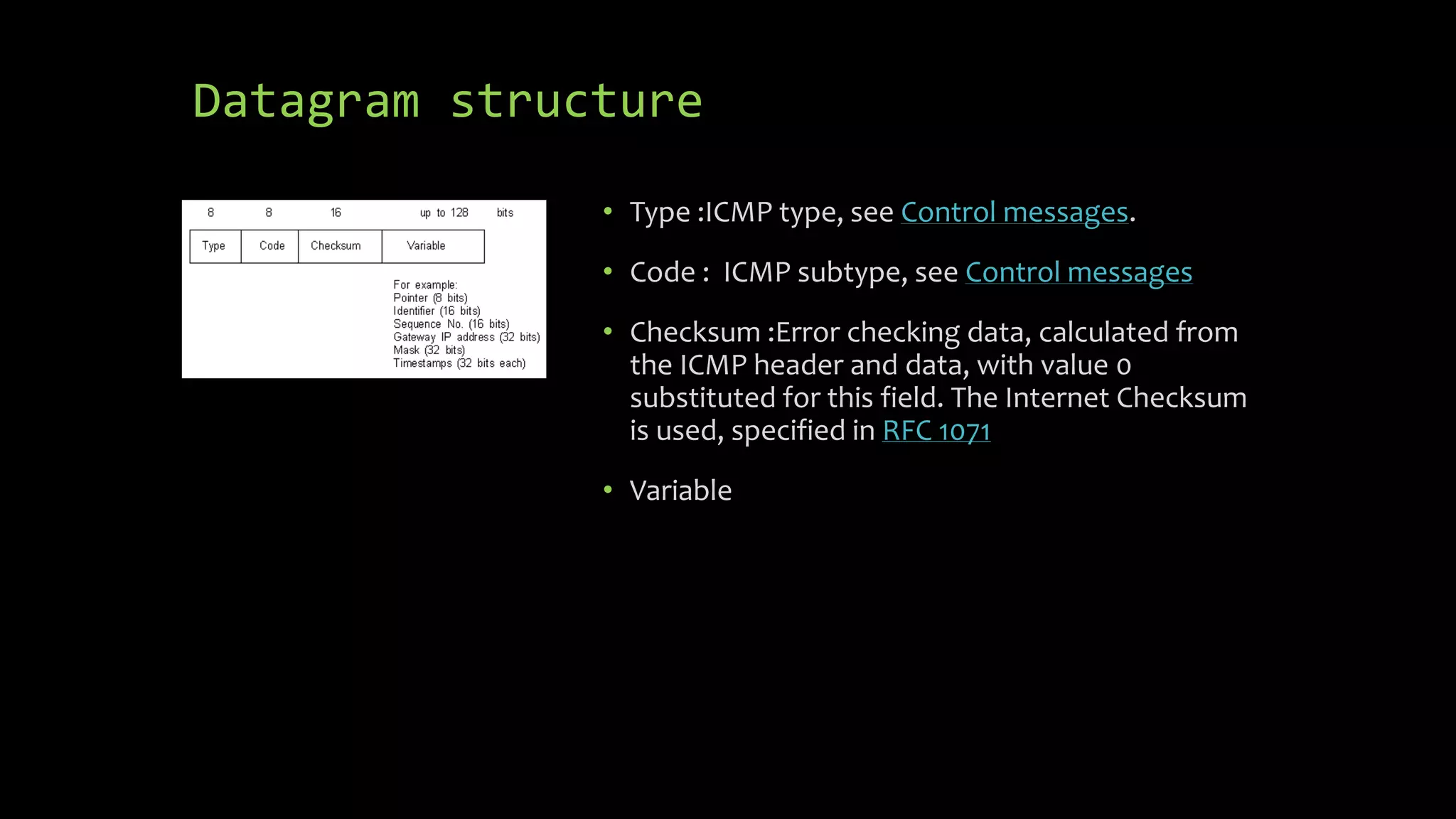
The document discusses the ICMP protocol and some of its applications. It provides the following key details:
- ICMP is a supporting protocol used by network devices to send error messages and operational information. Unlike TCP and UDP, it is not used to exchange data between systems.
- Common applications of ICMP include Ping, which is used to verify connectivity to an IP address, and Traceroute, which identifies each device on the network path and the response time between hops.
- Traceroute works by sending ICMP Echo Requests and measuring the response time at each network hop to map the full route between two points. This can help troubleshoot connectivity issues.