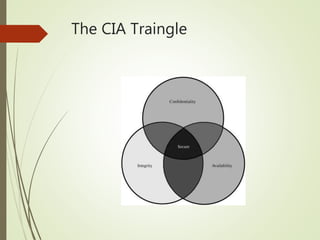
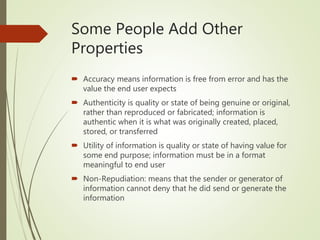
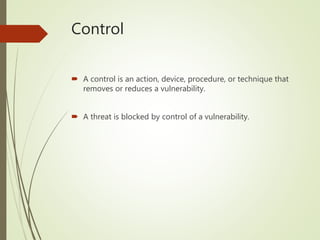
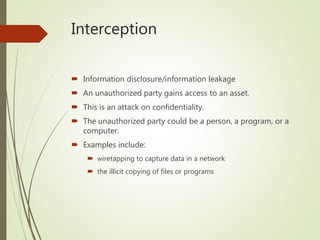
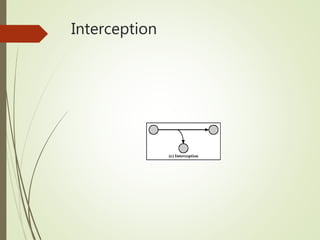
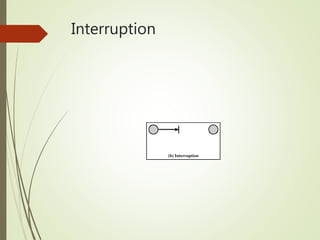
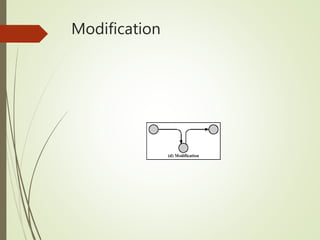
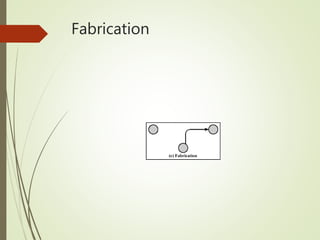
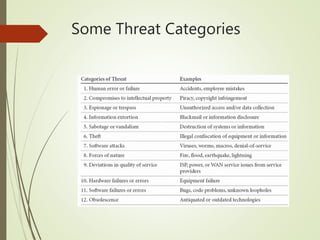
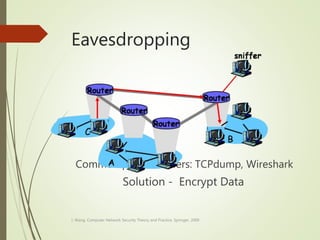
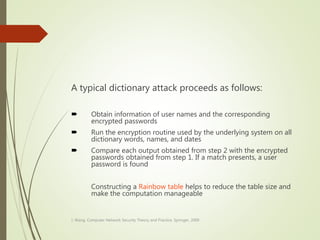
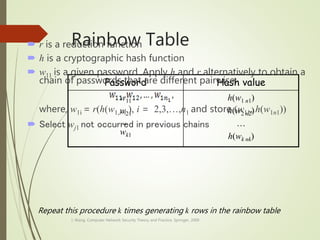
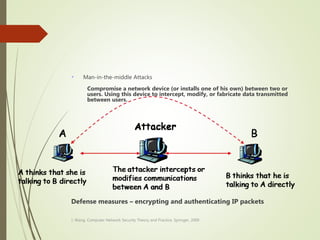
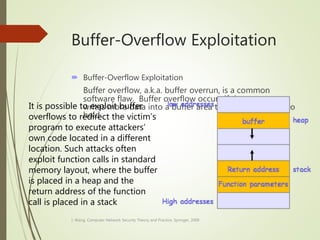
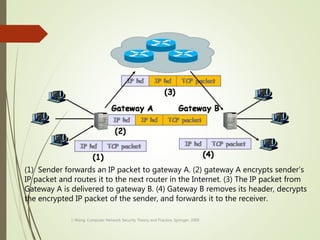
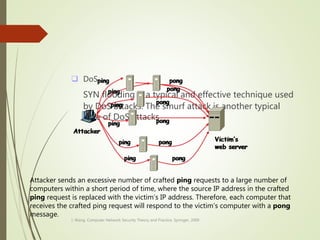
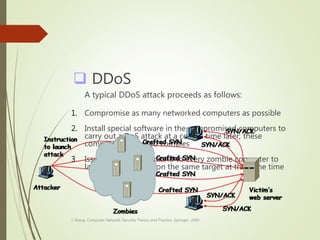
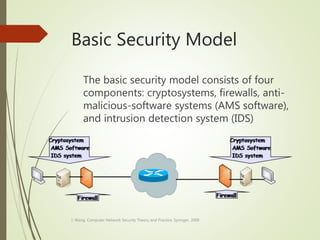
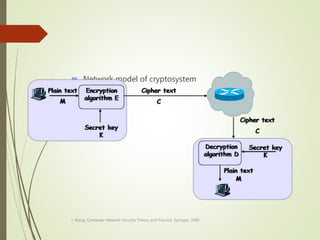
This document discusses network security and defines key concepts. It explains that security aims to protect confidentiality, integrity, and availability of information. The main pillars of security are the CIA triangle of confidentiality, integrity, and availability. Vulnerabilities are weaknesses that can be exploited by threats to carry out attacks, which aim to intercept, interrupt, modify or fabricate information. Common attacks include eavesdropping, cryptanalysis, password pilfering through guessing, social engineering, dictionary attacks and password sniffing. Controls work to reduce vulnerabilities and block threats to prevent harm.