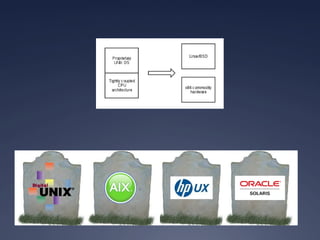
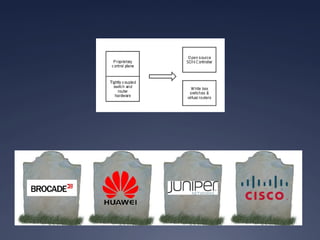
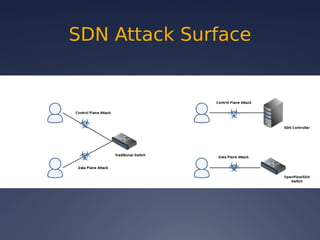
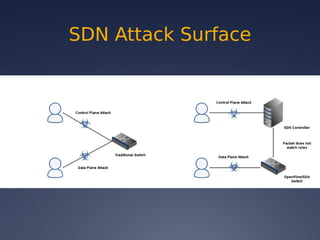
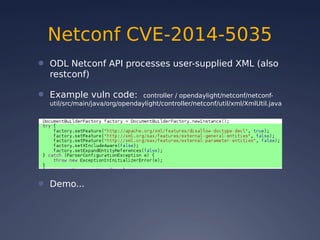
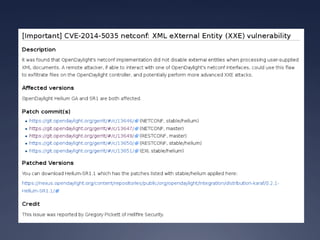
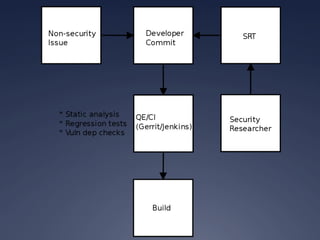
This document provides an overview of software-defined networking (SDN) security. It begins with an introduction to SDN and explains how decoupling the control plane from the data plane creates new attack surfaces. It then discusses recent SDN vulnerabilities in OpenDaylight and ONOS controllers. Defensive technologies like Topoguard and security-mode ONOS are presented. The document concludes with recommendations for secure SDN development practices and outlines the current security status and vision for OpenDaylight.