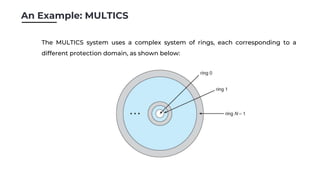
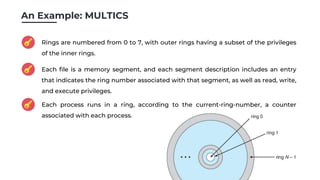
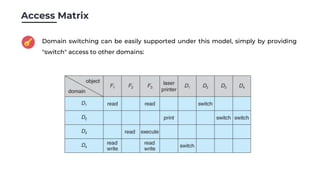
Protection in operating systems aims to control access to system resources and prevent misuse. Key goals are to ensure resources are only used according to policies and that errors cause minimal damage. Protection is achieved through principles like least privilege and access controls. For example, the MULTICS system used rings to separate privileges, with outer rings having fewer privileges than inner rings. Access is represented by an access matrix where rows are domains and columns are resources, with entries indicating access permissions. Role-based access control also follows least privilege by assigning privileges based on roles. Revoking access raises questions about when and how it takes effect, whether it applies selectively or generally, and if it is temporary or permanent. Protection is crucial as systems have become more complex