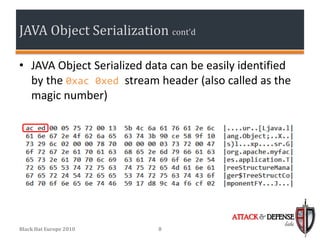
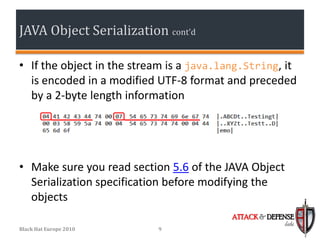
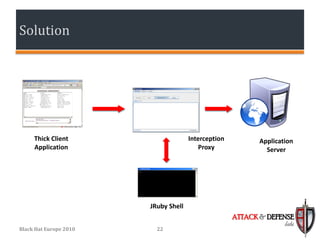
The document discusses techniques for simplifying penetration testing of thick Java clients by modifying serialized Java objects. It covers the basics of Java object serialization and evaluates current challenges and methods used to test Java applications, including modifying raw hex, runtime protocol analysis, and a proposed solution using JRuby. The suggested setup aims to enhance the testing process by facilitating seamless modification of Java objects on-the-fly through a compatible interception proxy.