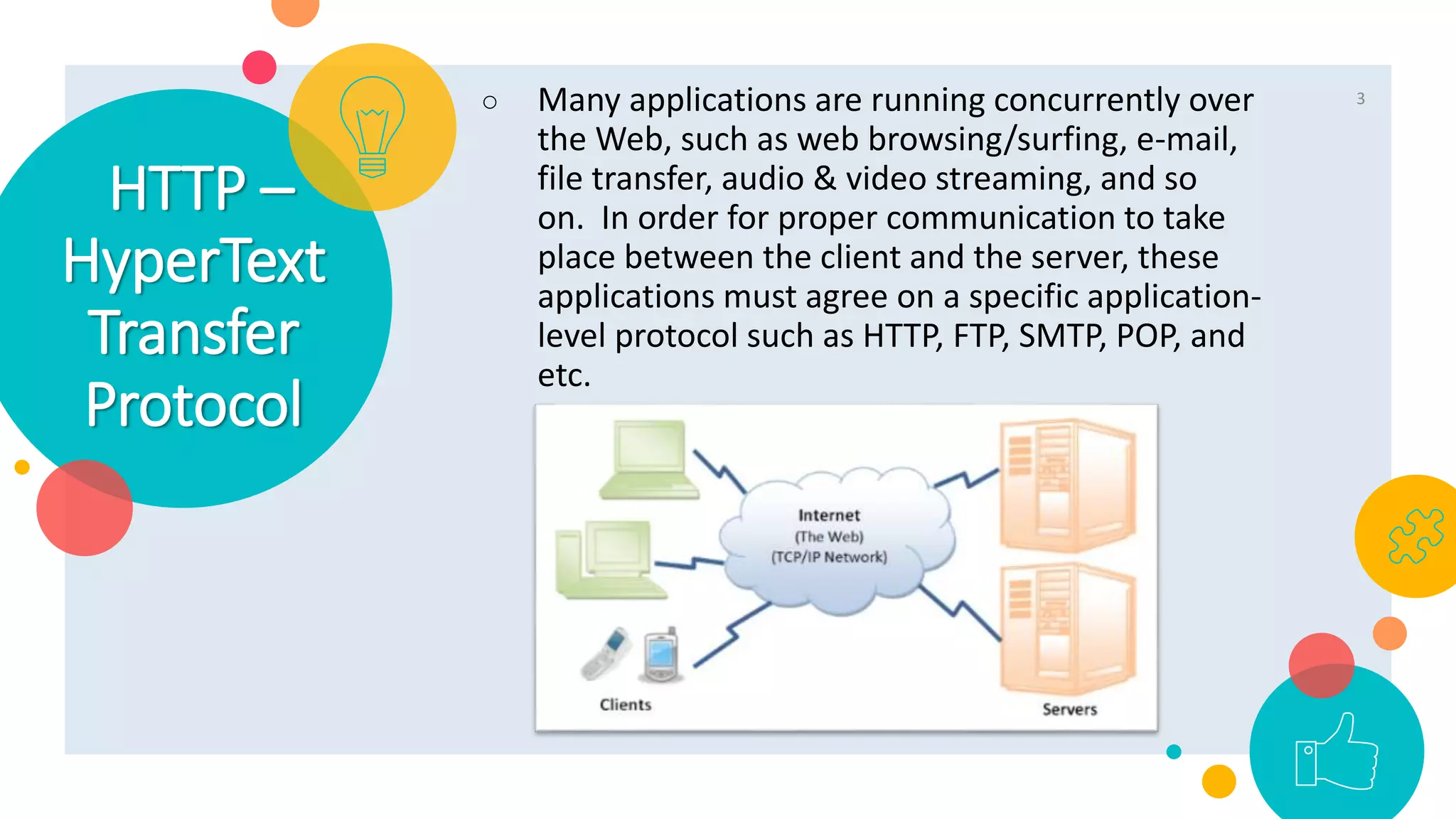
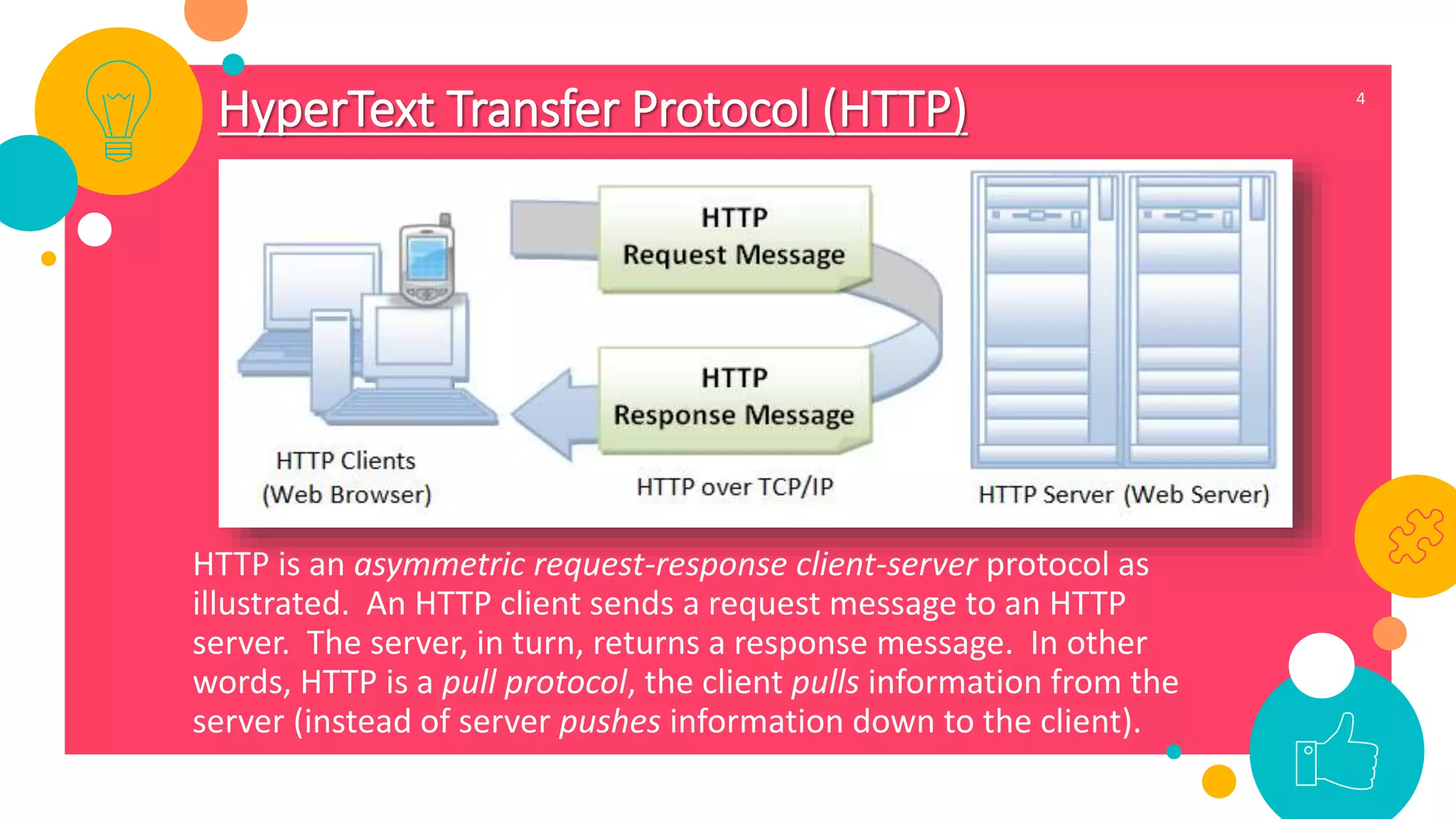
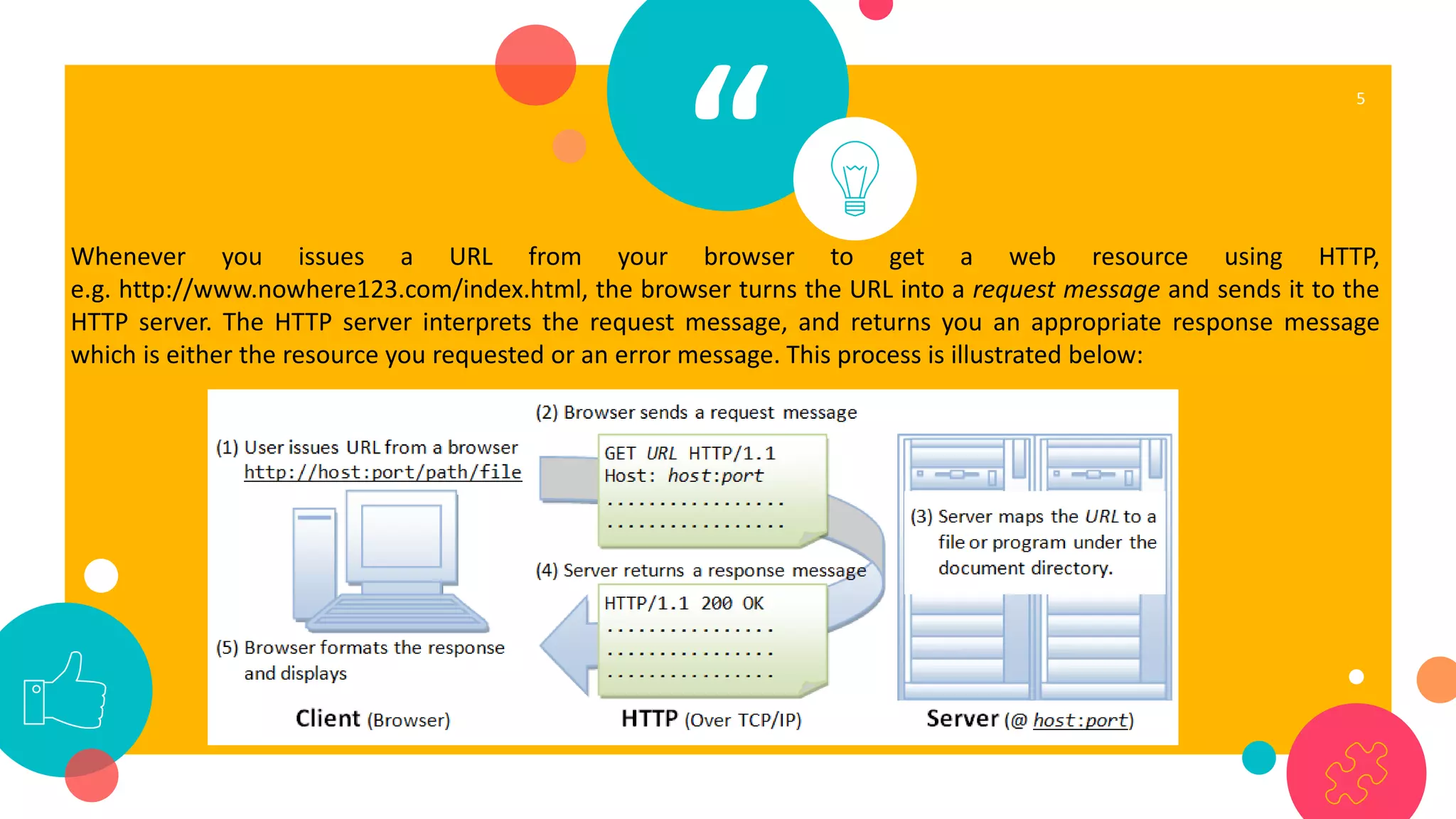
