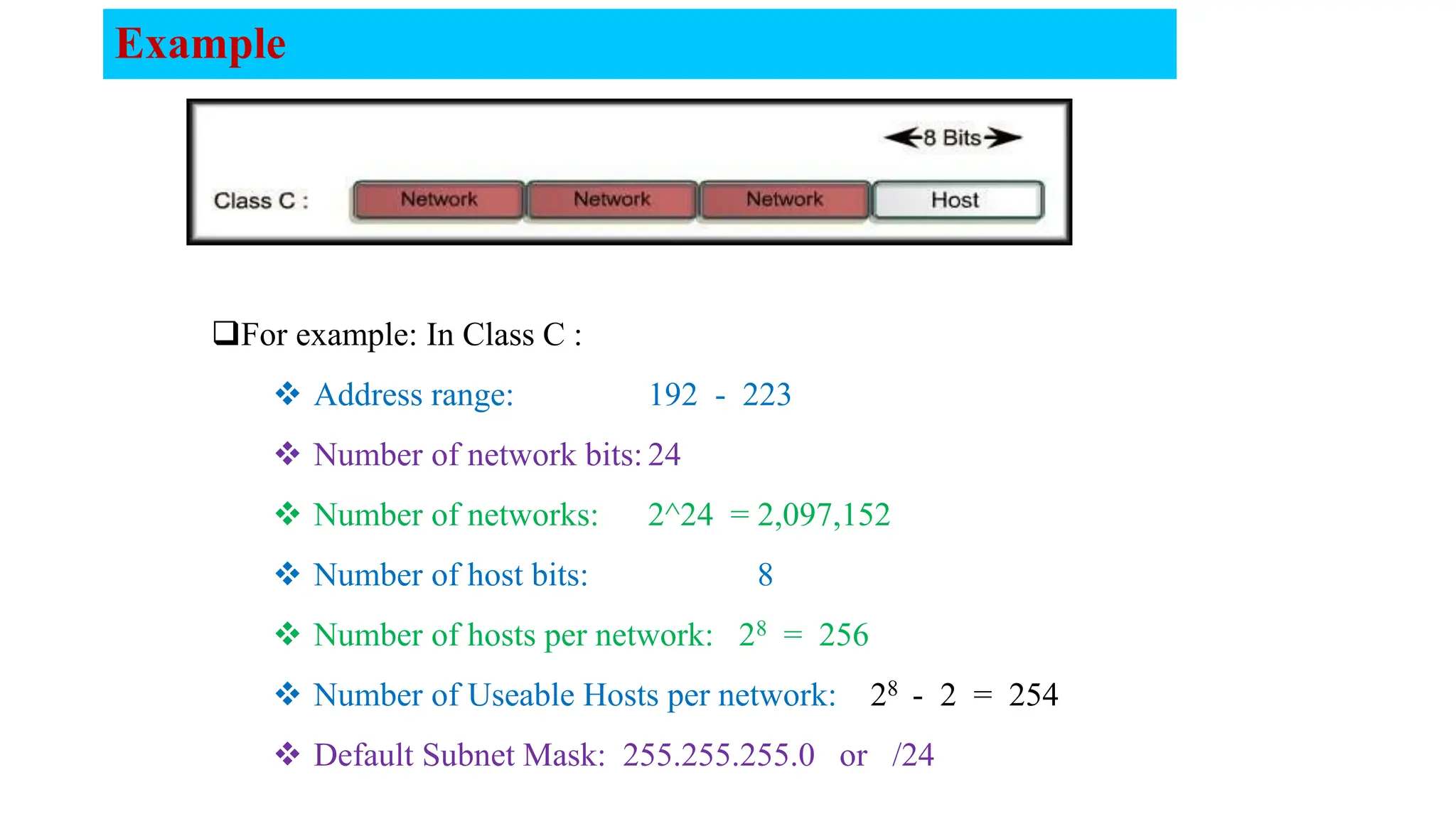
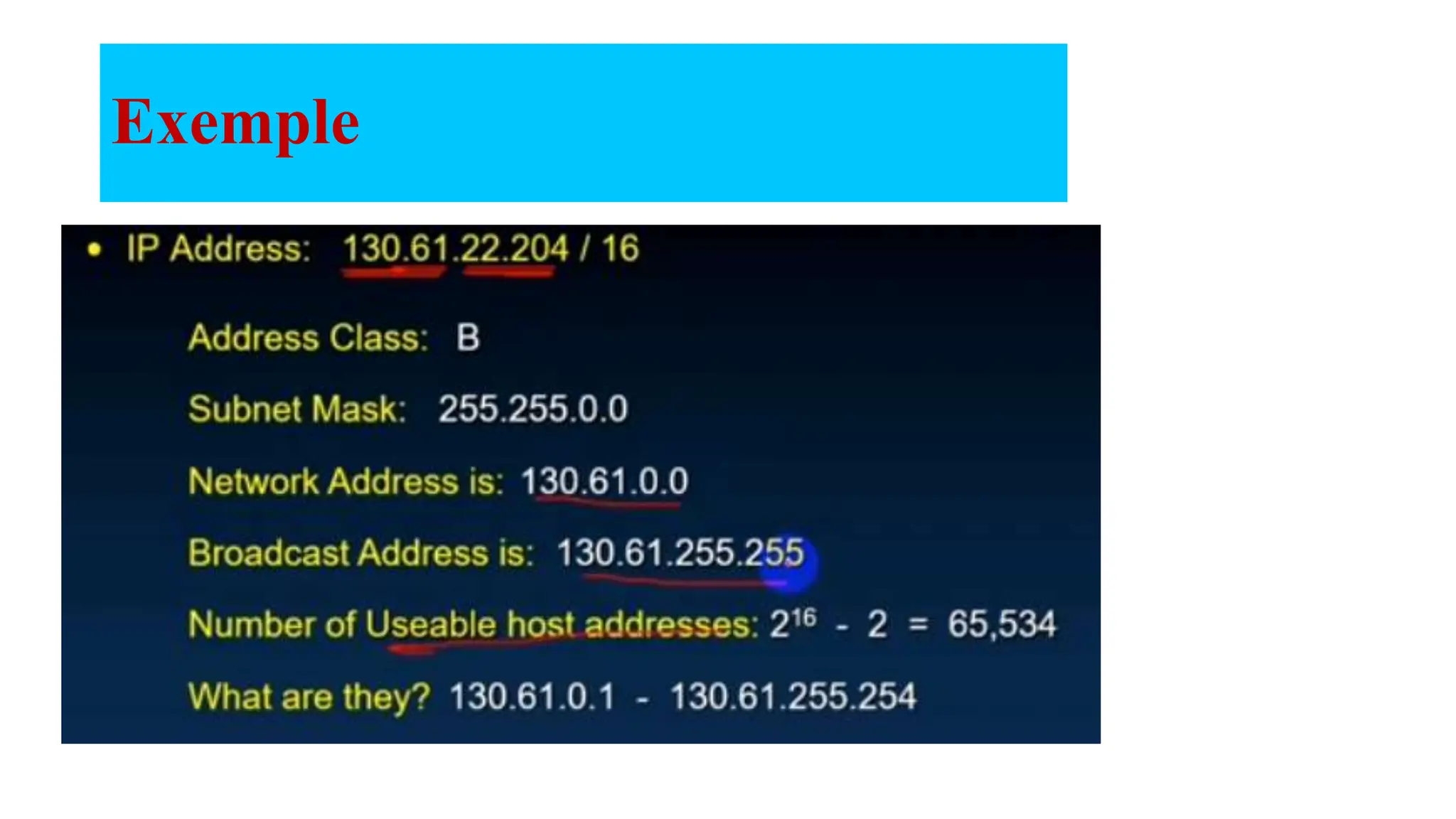
