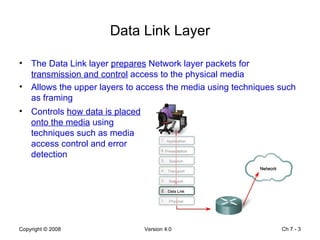
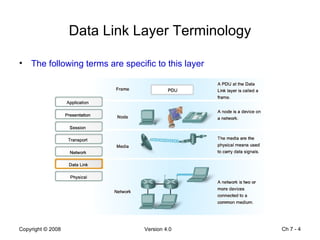
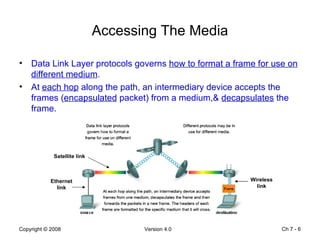
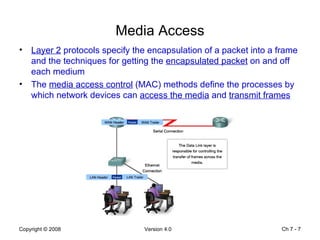
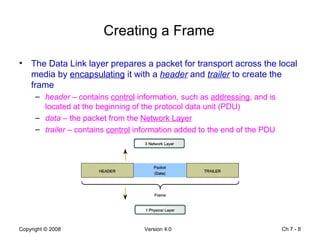
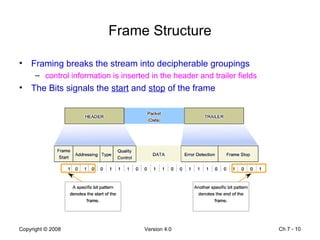
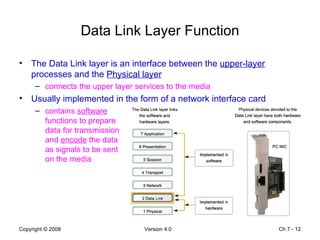
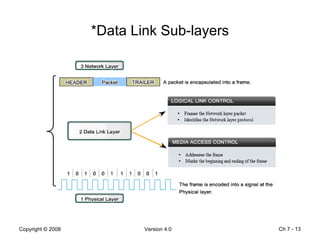
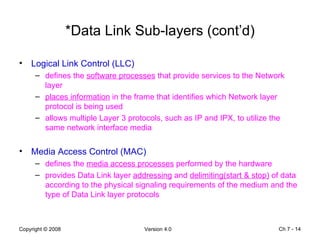
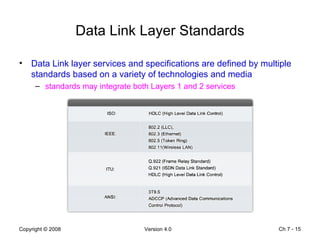
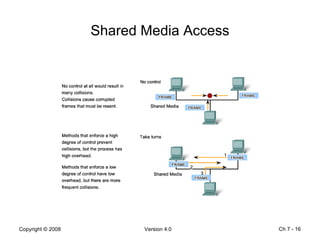
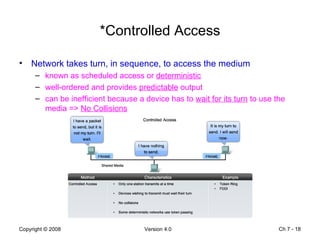
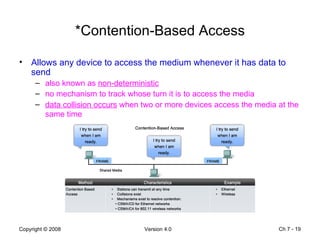
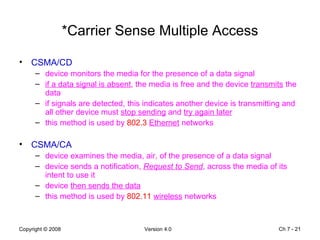
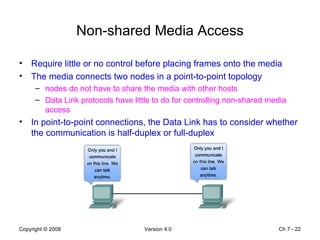
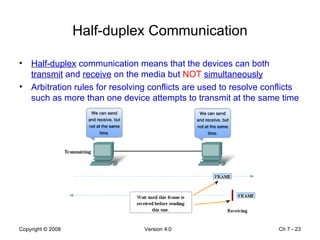
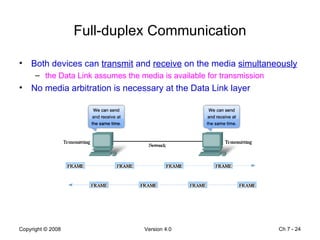
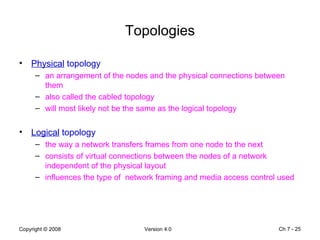
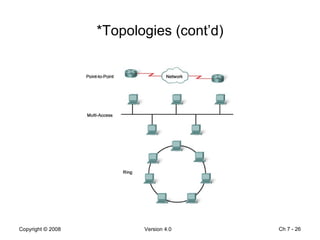
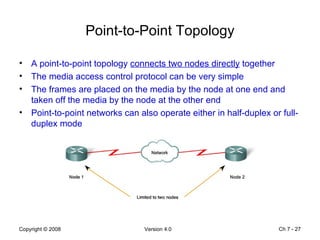
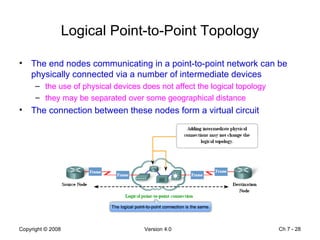
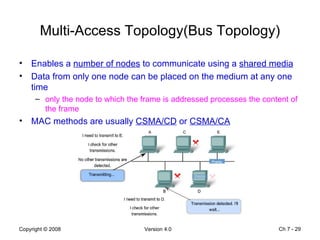