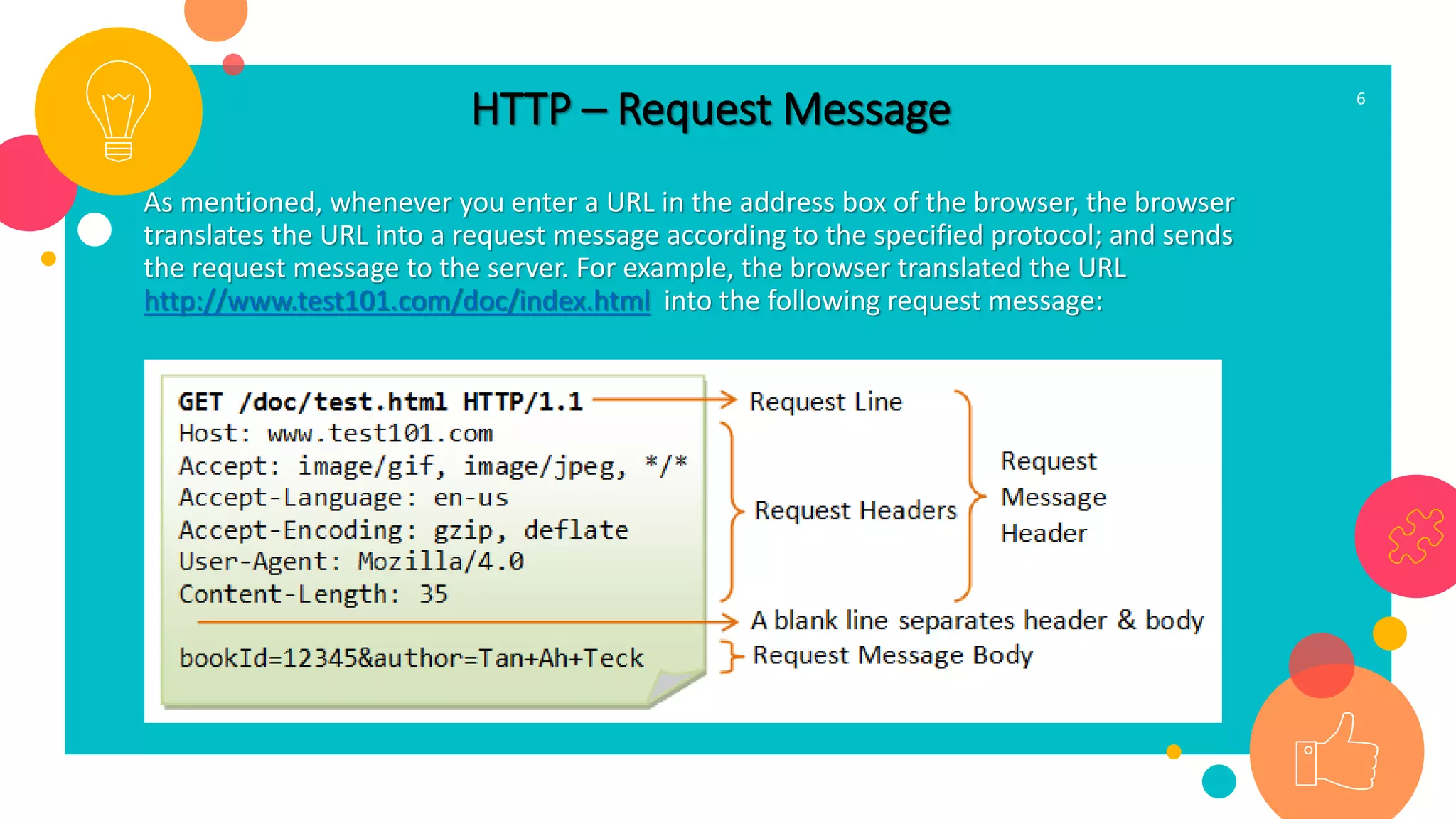
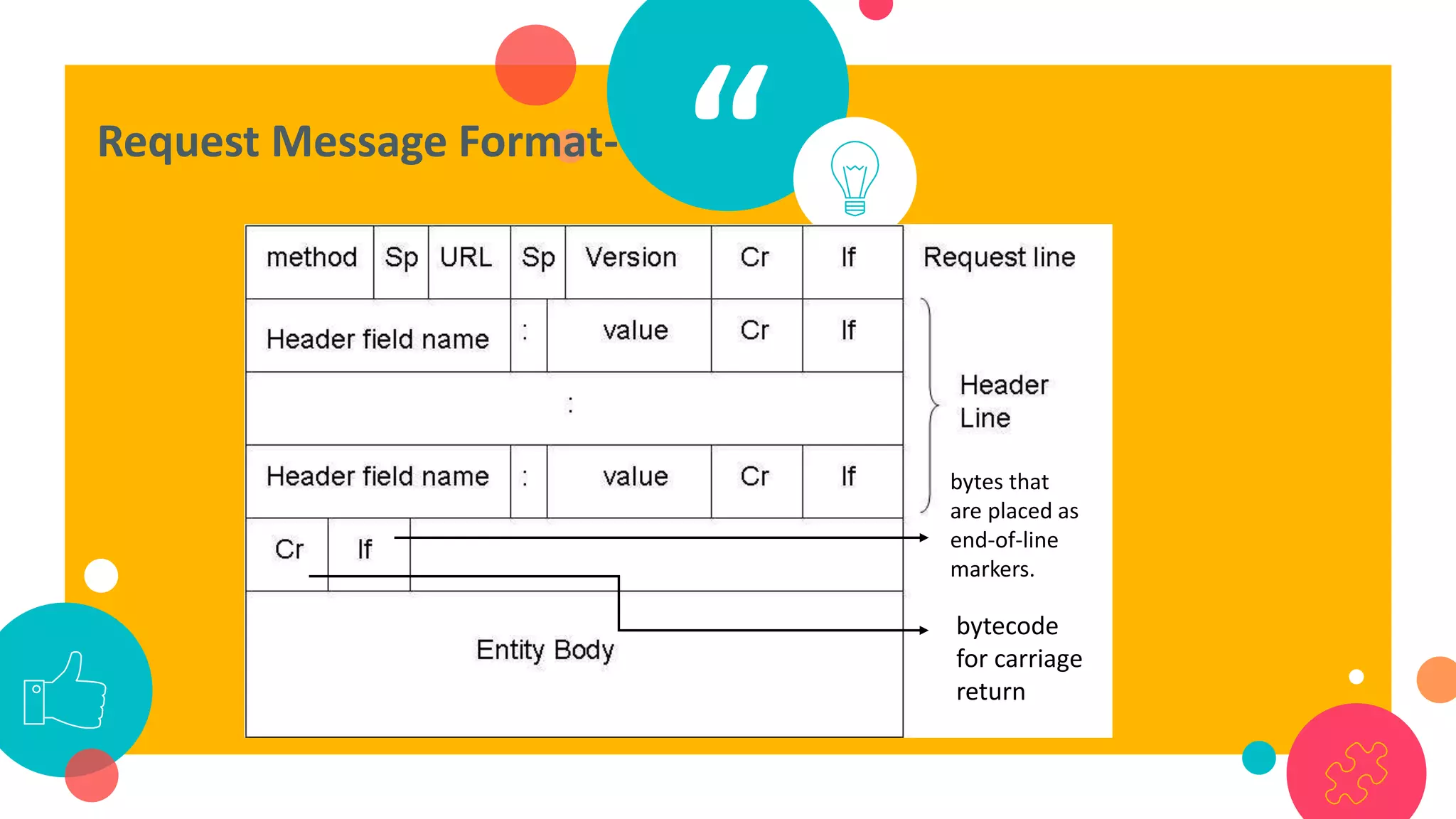
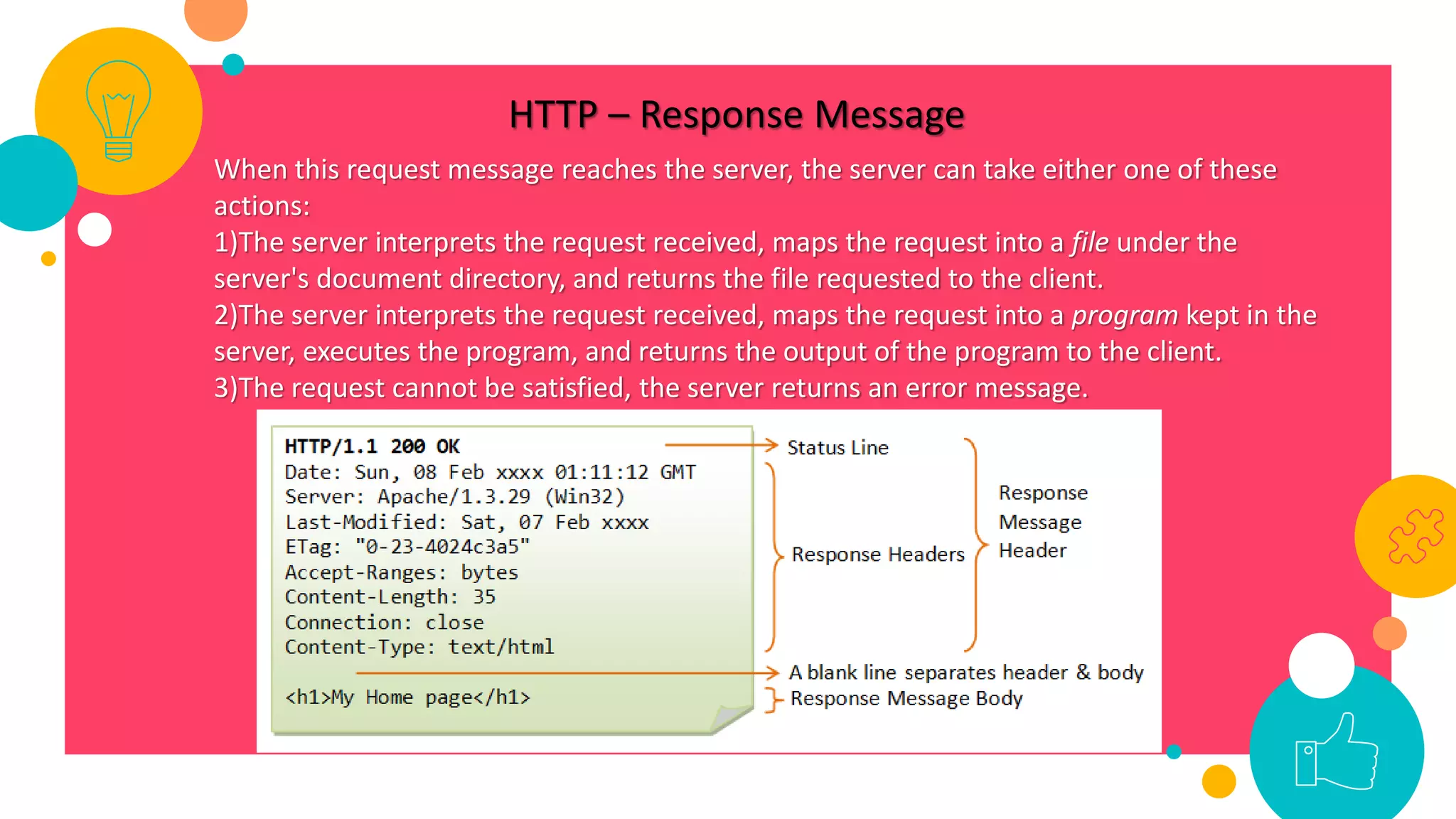
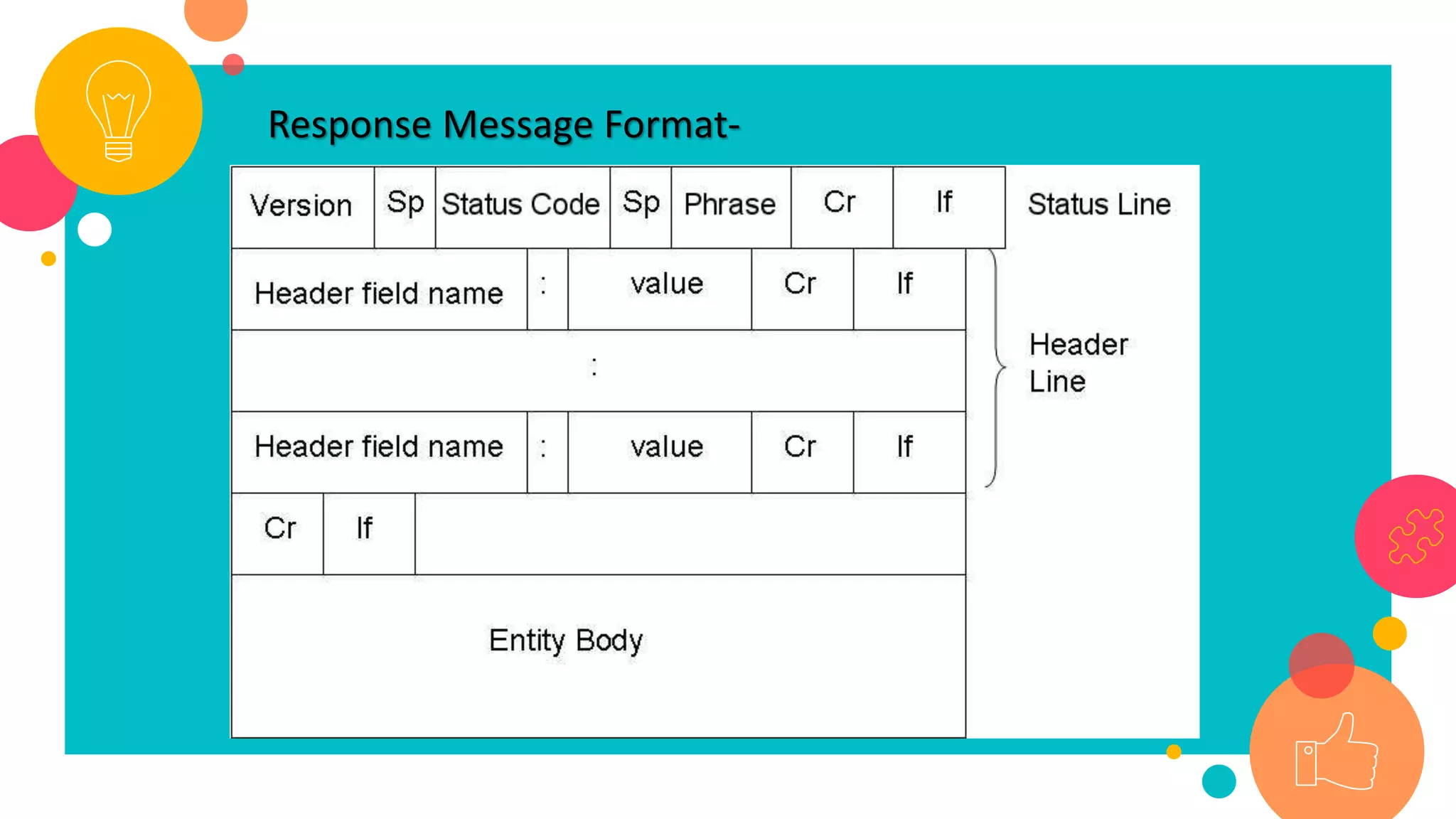