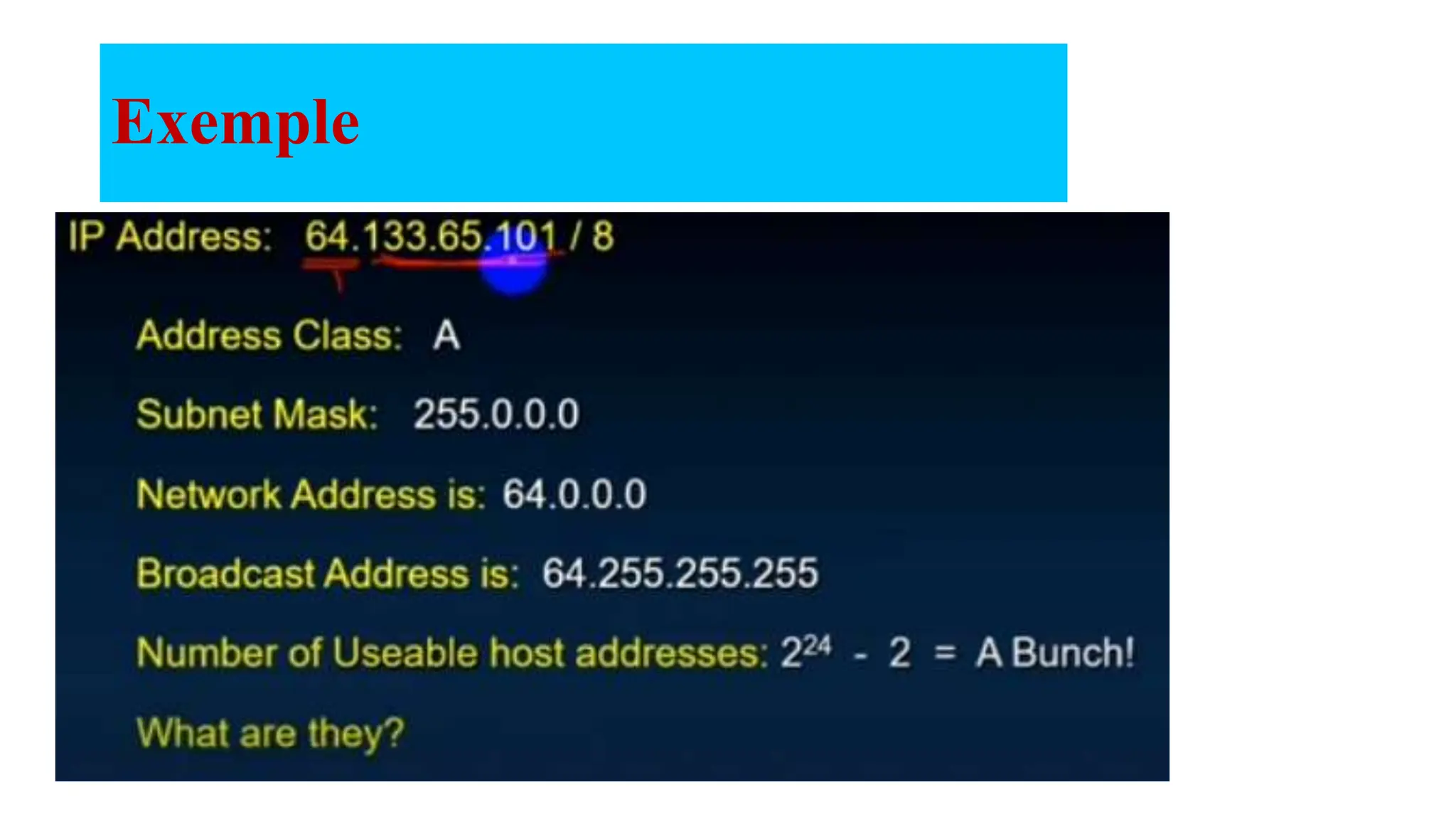
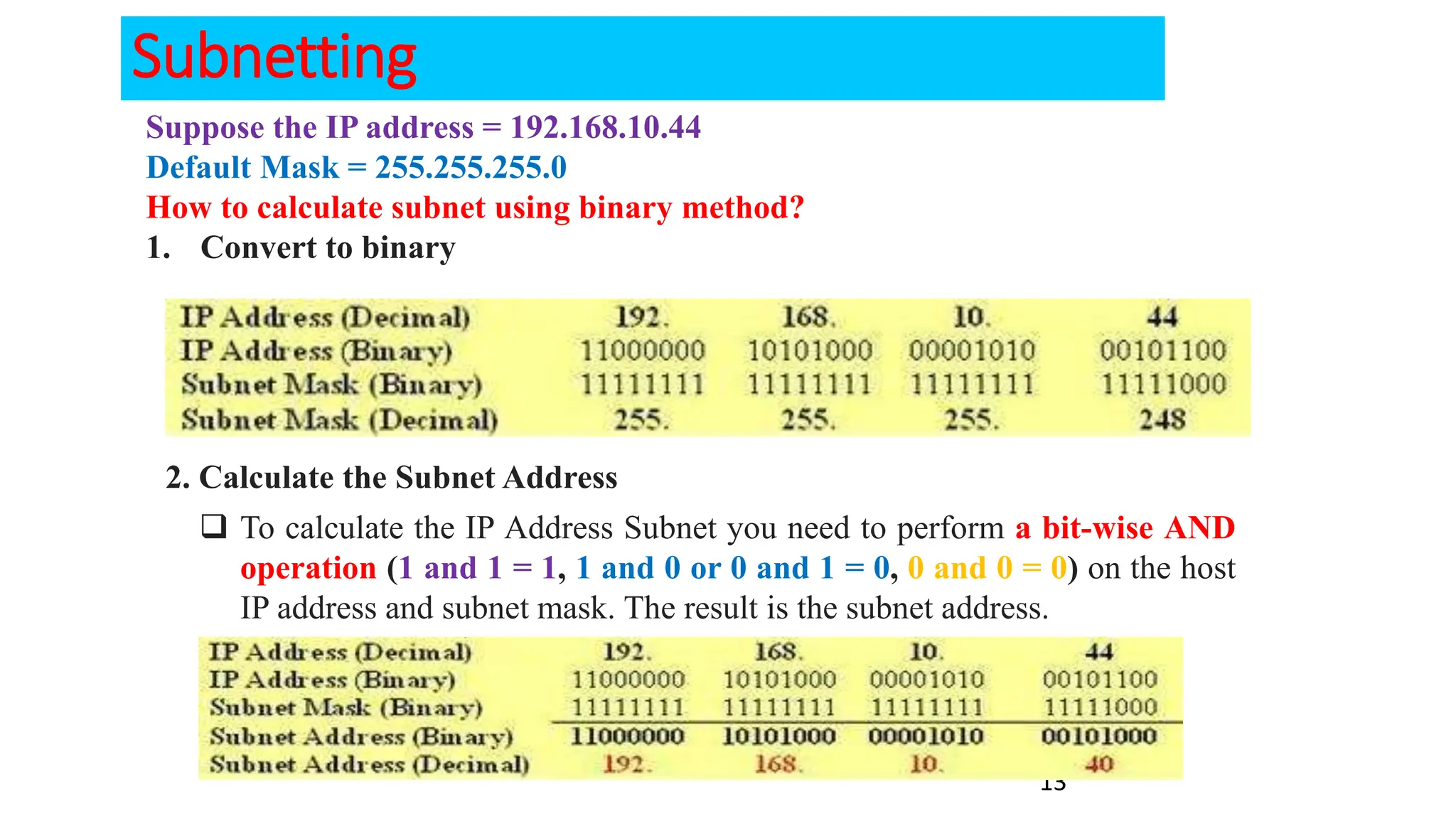
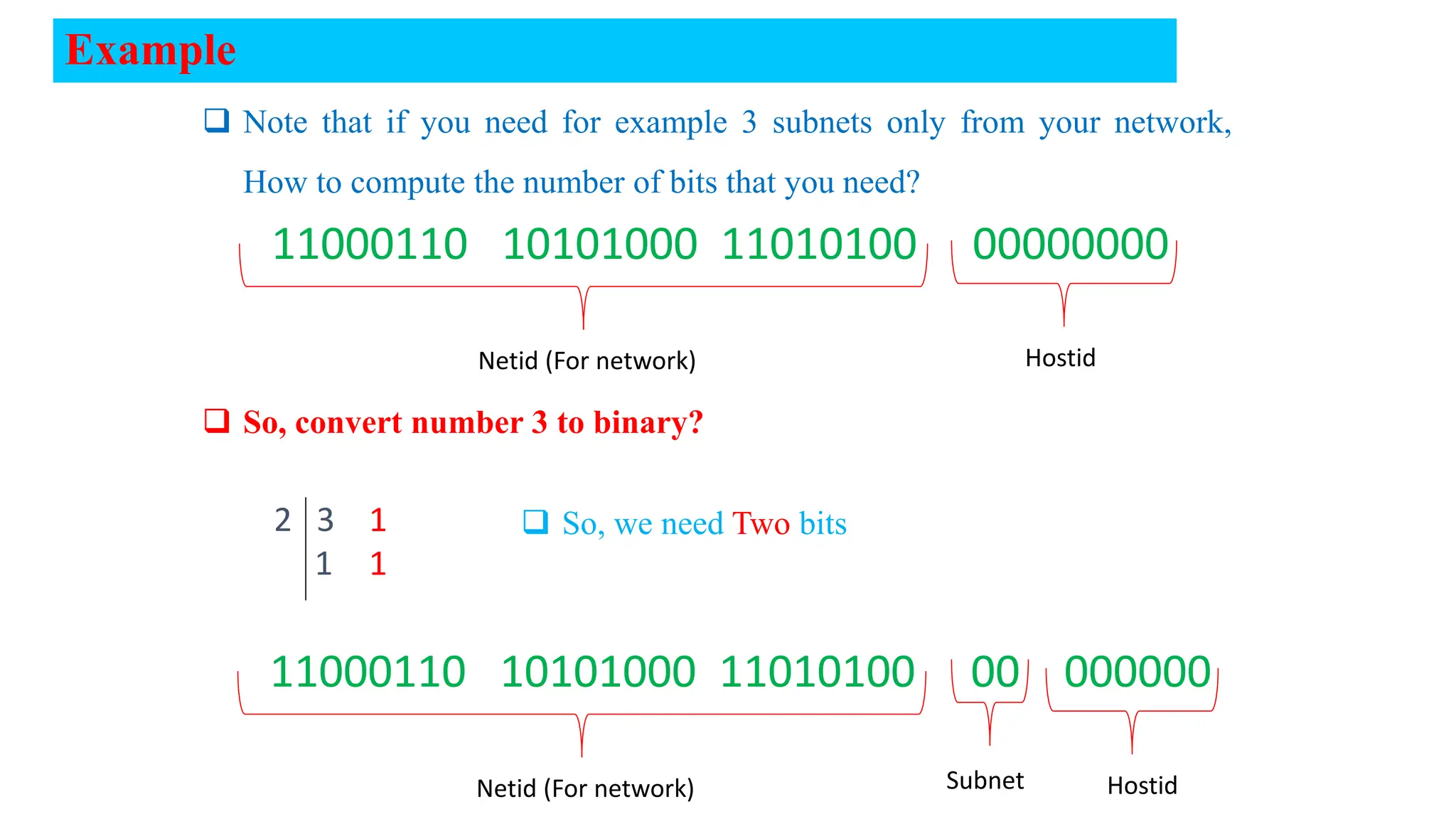
