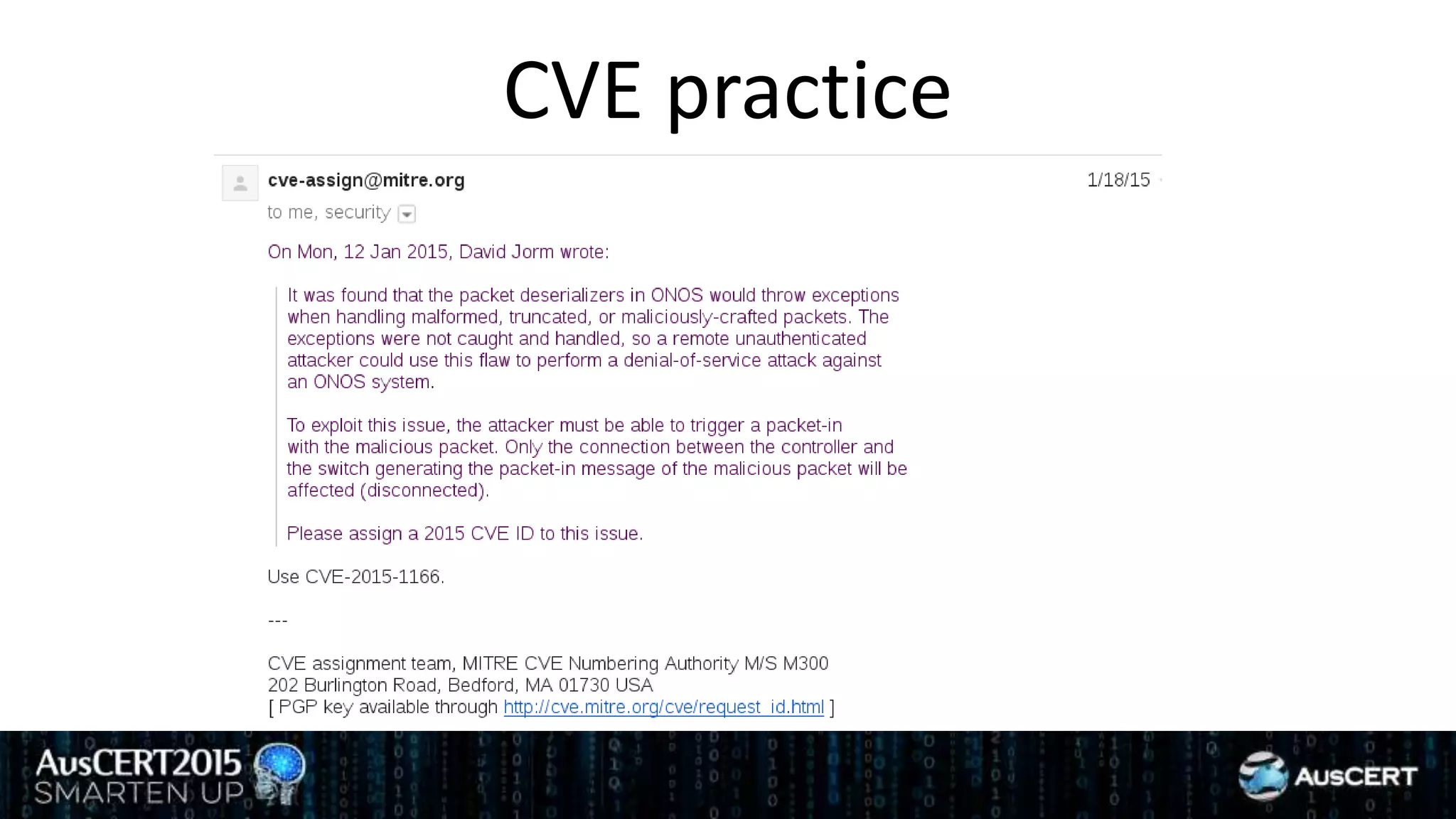
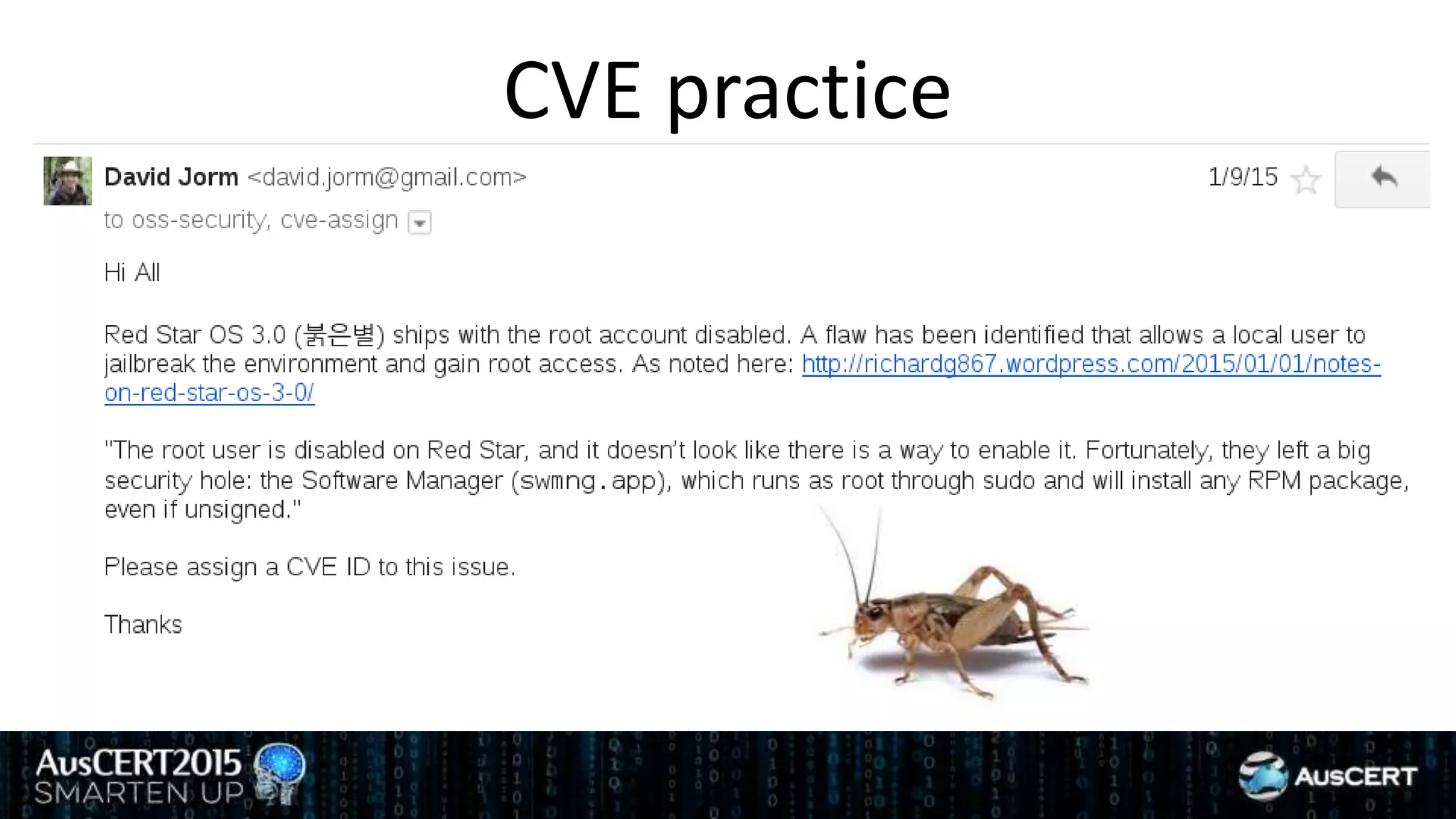
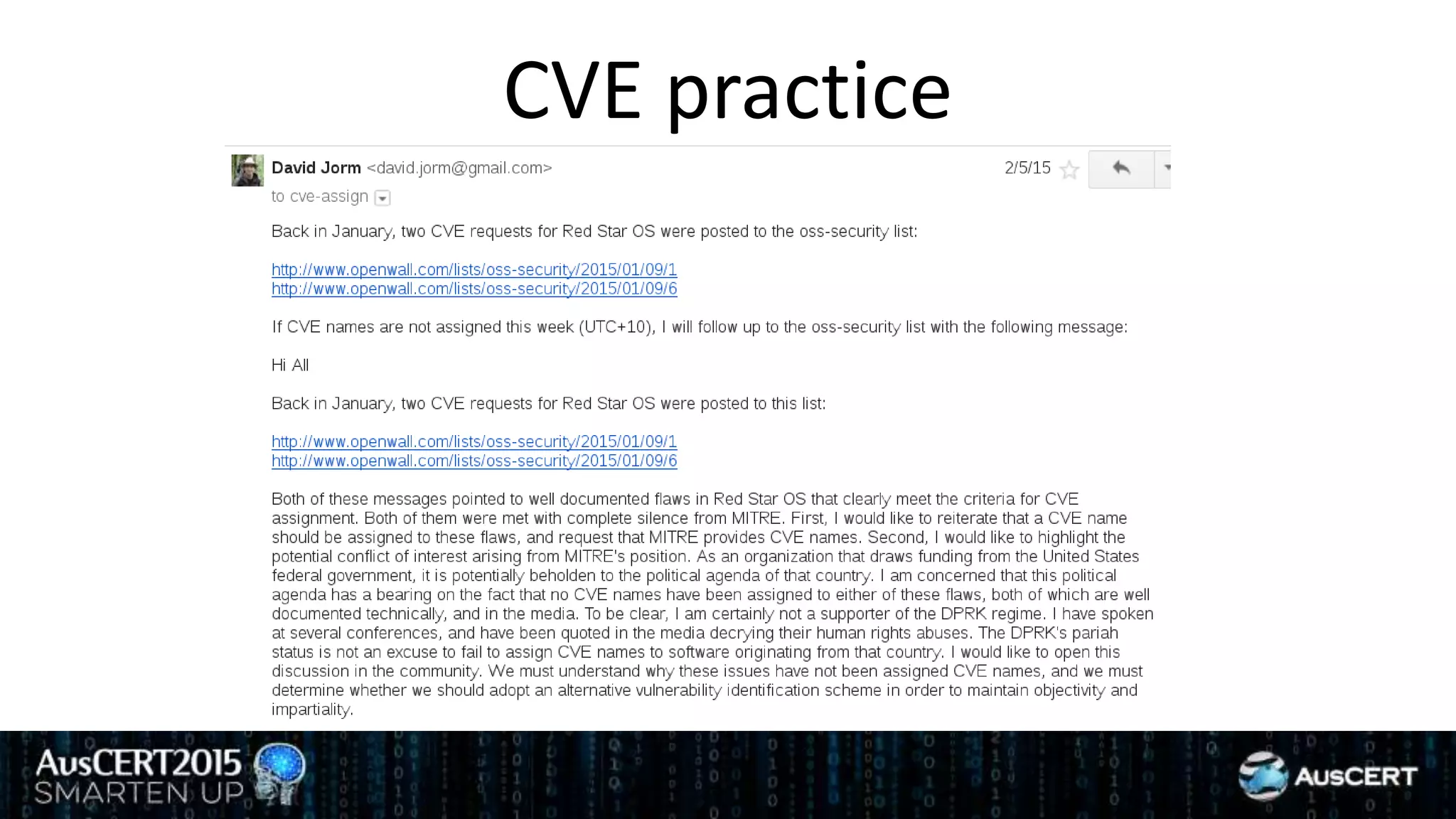