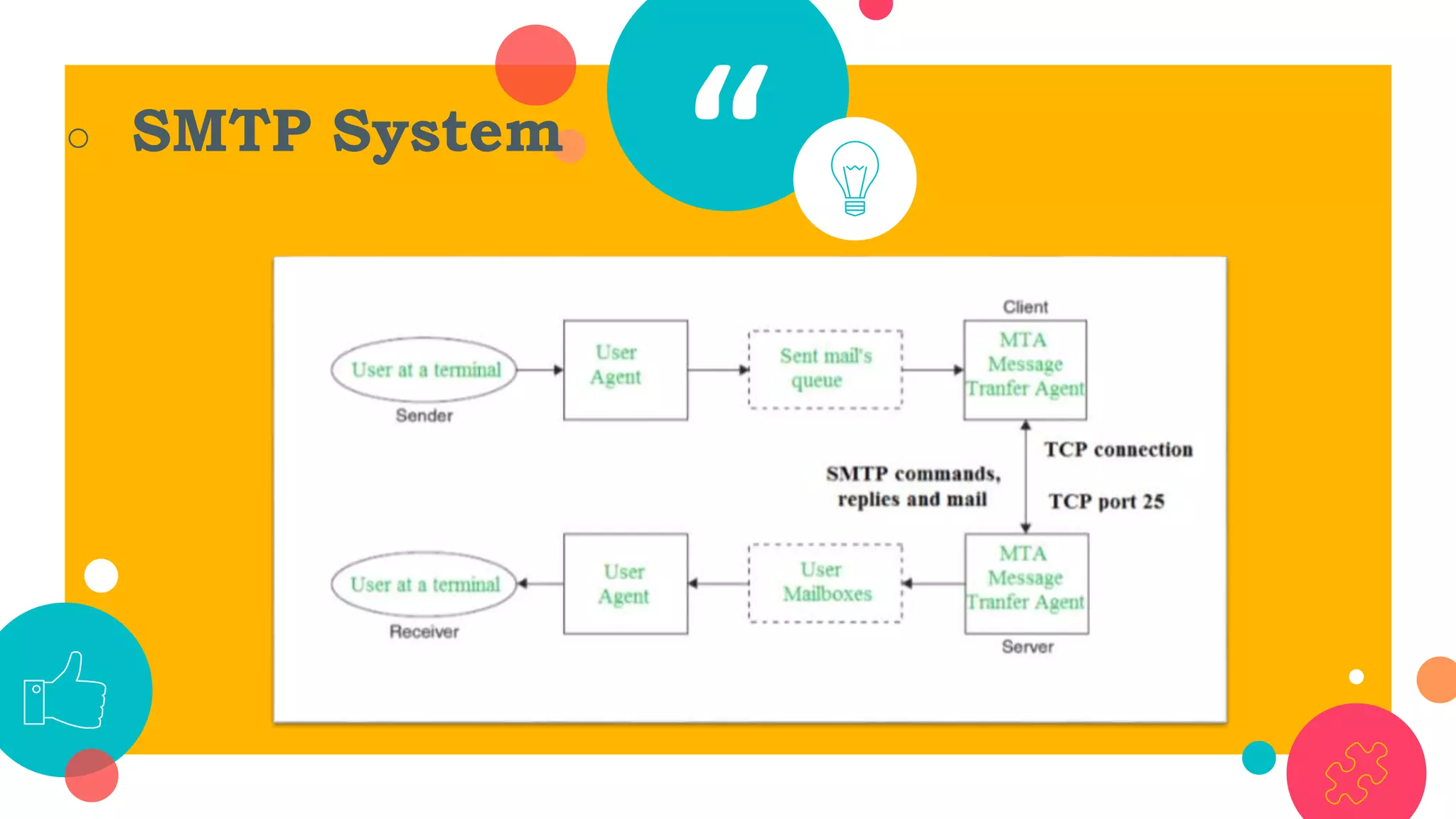
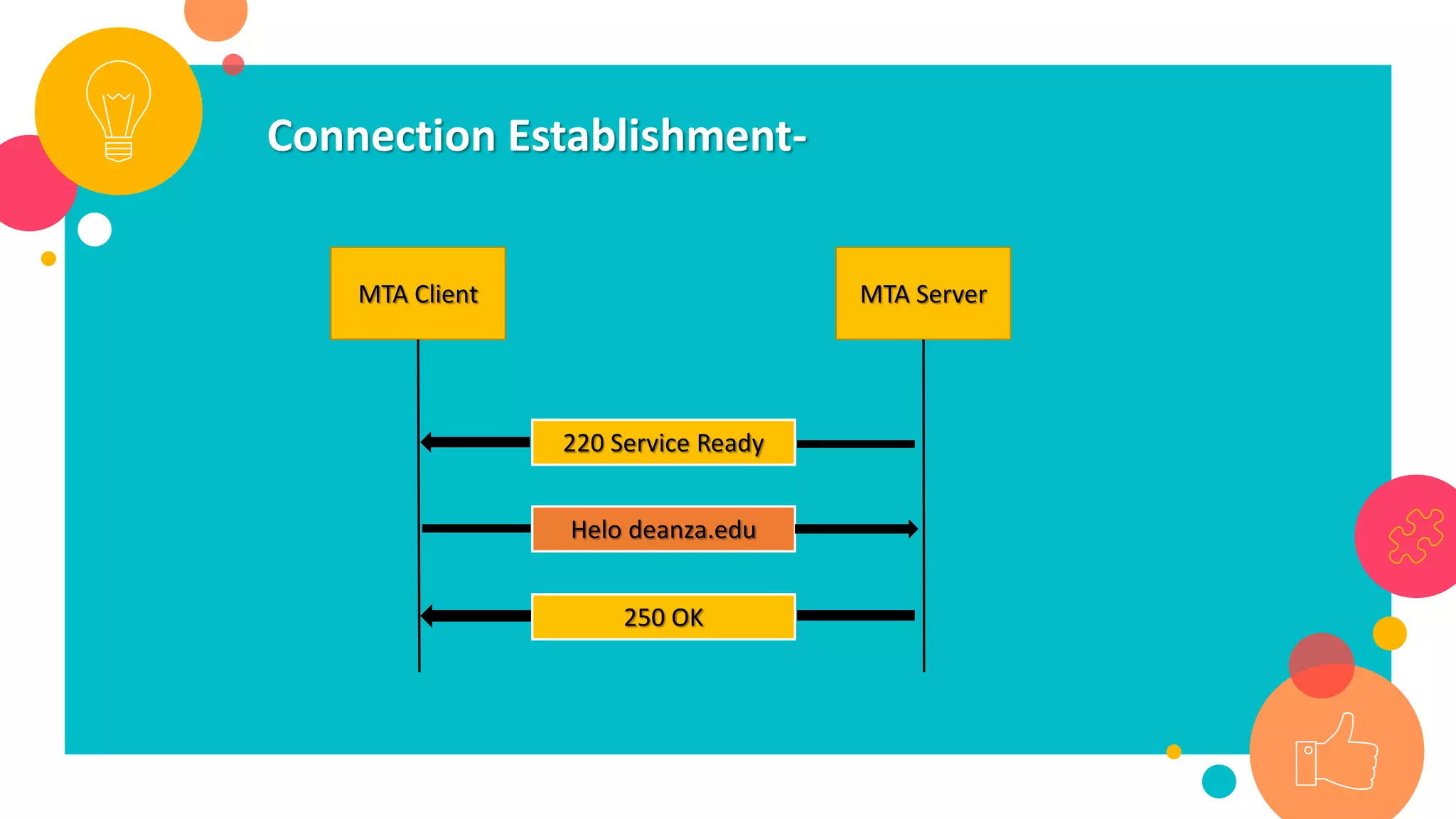
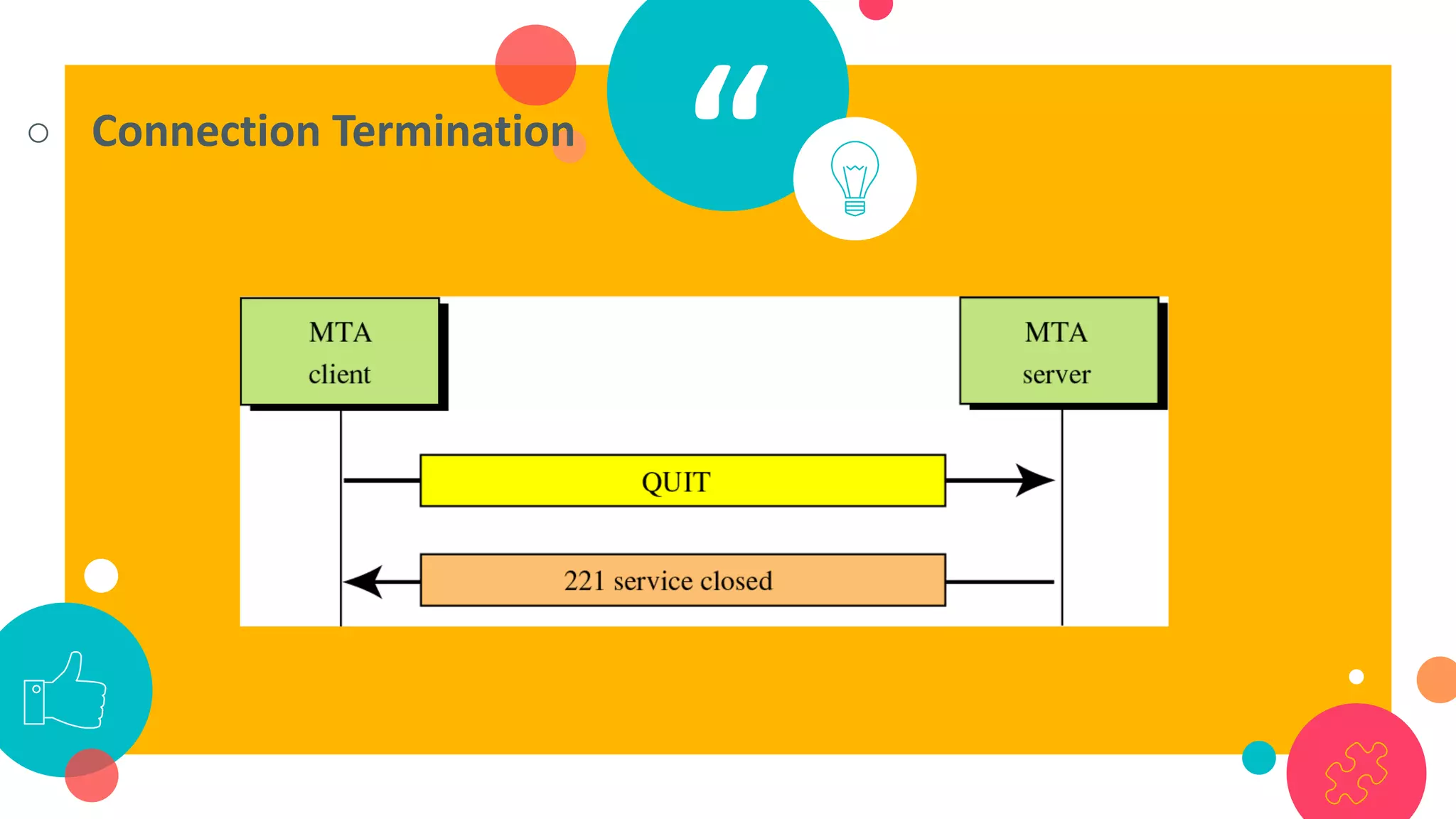