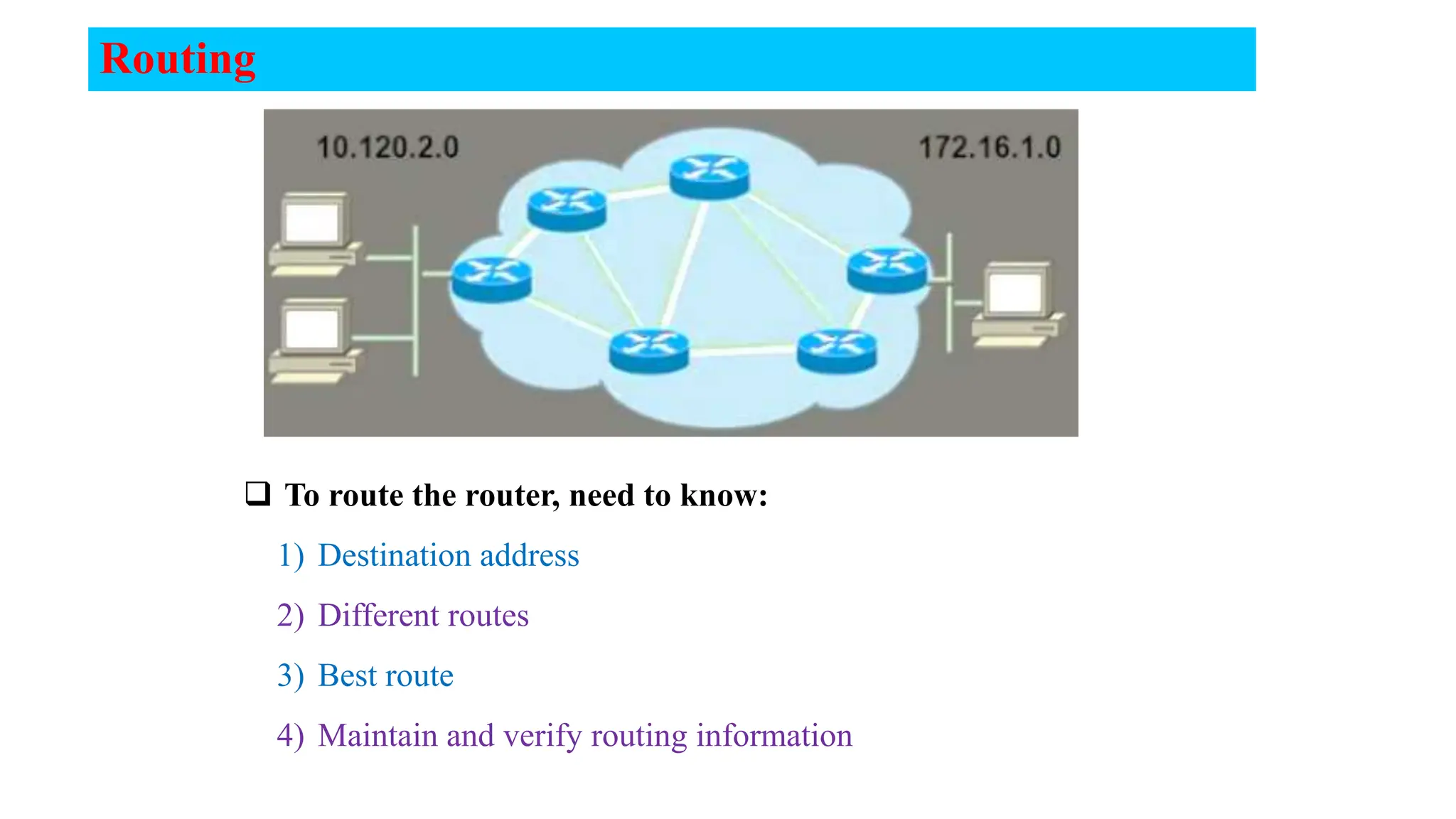
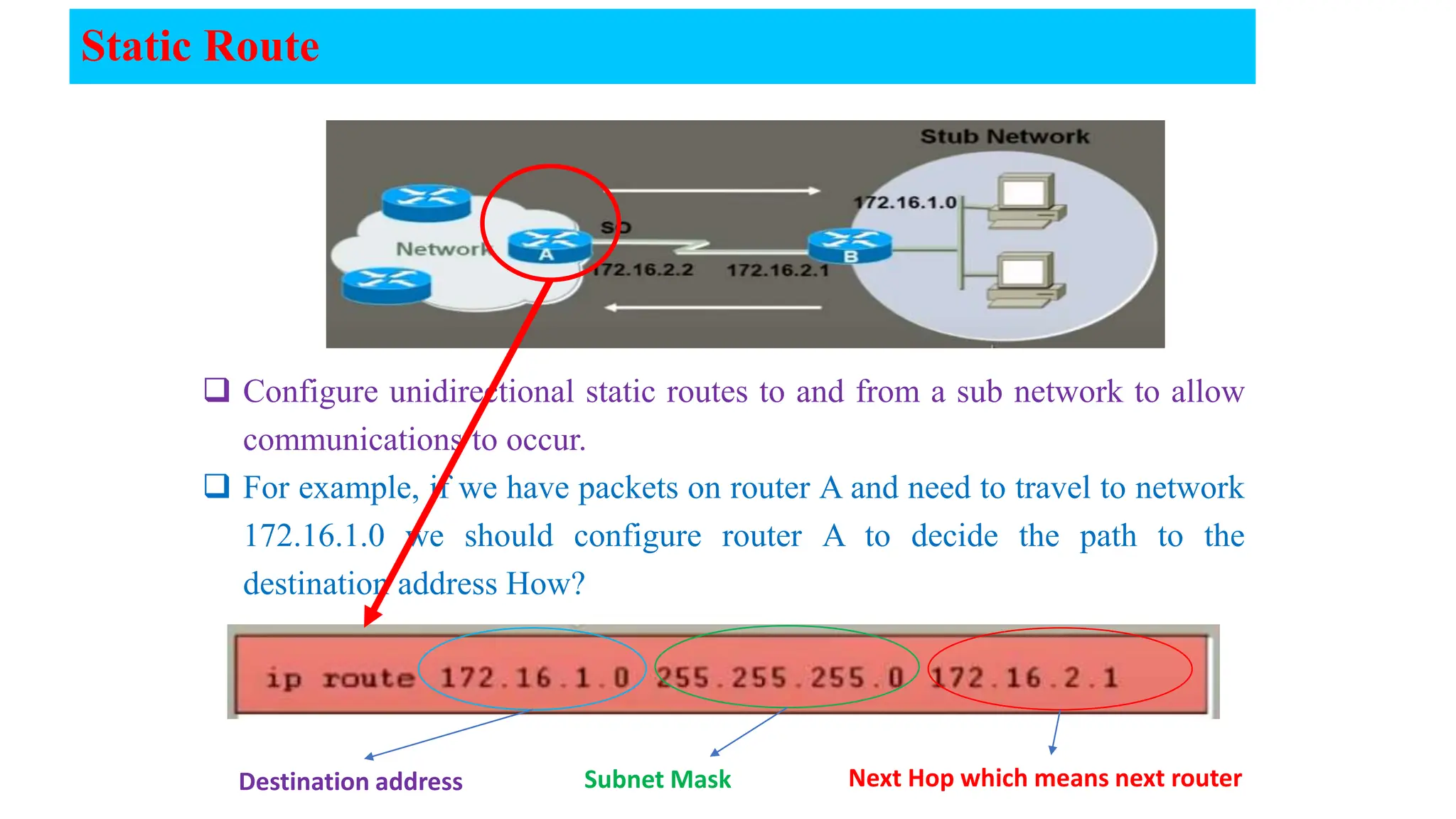
The document covers the fundamentals of computer networks, focusing on the concepts of the network layer, classful IP addressing, subnetting, and routing. It explains network classes (A, B, C), default subnet masks, the process of subnetting, and the calculation of usable host addresses. Additionally, it outlines static and dynamic routing processes, including routing protocols and how to manage routing tables effectively.