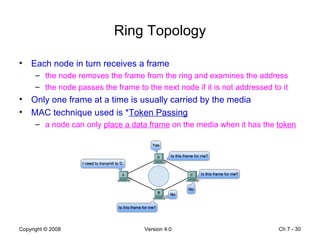
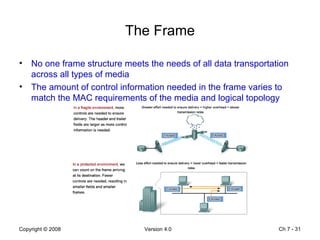
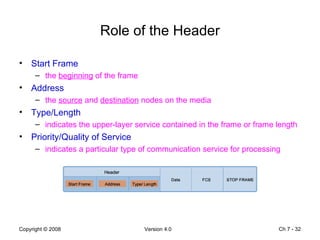
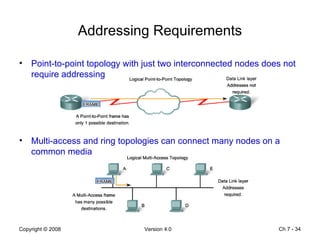
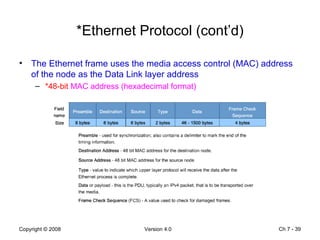
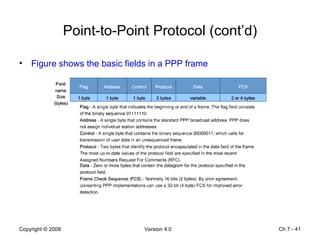
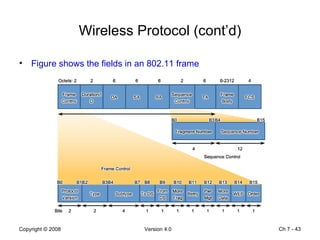
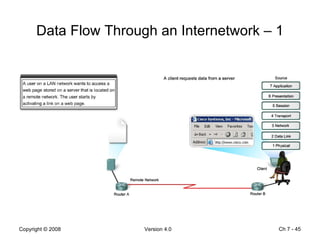
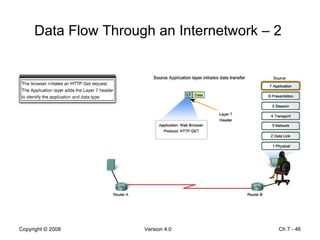
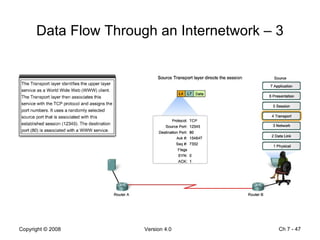
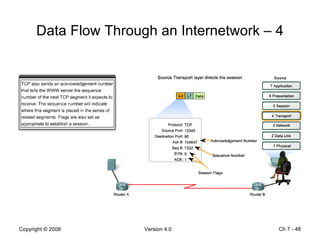
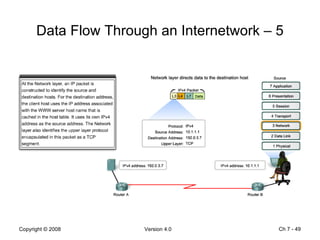
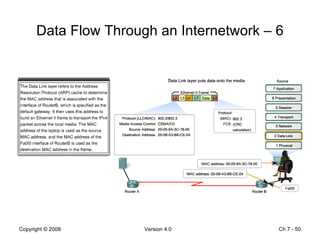
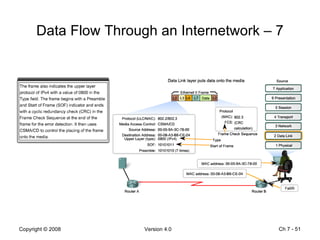
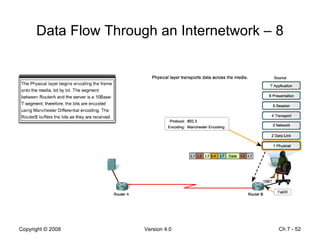
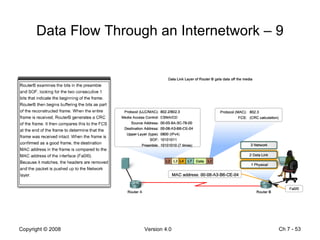
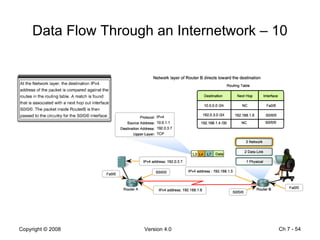
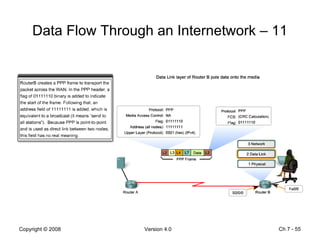
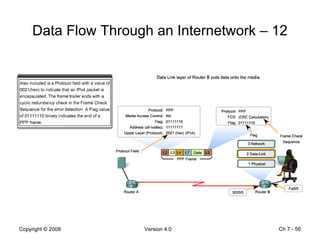
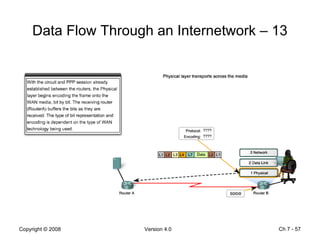
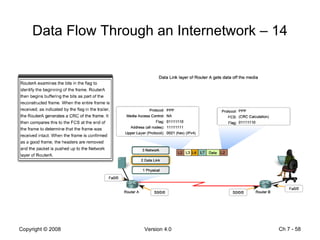
