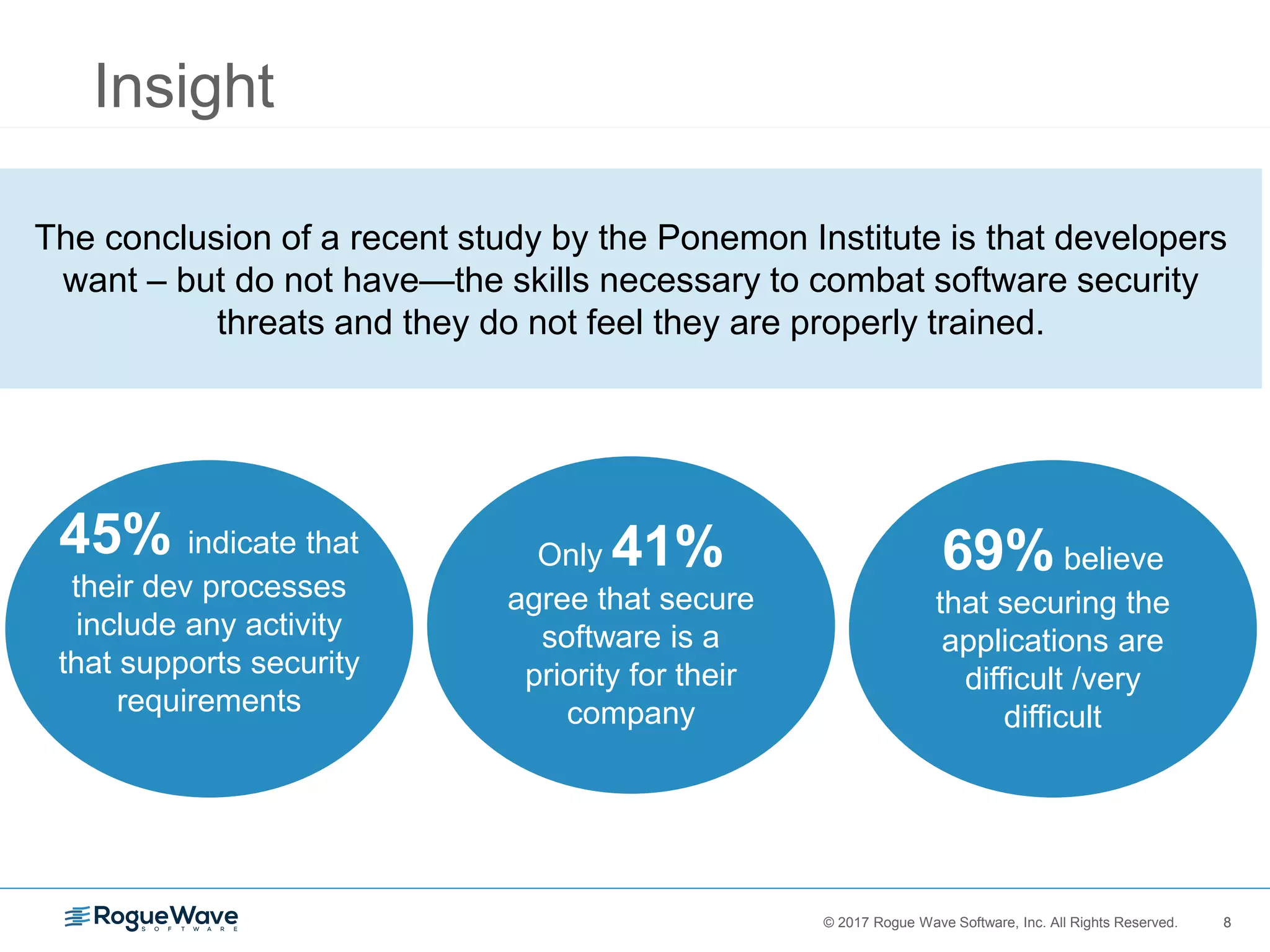
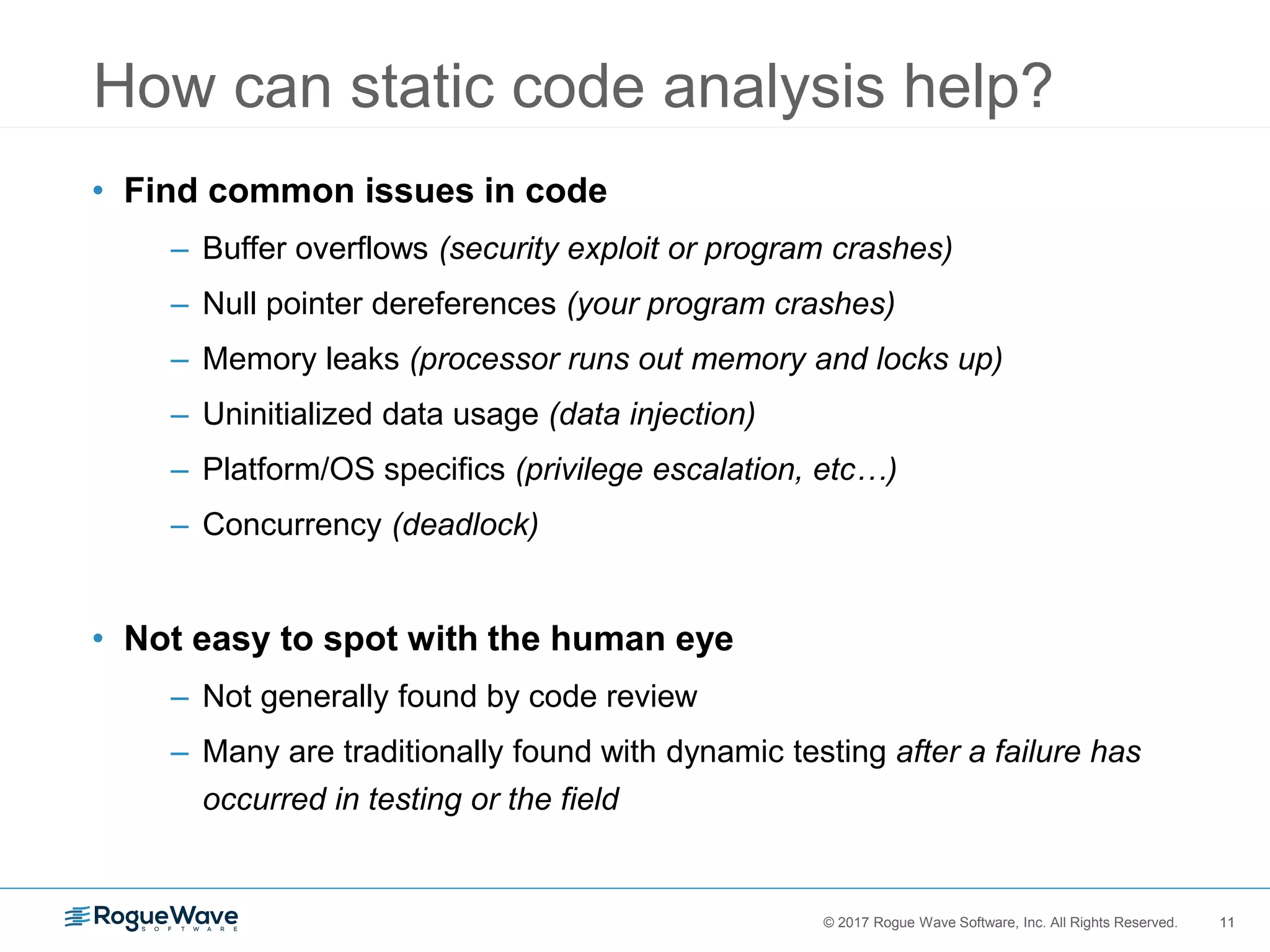
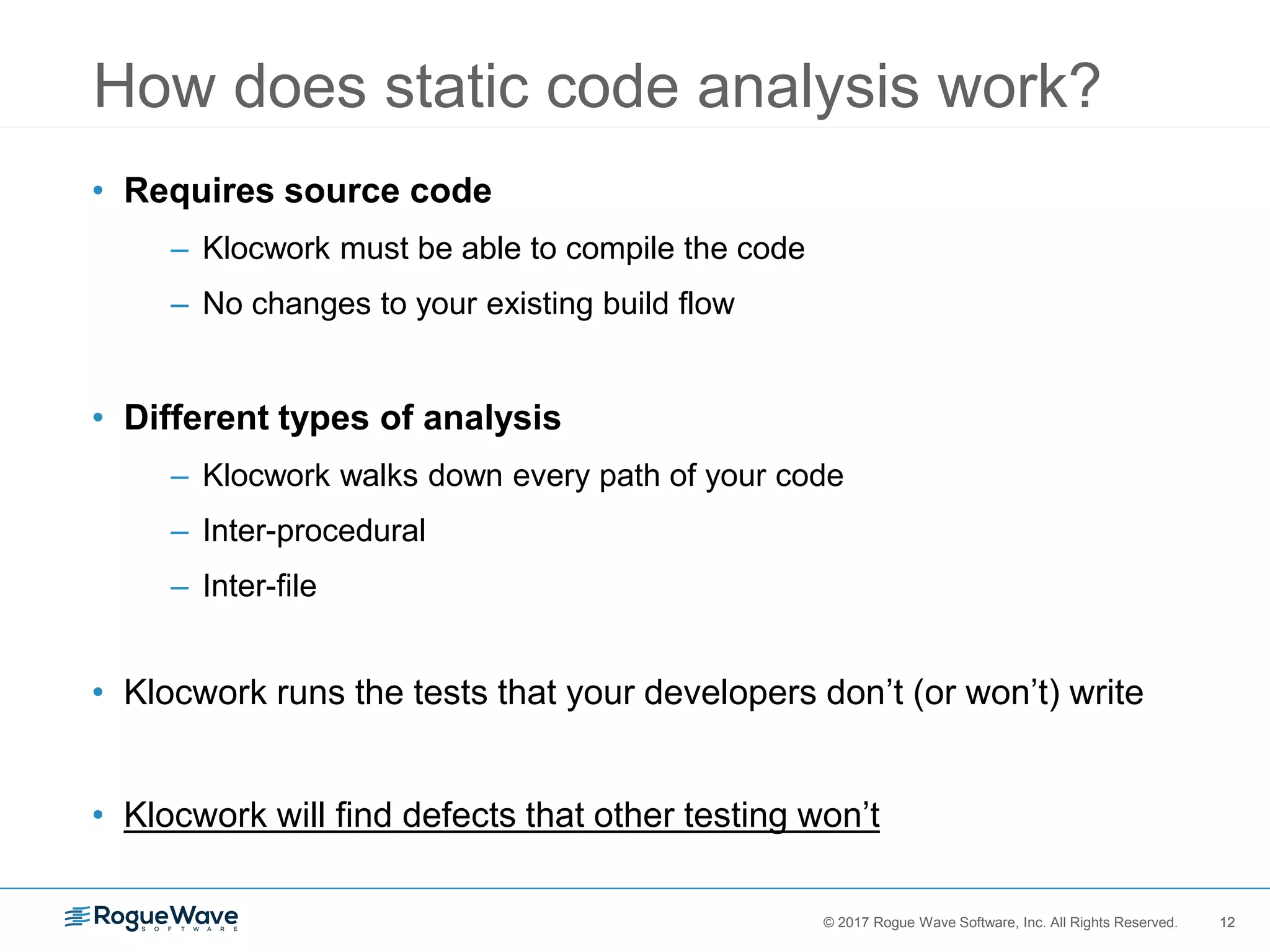
The document discusses the importance of securing embedded systems, highlighting that they are frequent targets for cyber attacks due to their inherent vulnerabilities. It proposes solutions such as implementing safe coding standards, static code analysis, and a zero-tolerance policy for security issues to enhance security. Despite the awareness among developers about security threats, many feel inadequately trained, indicating a necessity for better security education and practices in software development.