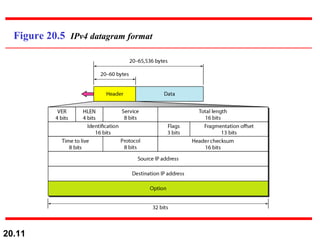
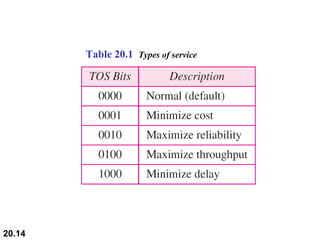
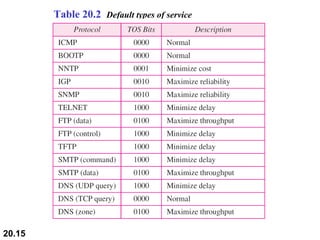
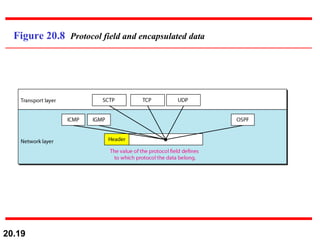
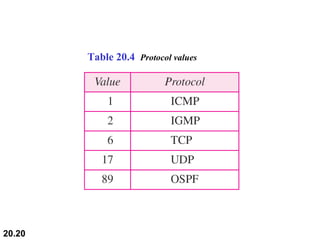
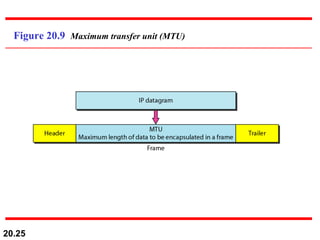
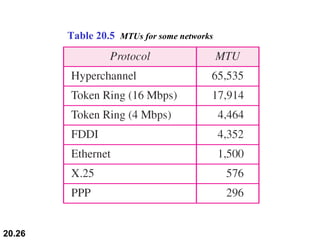
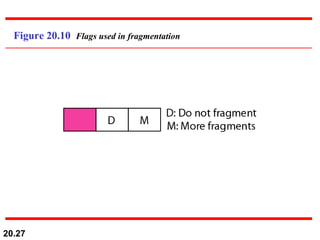
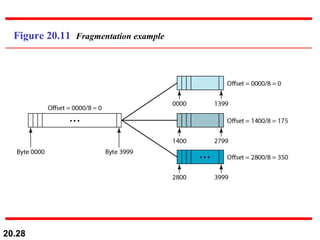
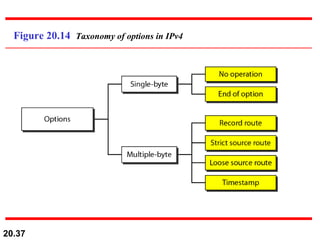
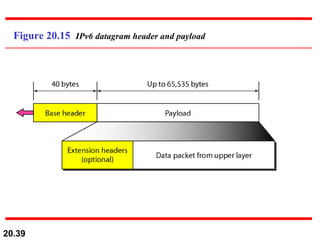
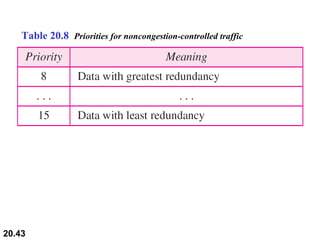
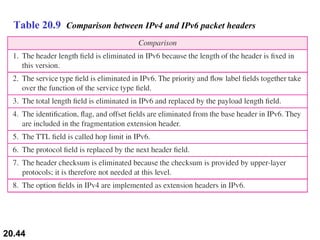
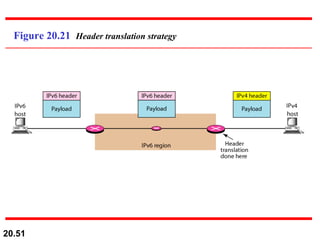
This document provides an overview of Internet Protocol version 4 (IPv4) and version 6 (IPv6). It discusses the need for a network layer in an internetwork, the key components and functioning of IPv4 including packet structure, fragmentation, and checksum calculation. It then covers the advantages of IPv6 over IPv4 and the differences in packet format and extension headers between the two protocols. Finally, it discusses the challenges of transitioning from IPv4 to IPv6 and different transition strategies like running both protocols simultaneously, tunneling, and header translation.