The document summarizes several internet protocols used for communication over IP networks:
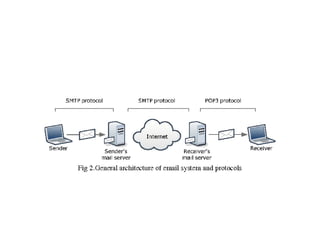
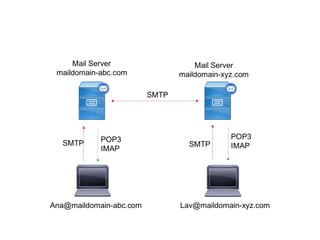
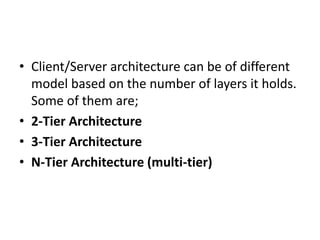
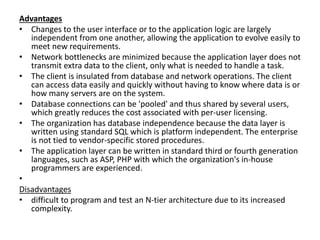
SMTP is used for email transmission and uses TCP port 25. It allows for mail, recipient, and data commands in a transaction. POP and IMAP are used for retrieving email from servers, with POP deleting emails from the server and IMAP leaving them on the server. HTTP is the underlying protocol for the web and uses port 80. FTP uses ports 20 and 21 for data and control connections. PGP provides encryption for email. Client-server and n-tier architectures partition tasks between clients and servers. Multiple protocols are needed for complex network communication due to hardware failures, congestion, and other issues.