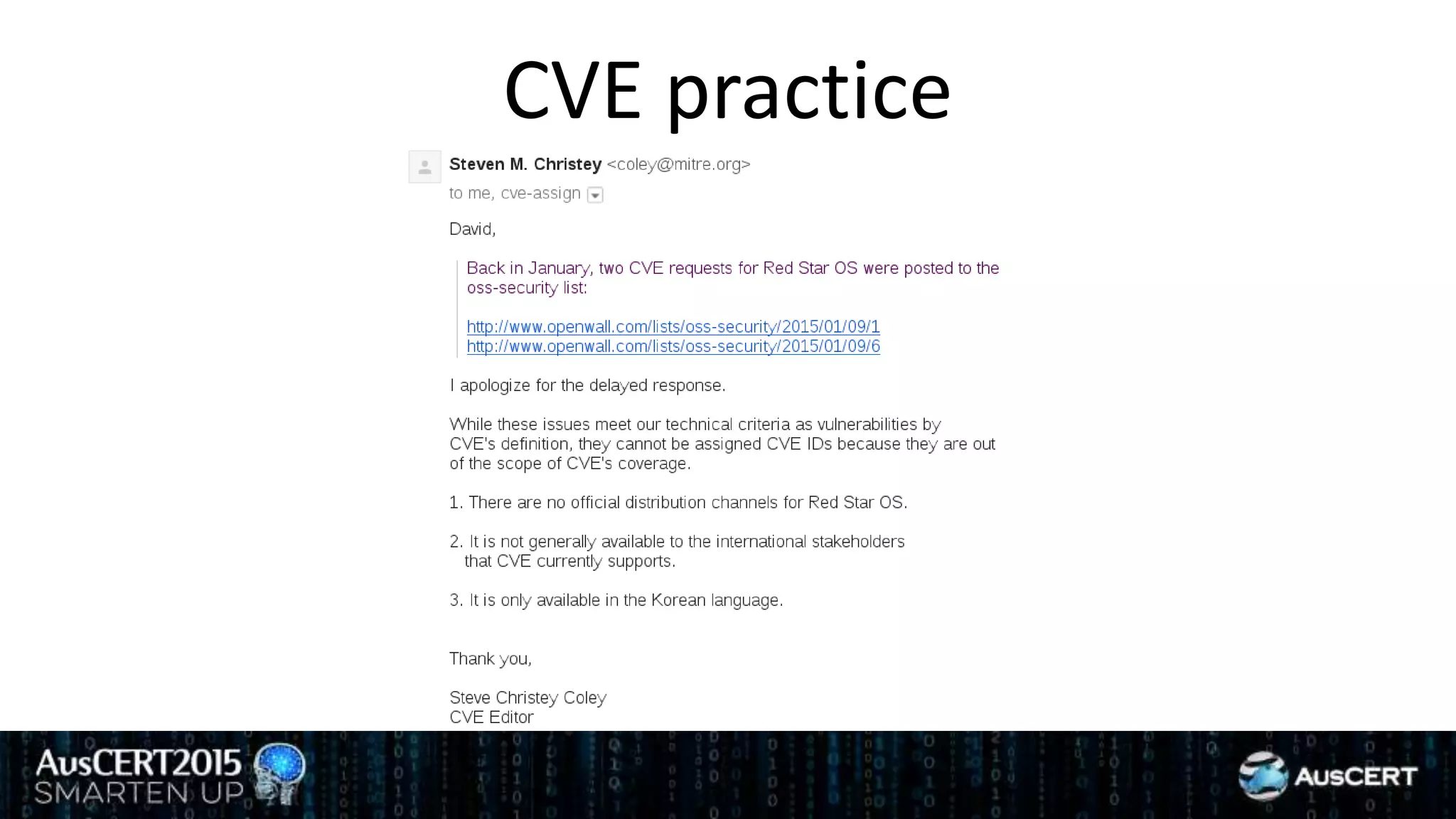
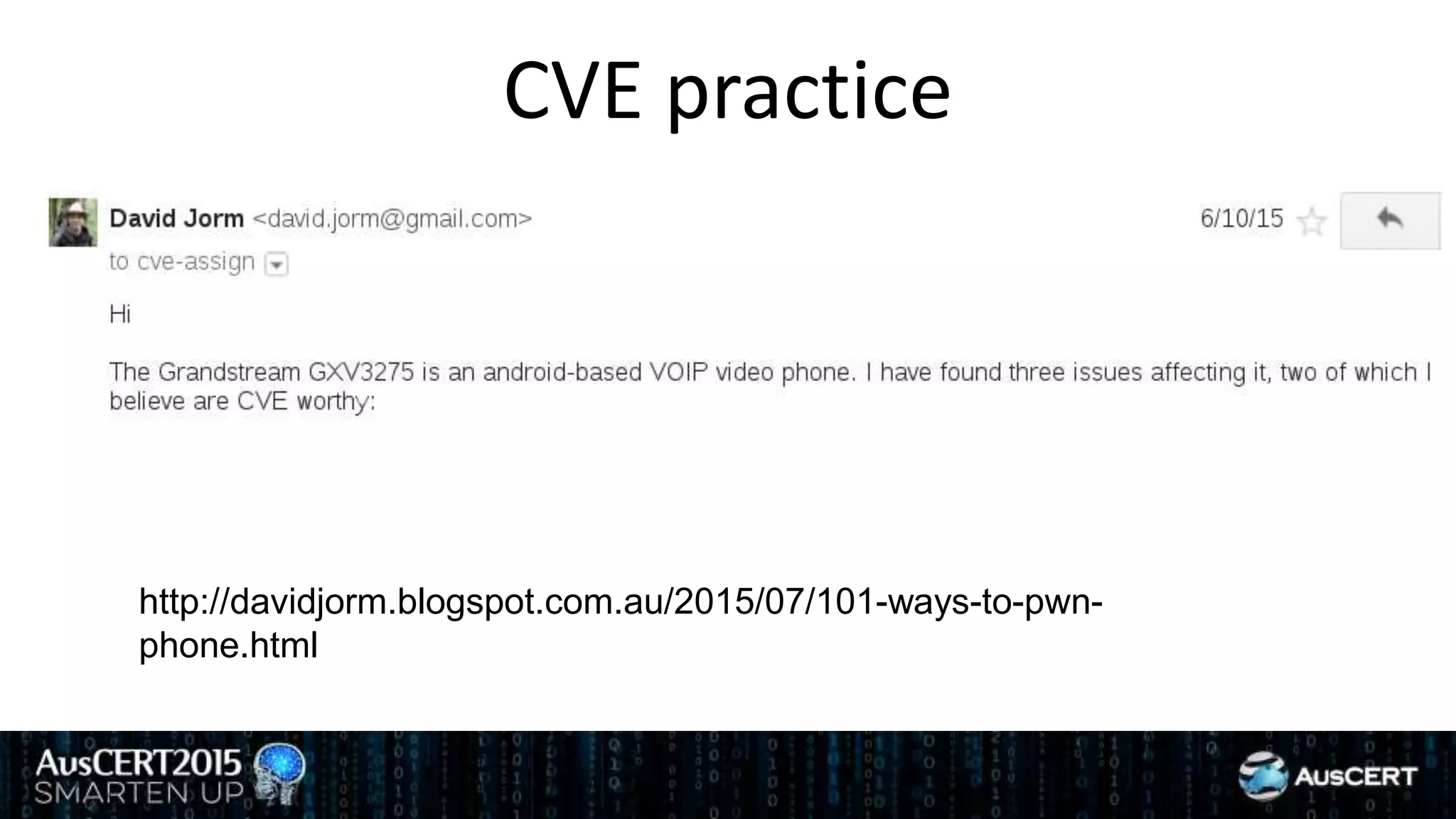
