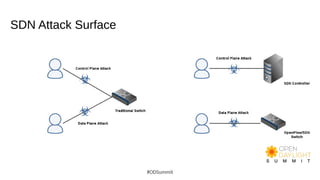
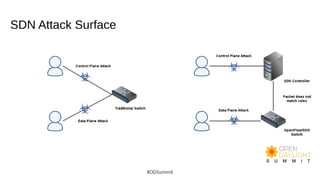
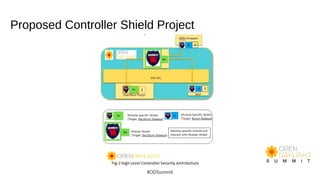
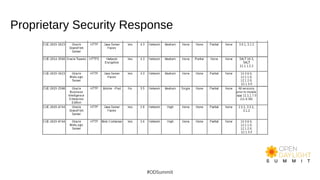
The document discusses building world-class security response and secure development processes for OpenDaylight. It outlines the SDN attack surface, recent vulnerabilities in OpenDaylight, and defensive technologies. It discusses security response best practices for open source projects and secure engineering best practices. The current status of OpenDaylight security response and engineering is described, along with the vision to improve reactive security response capabilities and implement more proactive security measures like automated checks and security training.