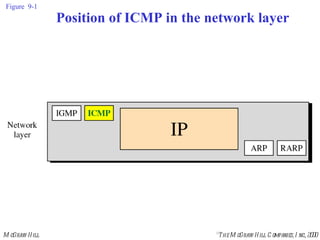
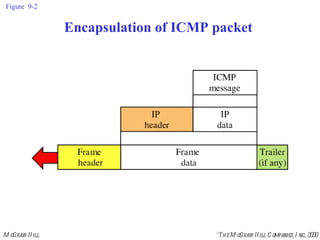
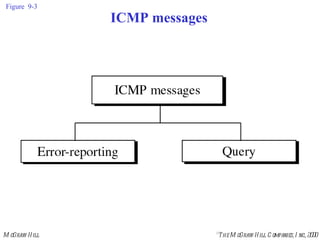
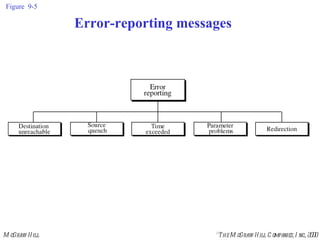
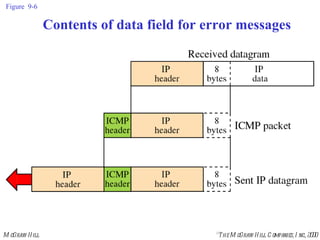
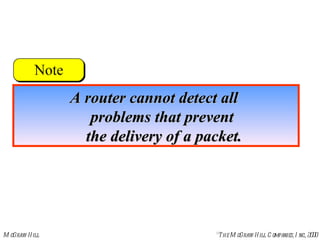
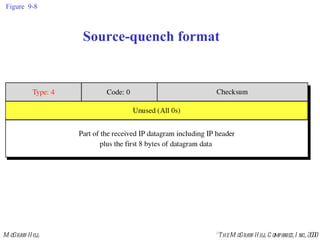
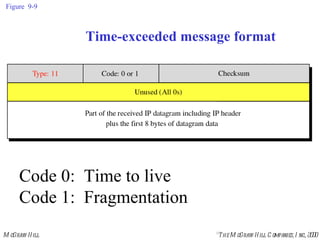
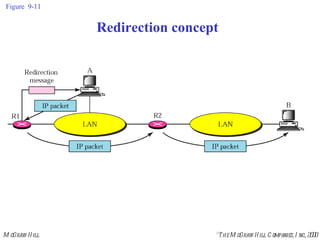
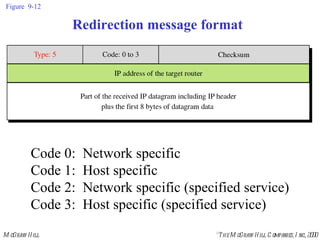
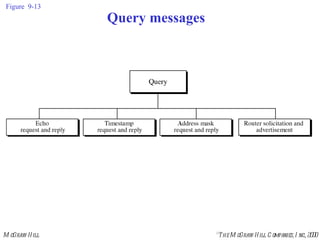
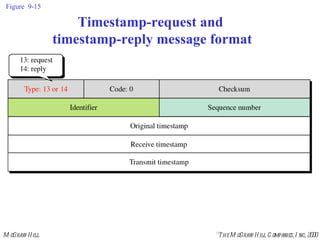
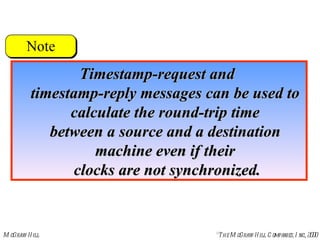
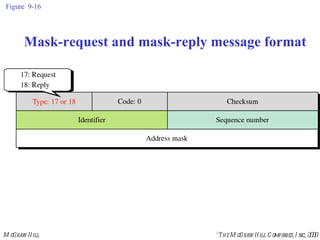
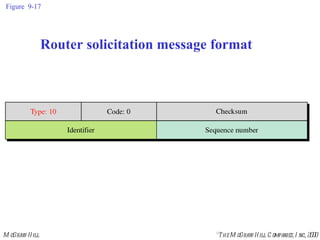
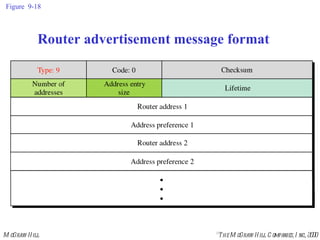
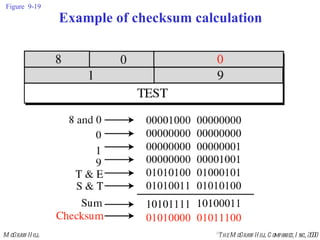
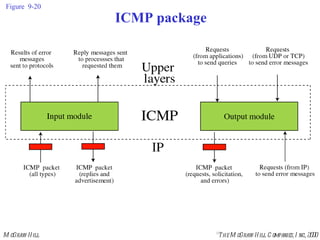
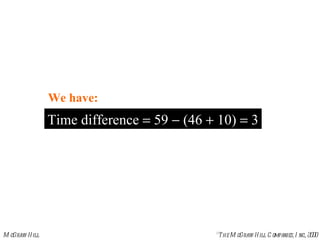The document summarizes Internet Control Message Protocol (ICMP) which is used to report errors and provide diagnostic functions for IP. It describes various ICMP message types including error messages like destination unreachable and time exceeded to report packet delivery problems. It also covers query messages like echo request/reply for reachability testing, and timestamp and mask messages for functions like clock synchronization between hosts. Checksums are used to validate ICMP packets.