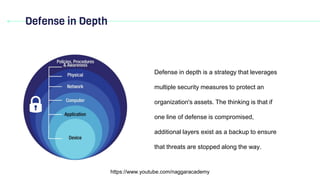
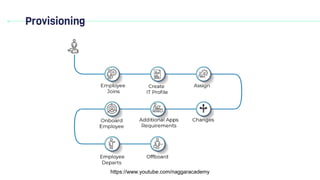
The document discusses key concepts in domain 3 - access control. It covers physical and logical access controls, security controls, subjects and objects, defense in depth, least privilege, need to know, privileged access management, segregation of duties, and provisioning. The concepts focus on controlling access to resources through countermeasures, granting only necessary access levels, leveraging multiple layers of security, and separating duties to prevent fraud and security compromises.