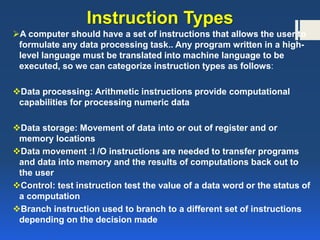
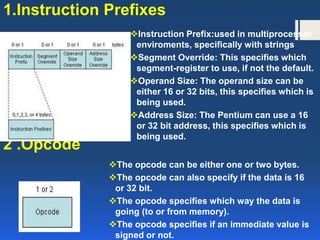
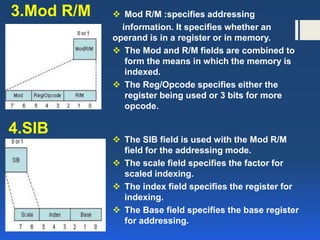
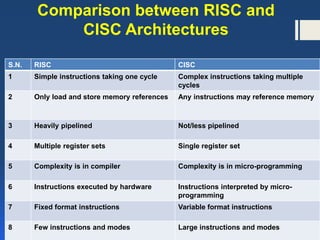
The document discusses instruction formats and set architectures, including the characteristics of Complex Instruction Set Computer (CISC) and Reduced Instruction Set Computer (RISC). It explains the structure of machine instructions comprising operation codes, operand references, and their addressing modes, along with the details of Pentium's variable-length instruction format. The comparison highlights the advantages and disadvantages of each architecture while acknowledging the convergence between CISC and RISC in modern processors.