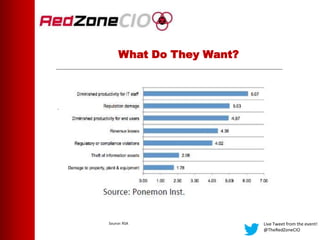
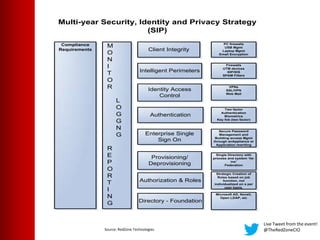
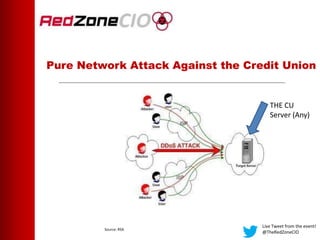
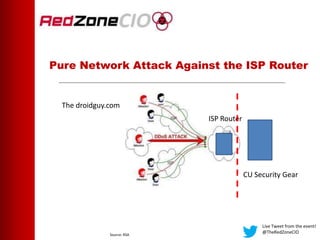
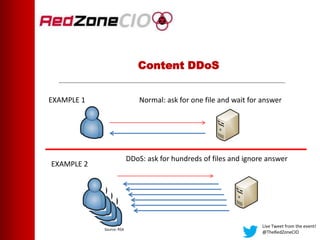
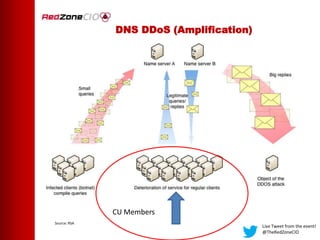
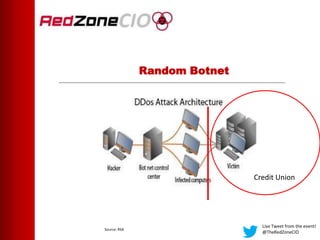
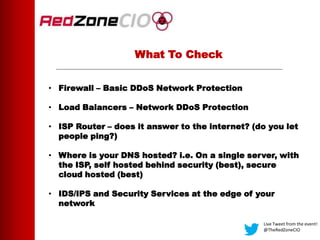
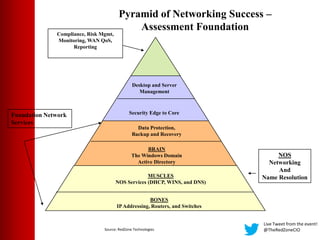
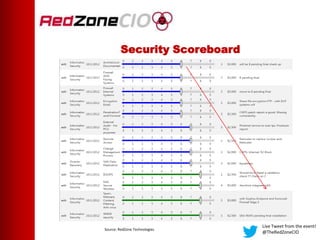
This document summarizes a virtual event about preventing DDoS attacks against credit unions. The event covers 5 types of DDoS attacks and discusses practical steps credit unions can take to prepare for and prevent attacks. Presenters from RedZone Technologies discuss reviewing a credit union's security portfolio, identifying gaps, and developing a long-term investment roadmap to strengthen defenses against DDoS and other cyber threats. The event provides an overview of vendor solutions that can help protect against different attack types and questions attendees should consider.