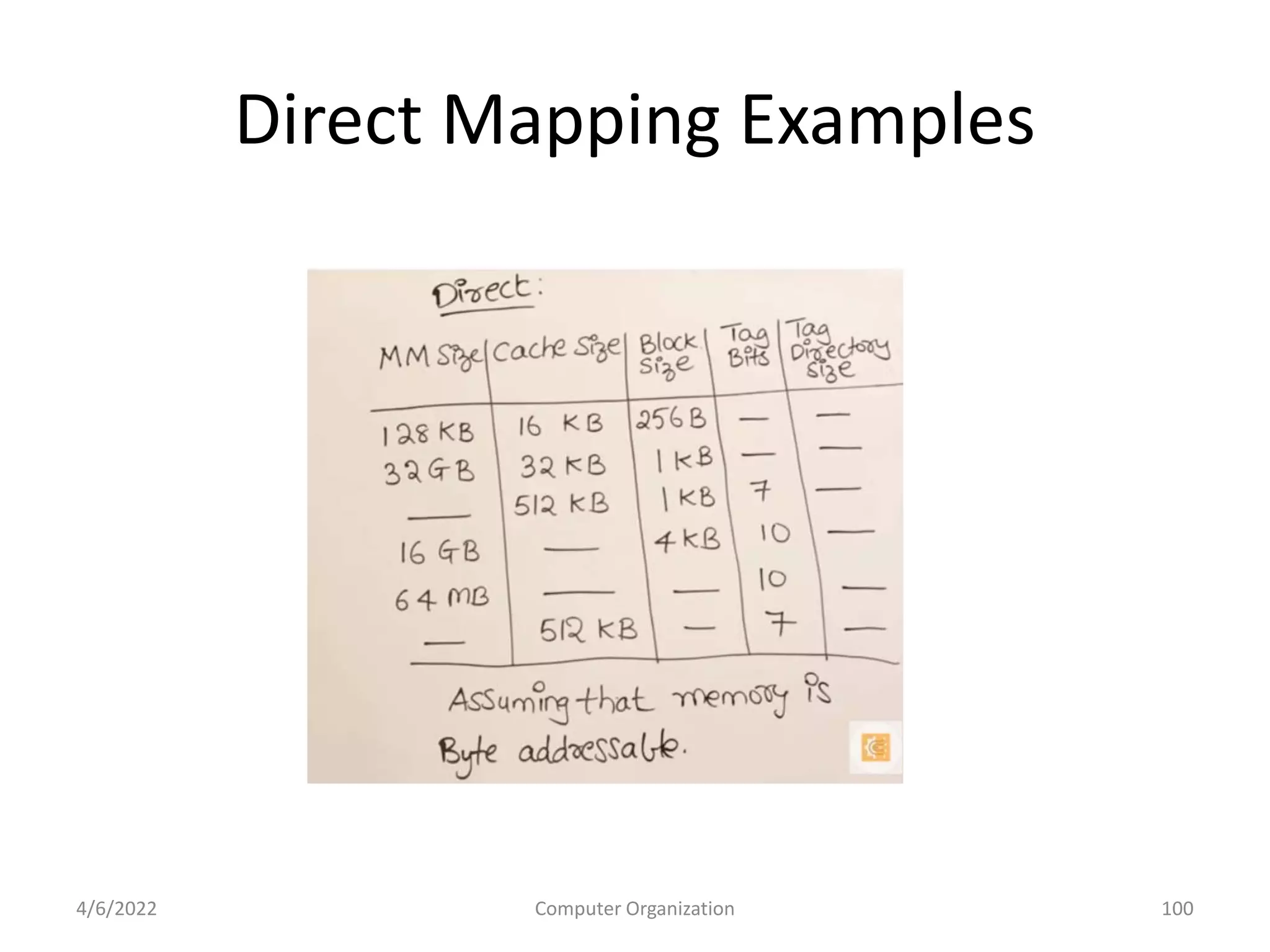
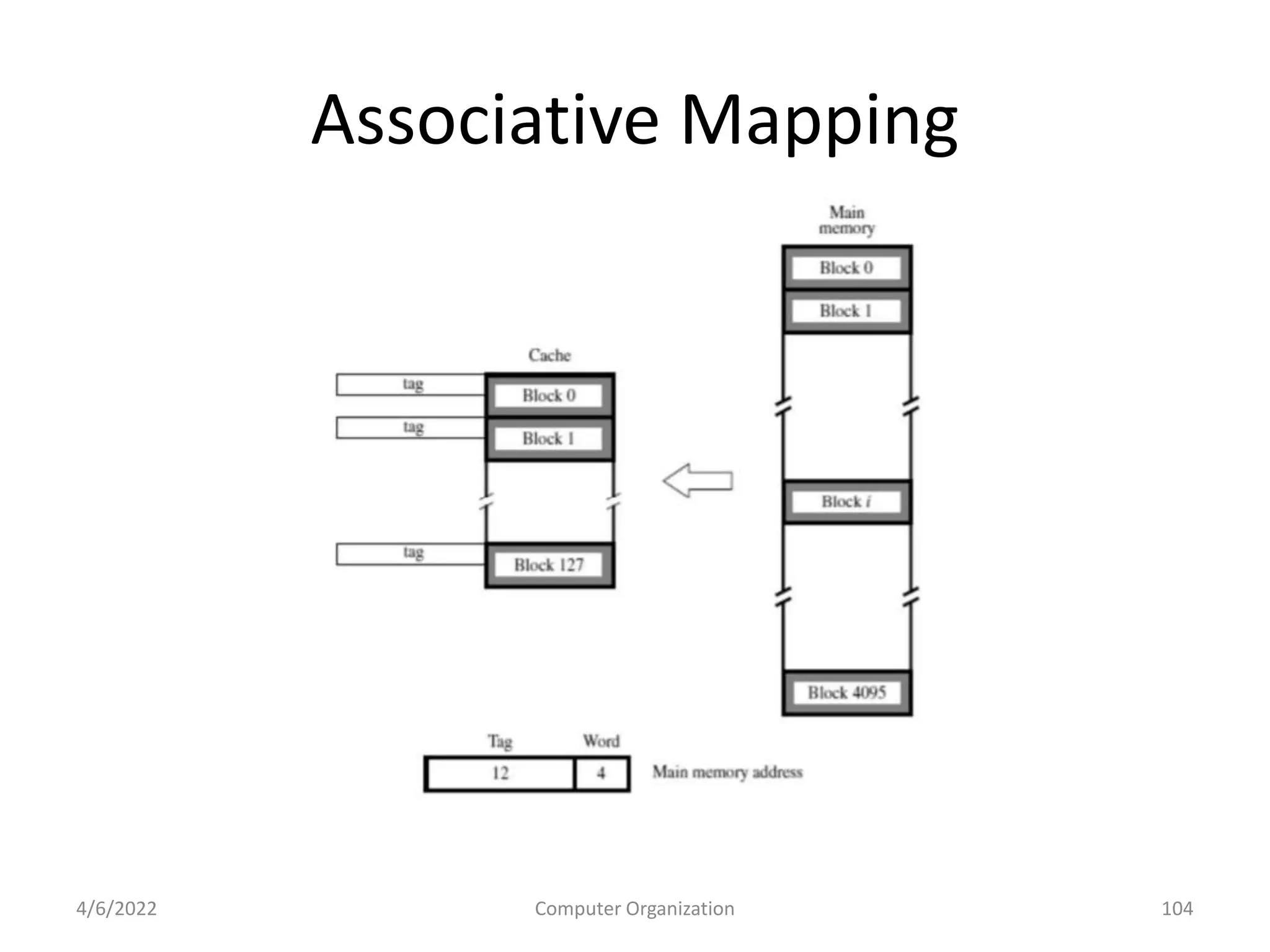
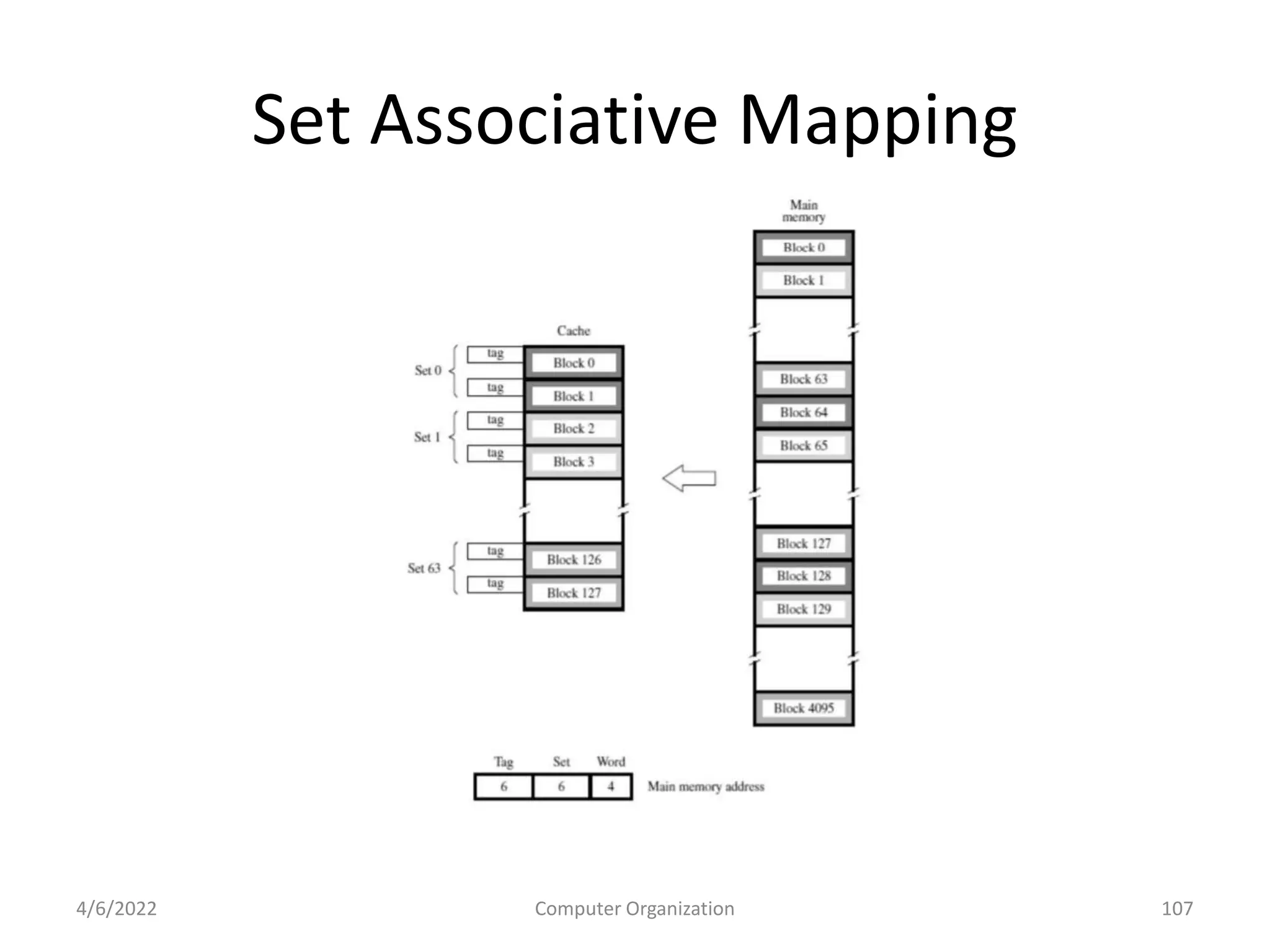
