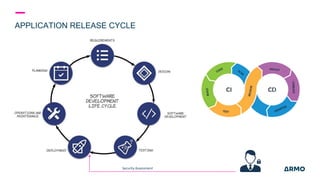
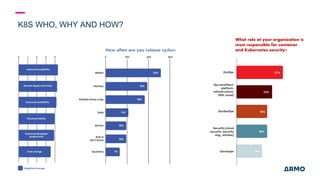
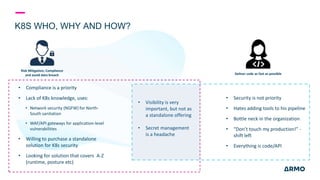
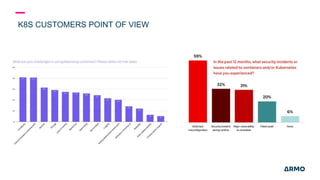
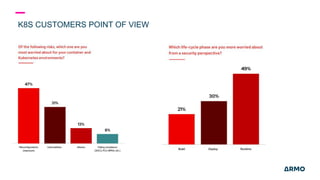
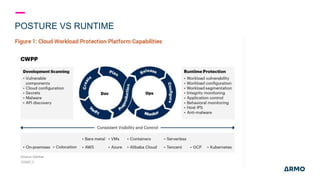
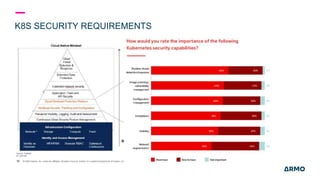
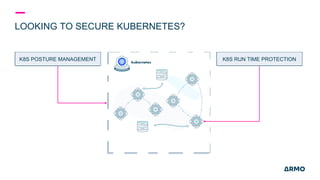
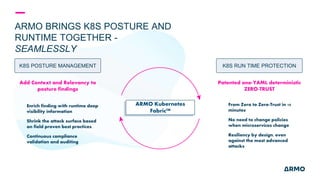
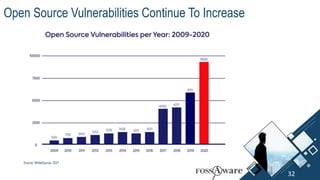
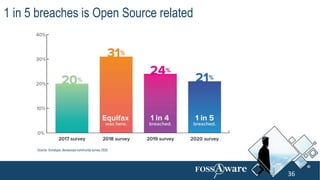
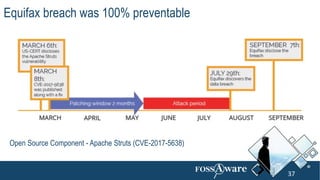
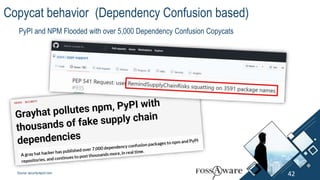
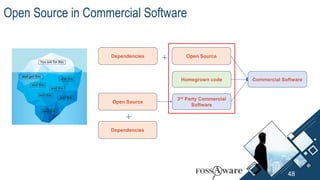
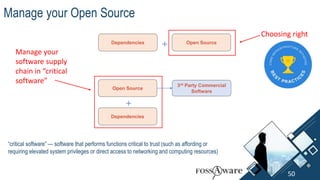
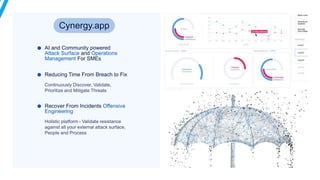
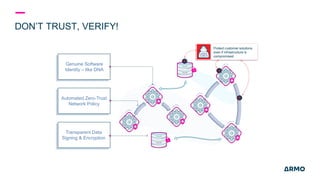
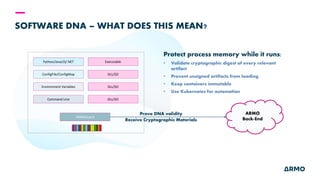
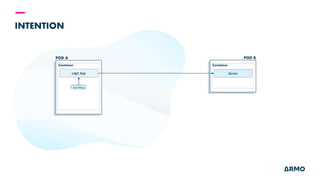
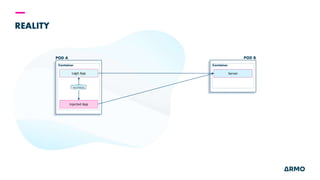
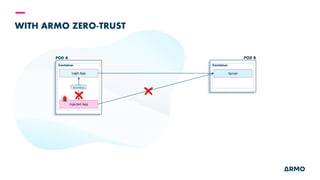
The document discusses Kubernetes (k8s) security, emphasizing the need for both posture and runtime protection in the release cycle to mitigate risks and ensure compliance. Organizations face challenges such as misconfigurations, visibility issues, and threat management, while ARMO offers solutions to improve k8s security by integrating visibility and control throughout the workload. It highlights the importance of managing open-source dependencies due to vulnerabilities, providing guidance on risk management for software supply chains.