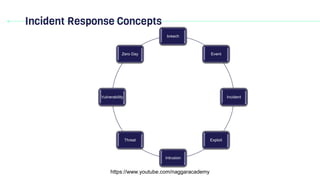
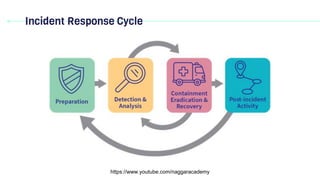
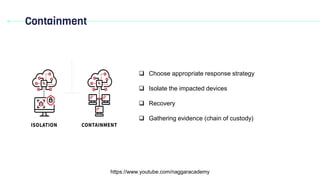
Domain 2 discusses incident response, business continuity, and disaster recovery. It defines key terms related to incident response such as breach, event, incident, exploit, intrusion, threat, vulnerability, and zero day. It explains the importance of having an incident response plan and outlines the typical incident response cycle, which includes preparation, detection and analysis, containment, and post-incident activities like generating lessons learned.