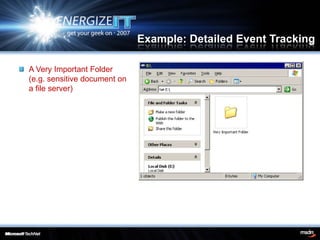
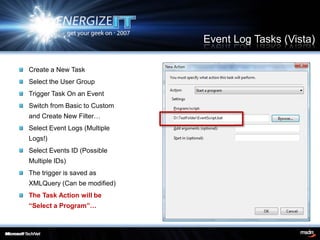
The document discusses the importance of event logging for maintaining a secure environment, highlighting its relevance for regulatory compliance and incident response. It covers aspects such as real-time monitoring, auditing, analysis, and archiving of event logs to mitigate security incidents. Furthermore, it details specific event categories and configurations to effectively track user activities and potential breaches.