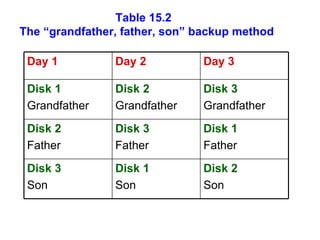
The document discusses various threats to information systems and the need for controls to protect systems. It describes common threats like accidents, natural disasters, sabotage, theft, and unauthorized access. It then discusses different strategies for information security controls, including containment, deterrence, obfuscation, and recovery. It also outlines specific types of controls like physical, biometric, telecommunications, failure, and auditing controls. Finally, it discusses techniques for controlling information systems, such as security policies, passwords, encryption, procedures, user validation, and backup protocols.