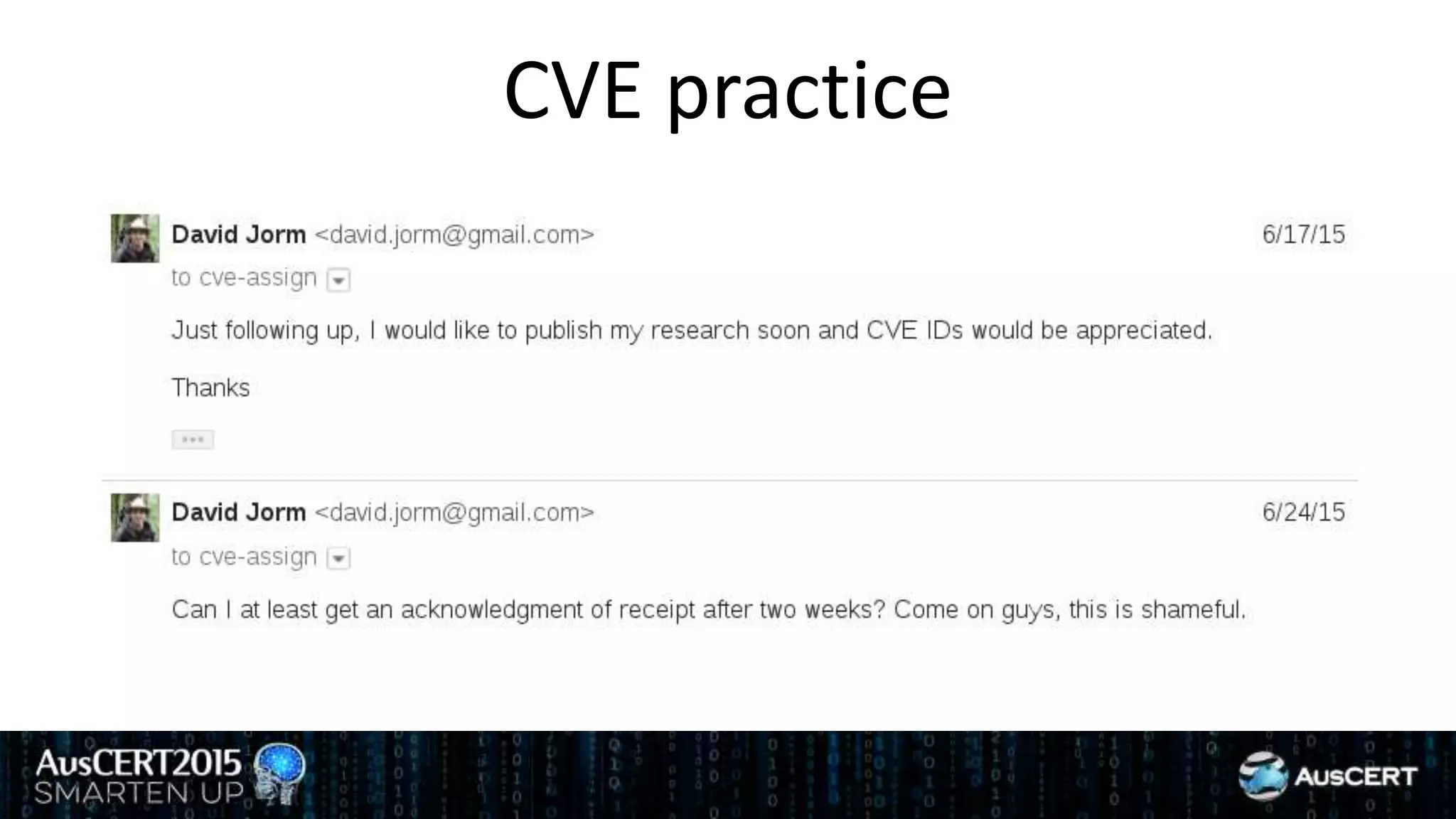
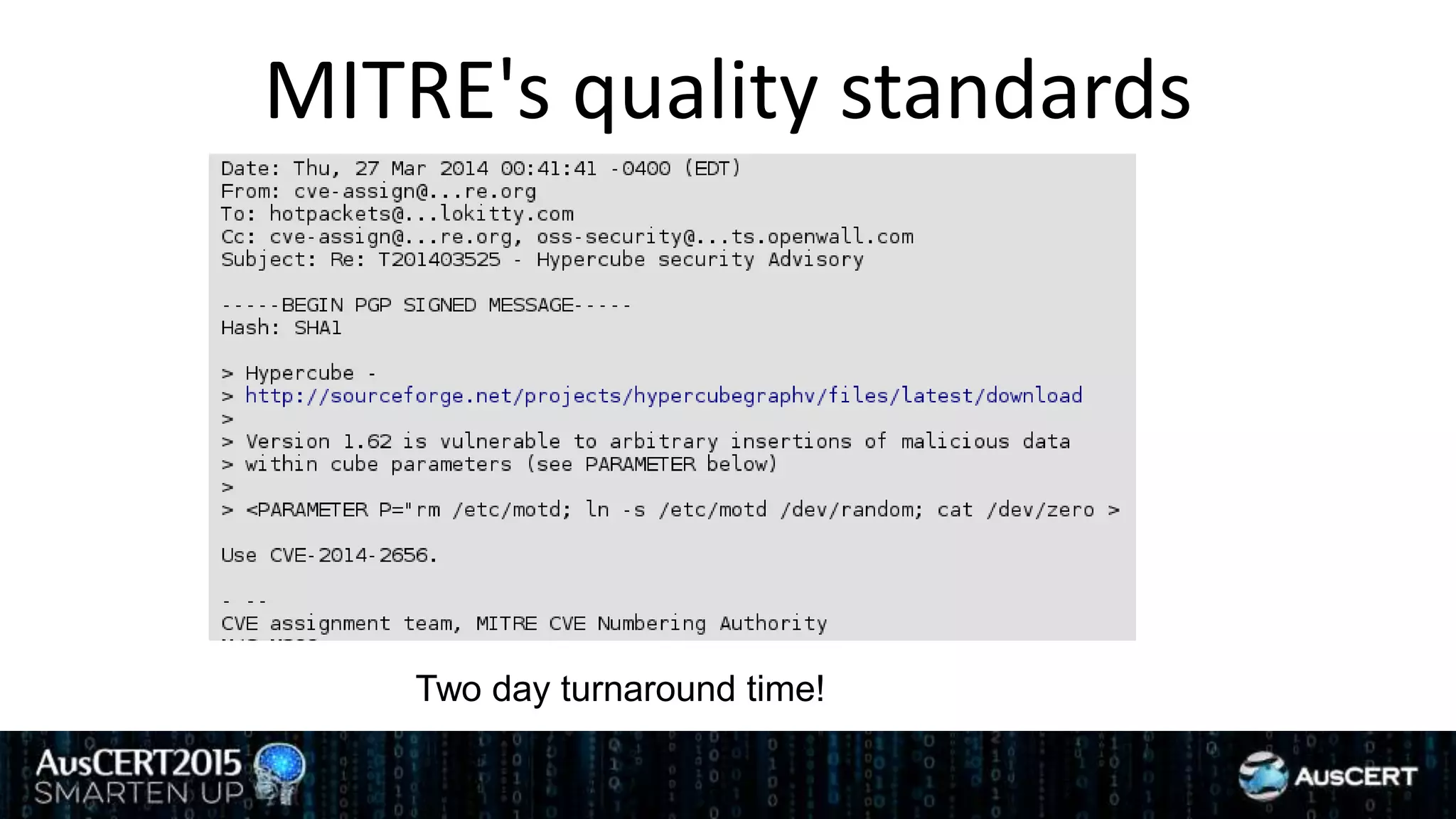
David Jorm discusses the purpose and history of the Common Vulnerabilities and Exposures (CVE) system, developed to provide a standardized identifier for software vulnerabilities. He highlights the growth of CVE since its inception, the challenges related to CVE assignment, and mentions alternatives like Distributed Weakness Filing (DWF). Jorm advocates for community efforts to enhance the adoption of these systems and improve vulnerability naming and identification.