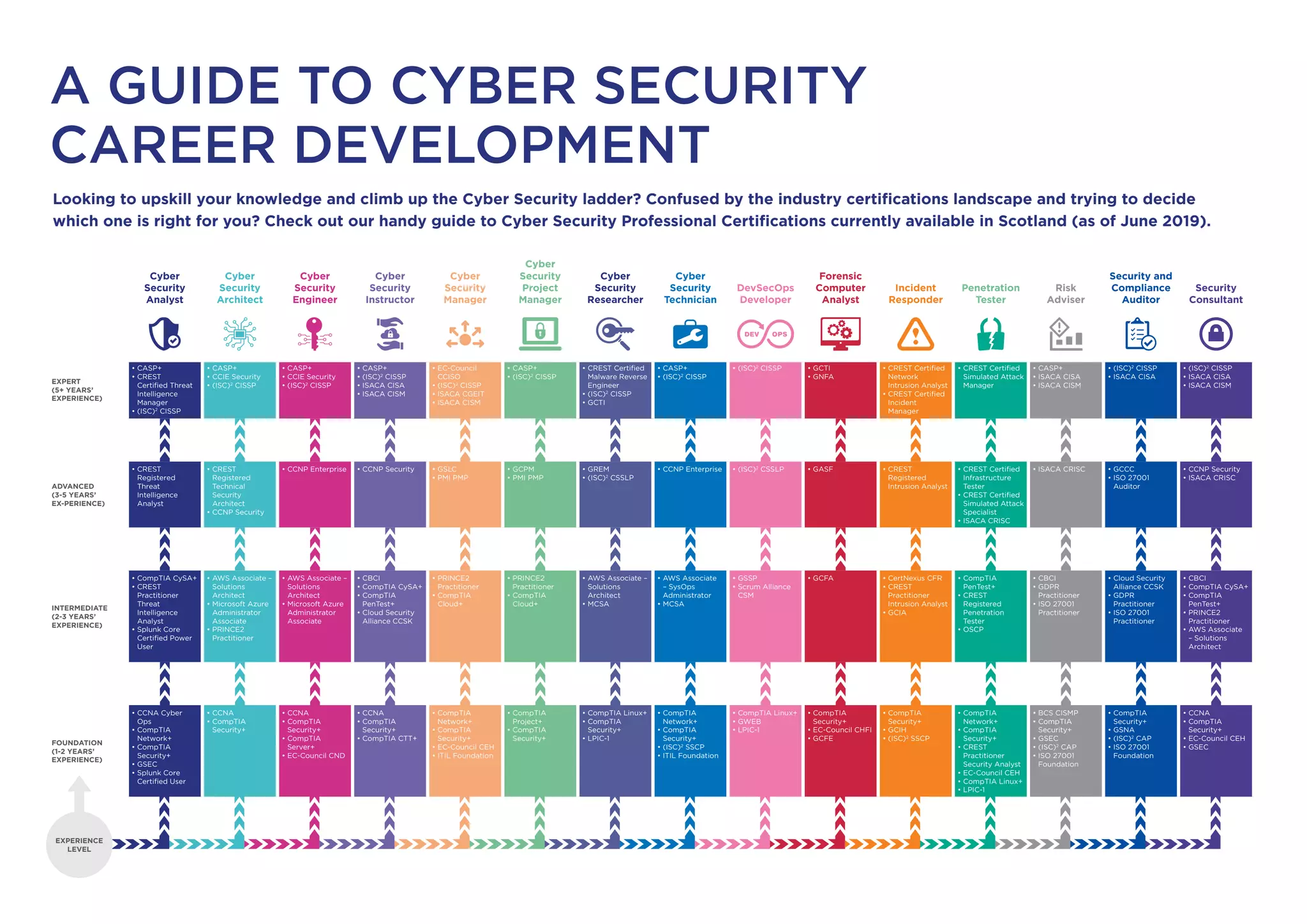
The document provides a comprehensive guide to cyber security professional certifications available in Scotland as of June 2019. It categorizes certifications by experience level—foundation, intermediate, advanced, and expert—covering various roles such as cyber security analyst, architect, manager, and developer. The guide includes specific certifications from various organizations, helping individuals make informed decisions to enhance their career in the cyber security field.