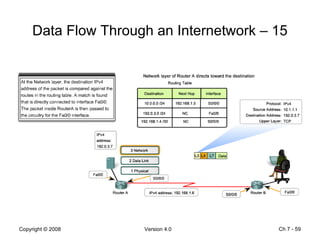
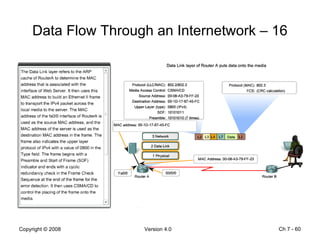
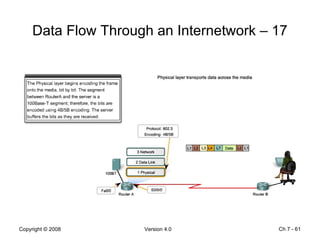
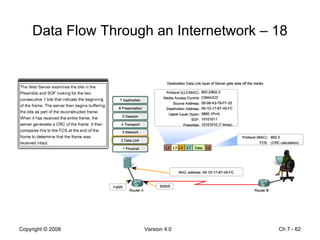
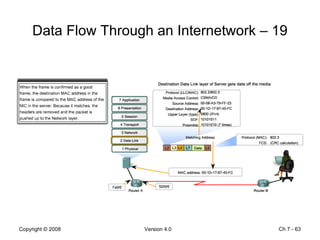
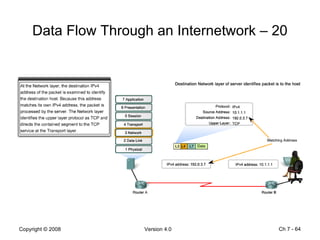
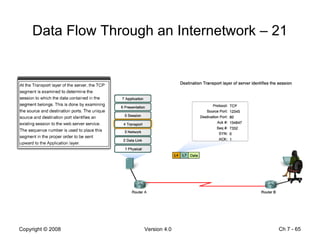
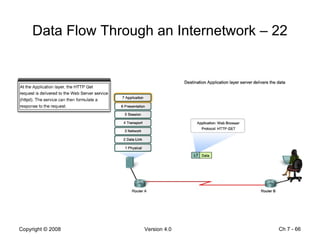
The Data Link layer prepares data for transmission by encapsulating network layer packets into frames. It controls how data is placed onto the physical media using media access control methods like CSMA/CD and token passing. Different network topologies like point-to-point, bus, and ring determine the logical connections between nodes and influence the type of media access control used. The Data Link layer frame includes a header with addressing and error detection fields, and a trailer to prepare the packet for transmission across the local media link.