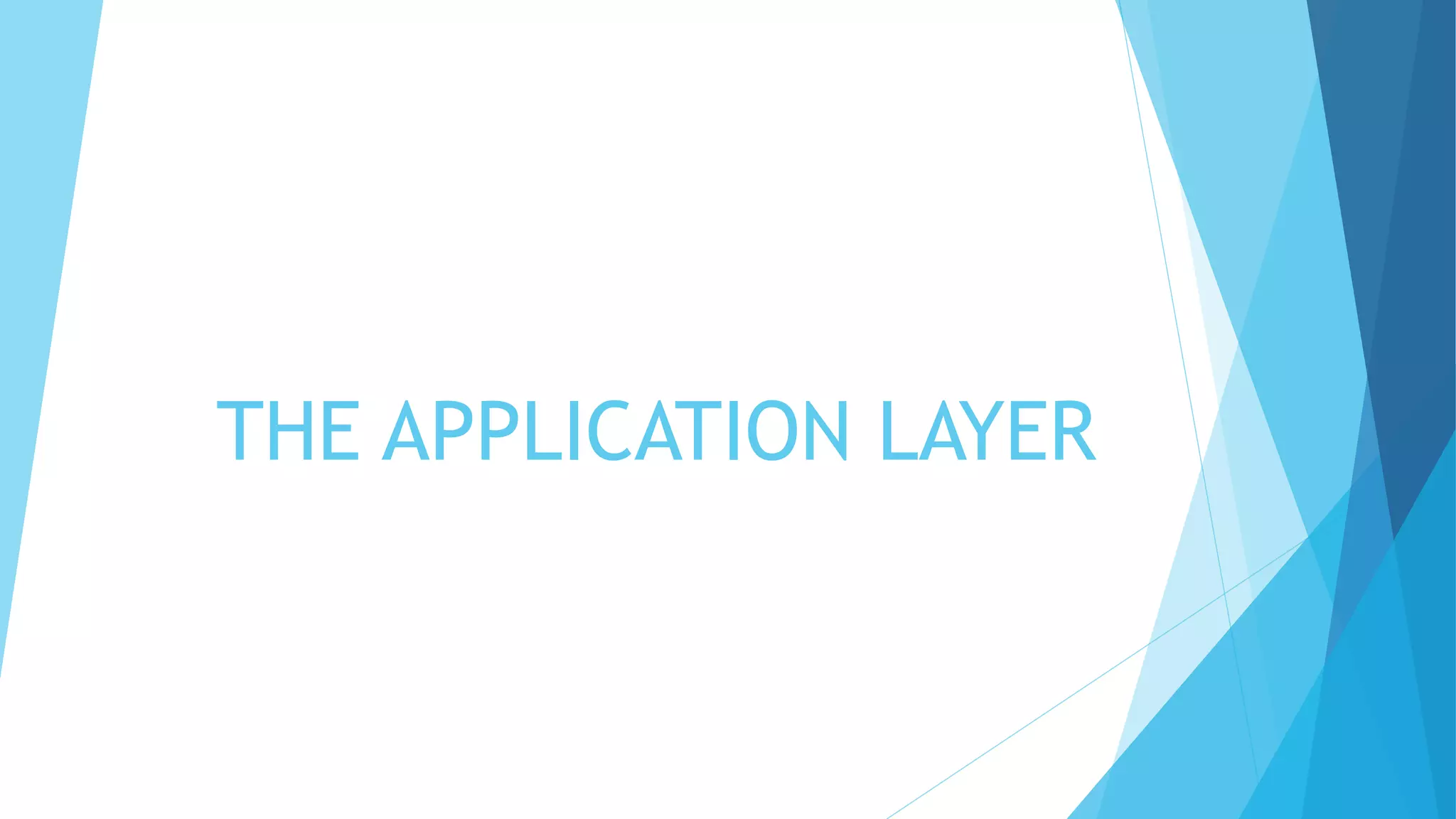
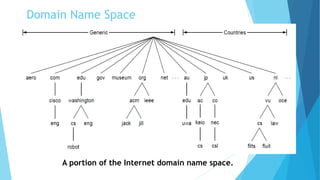
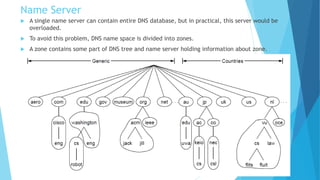
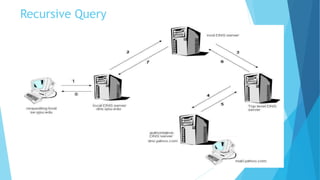
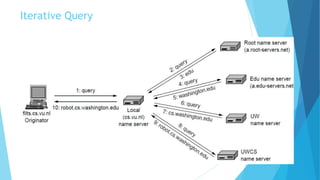
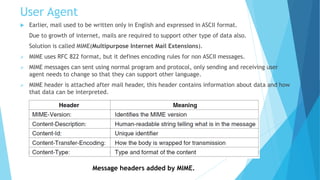
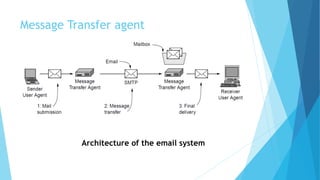
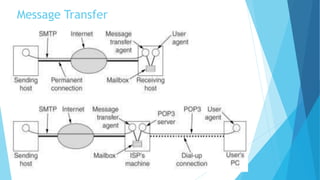
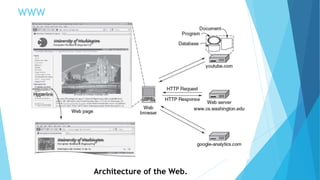
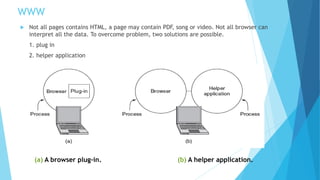
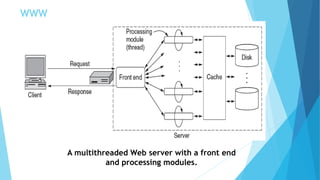
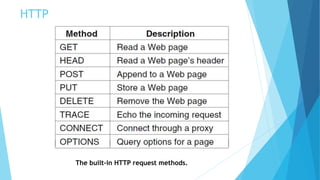
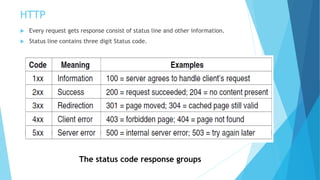
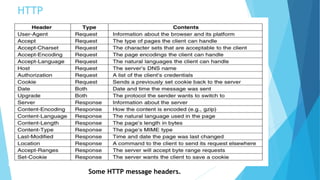
The document discusses the Domain Name System (DNS) and how it works to translate domain names to IP addresses. It explains the hierarchical structure of domain names from top-level domains down to subdomains. It also describes how DNS servers store and retrieve resource records containing IP address mappings for domain names. Finally, it provides examples of common resource record types used in the DNS.