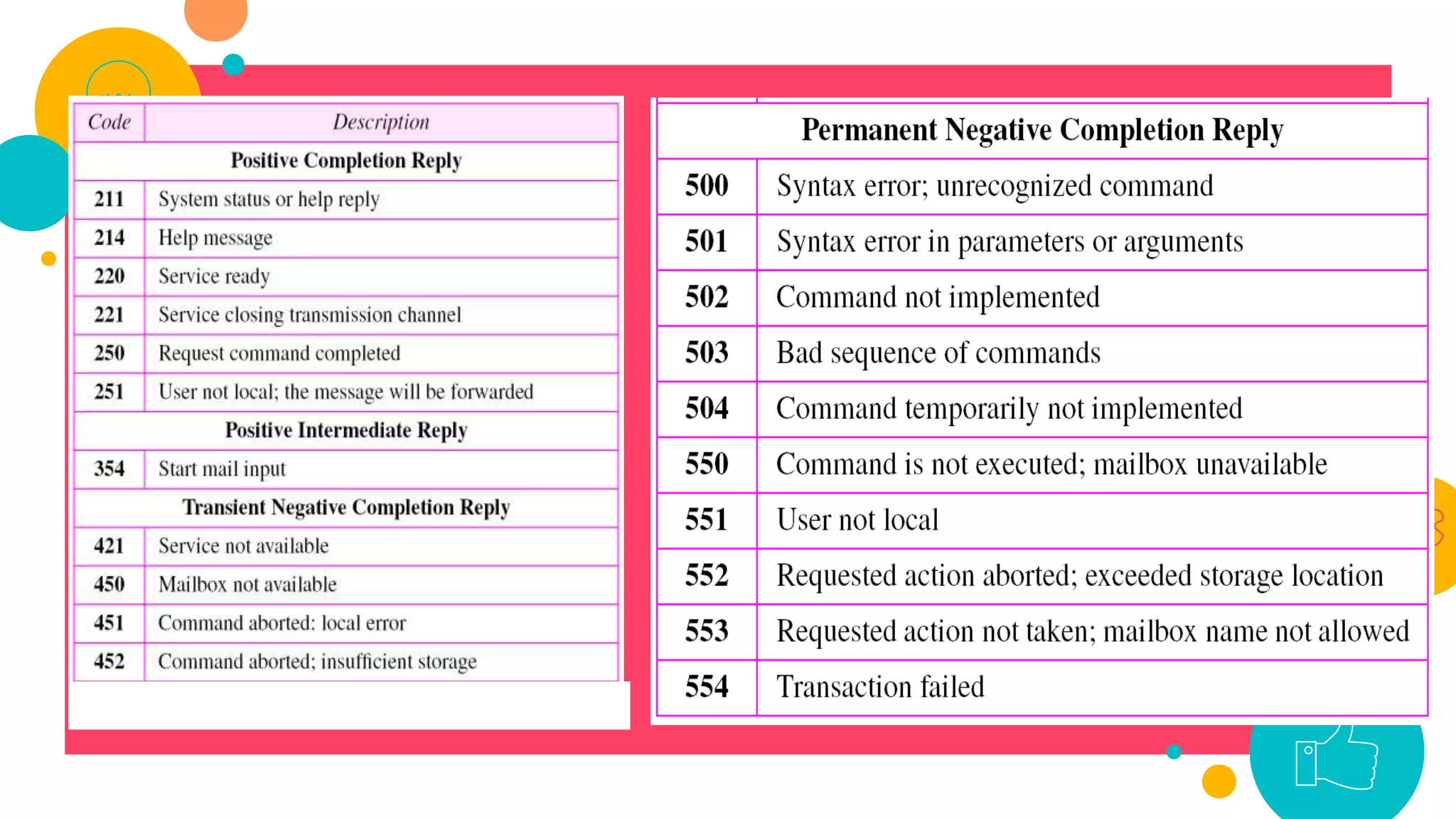
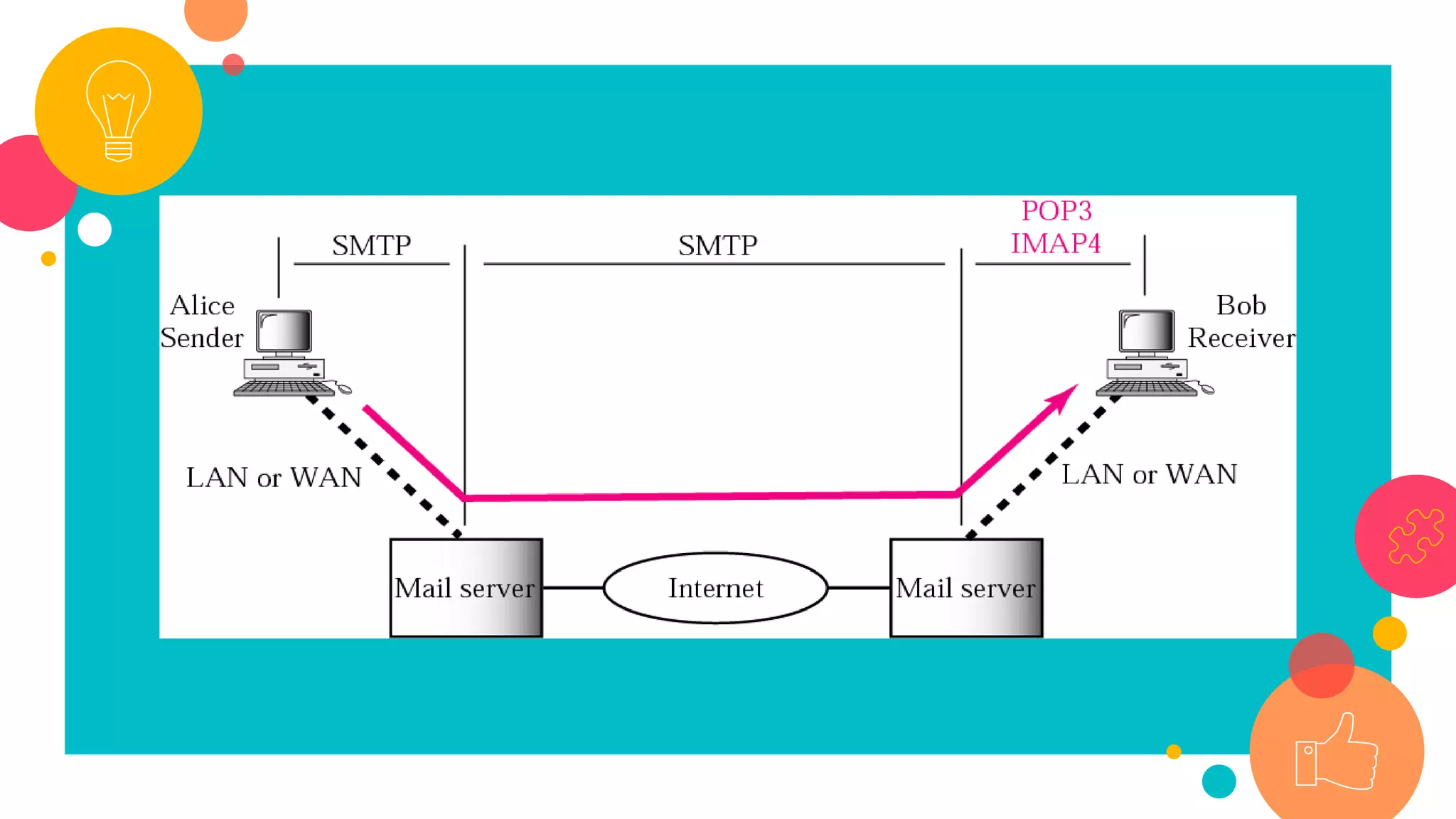
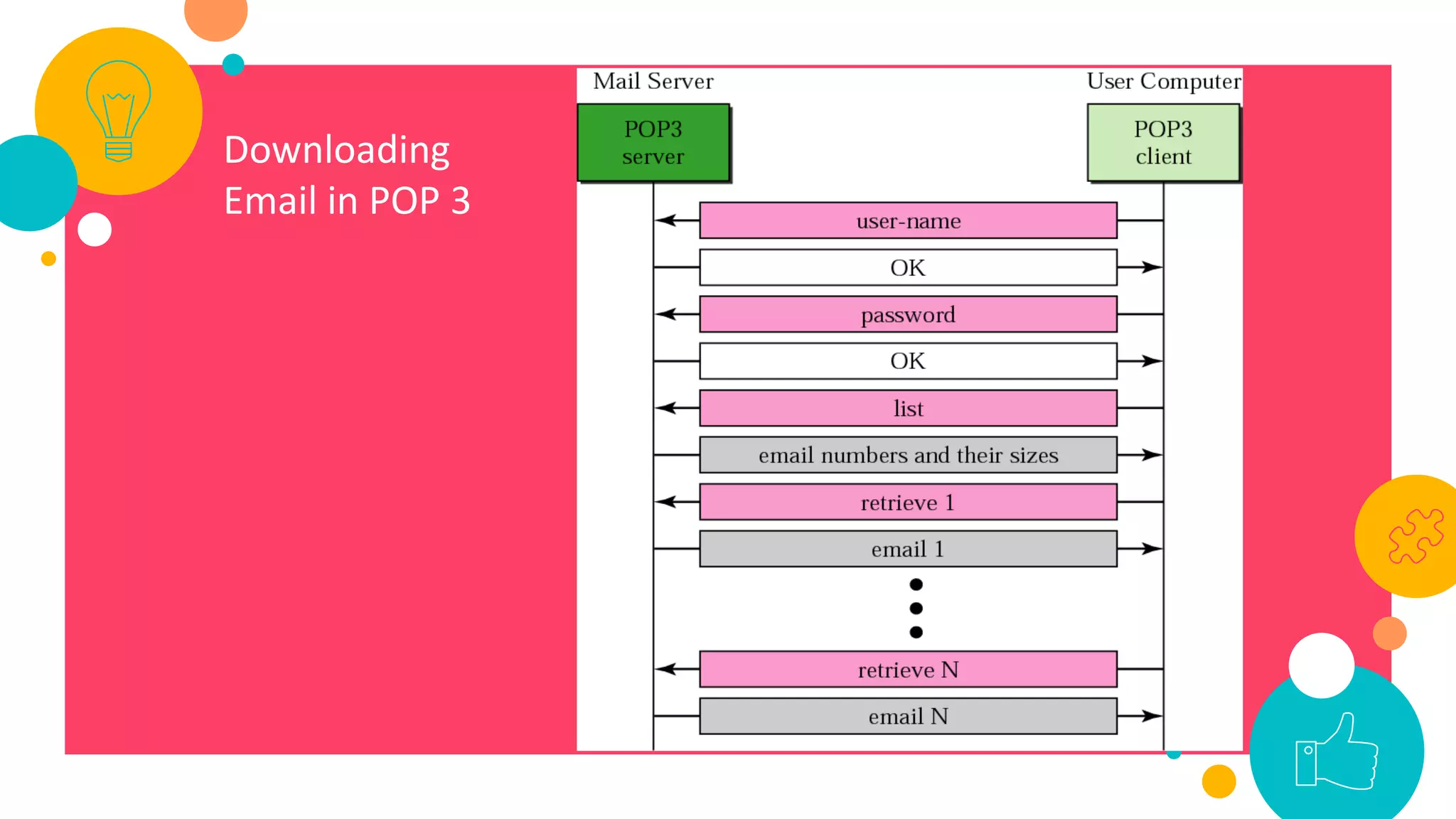
HTTP is an application layer protocol for transmitting hypermedia documents across the internet. It uses a request-response model where clients make requests which are serviced by HTTP servers. Common HTTP request methods include GET, POST, PUT and DELETE. A GET request retrieves a resource from the server, while POST submits data to be processed. The HTTP protocol defines the format of requests and responses, including request headers, response status codes and more. Other application layer protocols discussed include SMTP for email transmission and POP3 for retrieving emails from a server.