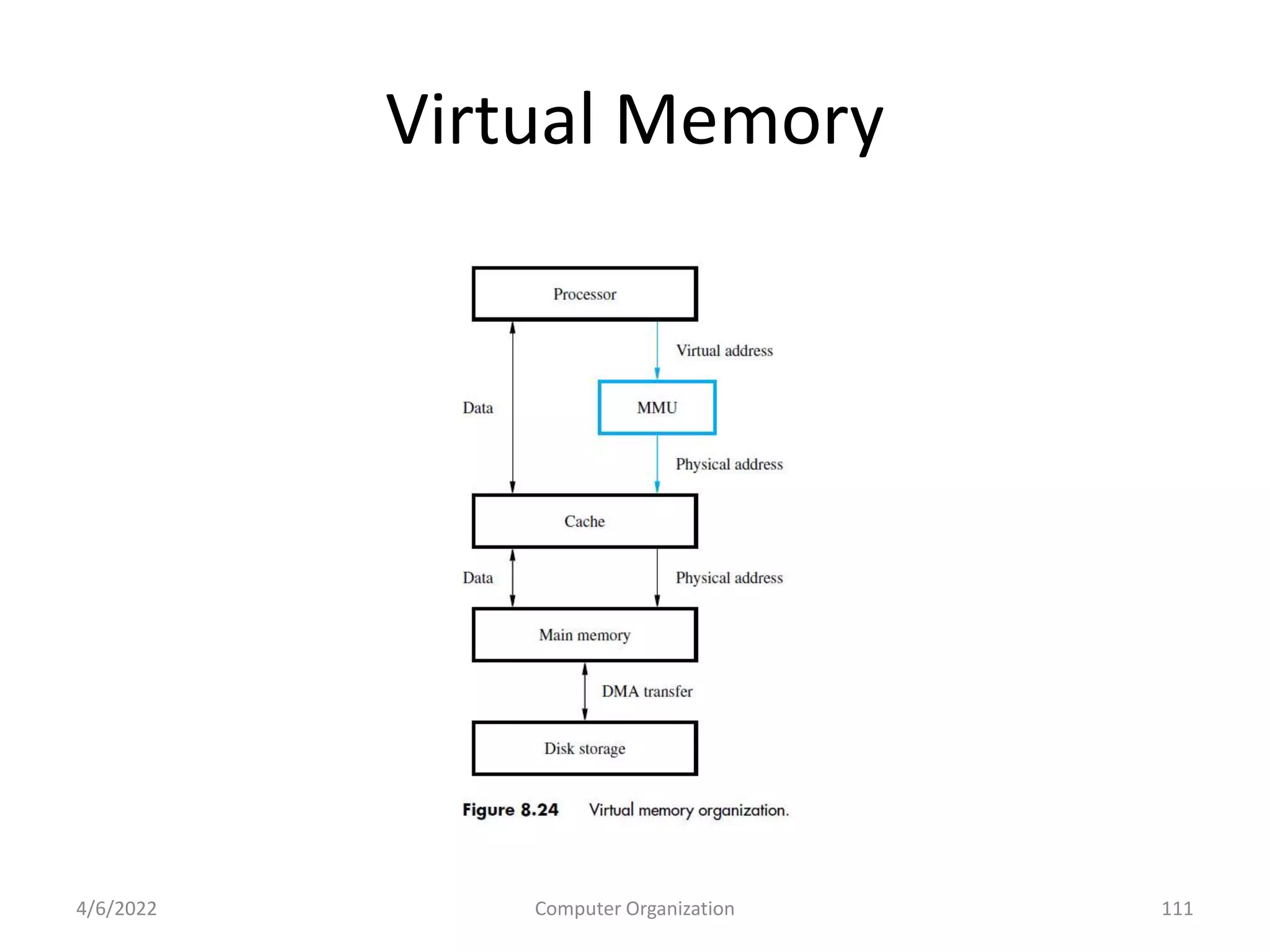
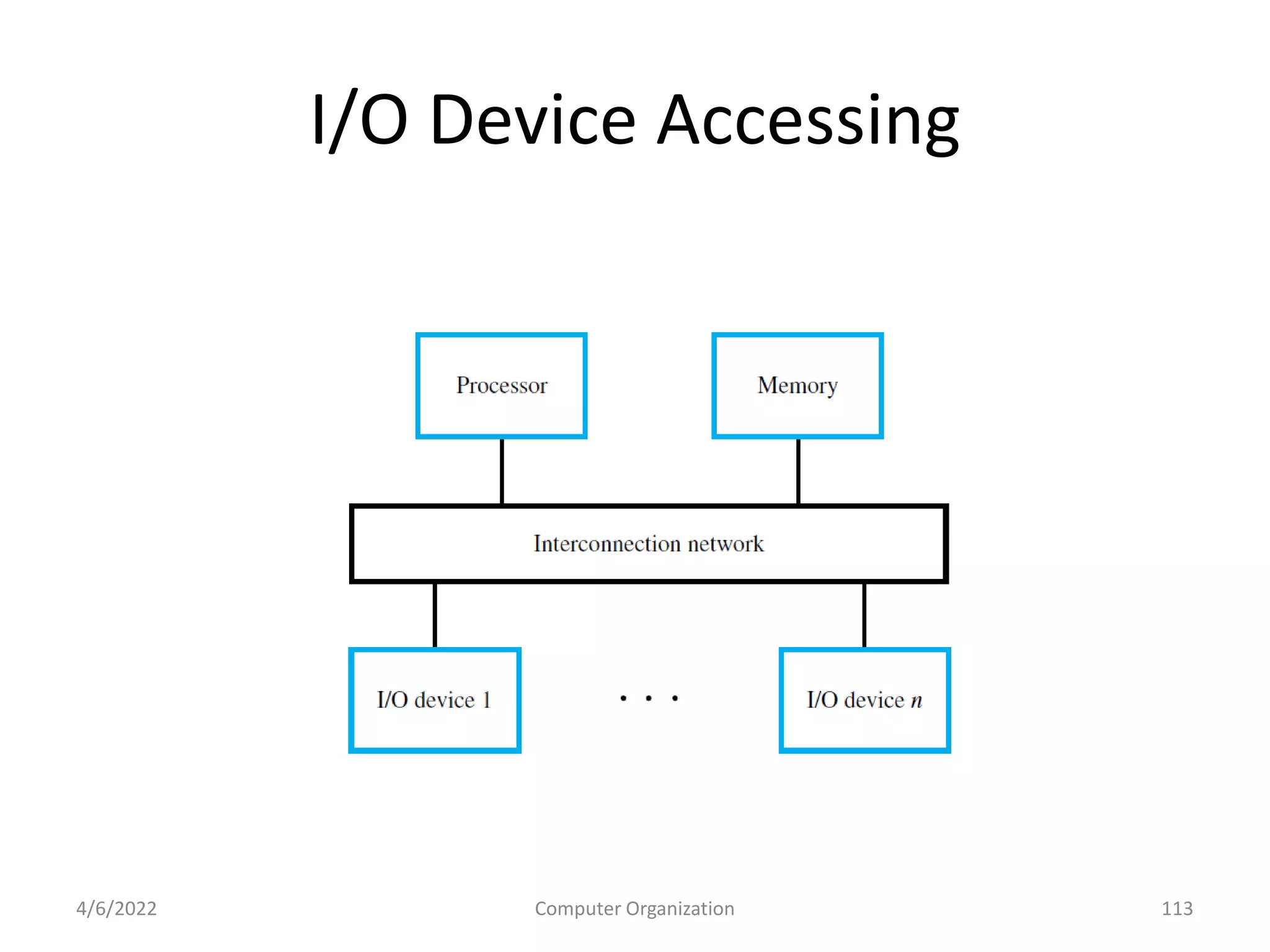
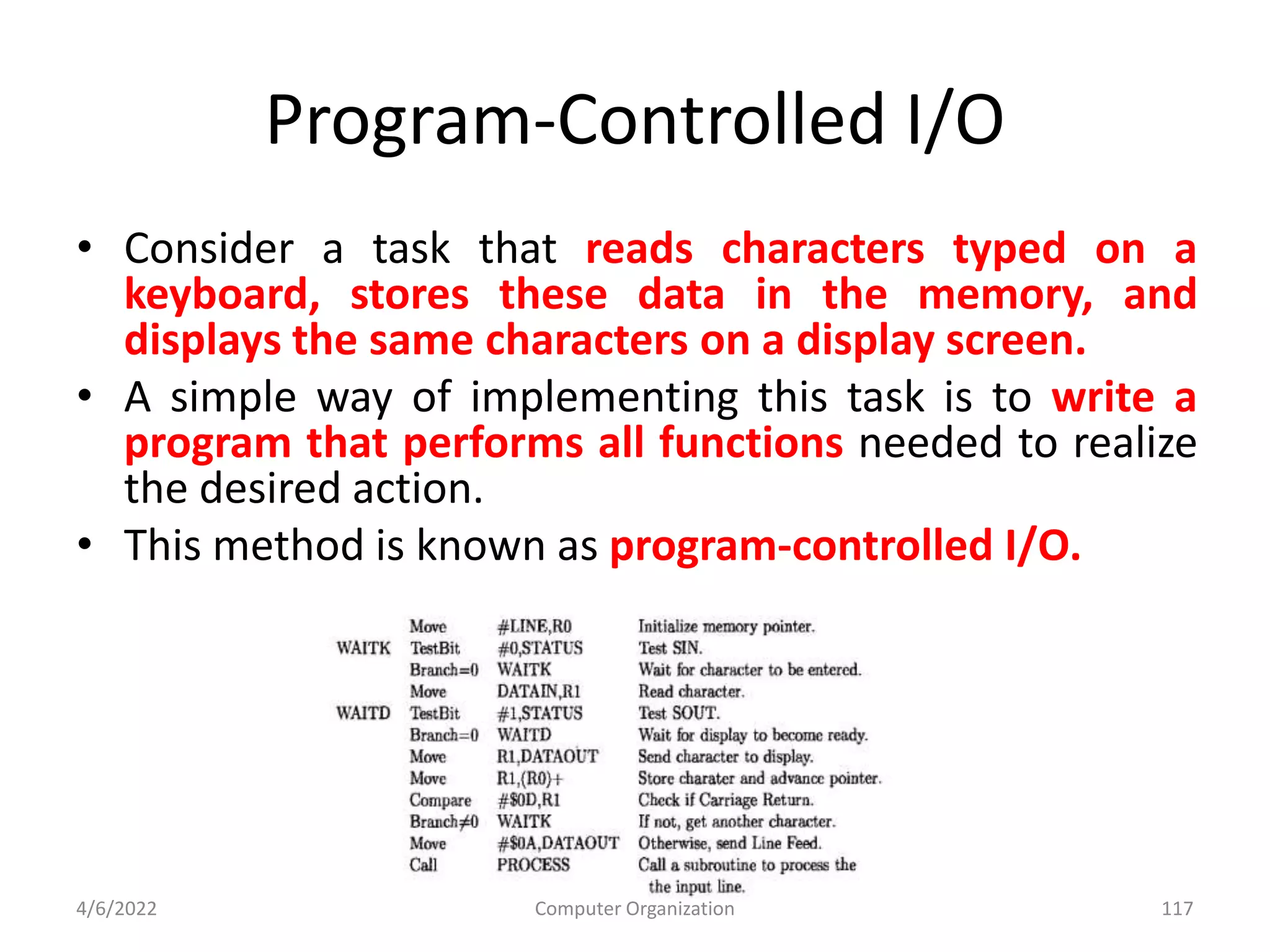
This document provides an overview of computer organization. It discusses the functional units of a computer including taking input, storing data, processing data, outputting information, and controlling workflow. It also describes the components of a processor such as the instruction register, program counter, memory address register, and general purpose registers. Finally, it examines concepts like pipelining, where instructions are broken down into stages to allow simultaneous execution and improve performance compared to non-pipelined processors.